Join Us for Live Online Training on TPRM for Cyber Risk Professionals
Ask questions, gain insights into how to address the challenges of third-party, supply-chain risk.
Join SAFE for a live training session on third party cyber risk management (TPRM), designed to provide you with valuable insights into the lifecycle, methods, and industry trends of TPRM, as well as to address common challenges and solutions.
Live Training Session: Understanding TPRM for Cyber Risk Professionals
Date: Thursday, July 18th
Time: 11:30AM-12:30PM EDT
Led by: Vince Dasta, Senior Partner, Risk Strategy, and Mark McKinney, Risk Advisor, TPRM Consultant, SAFE
Register now!
As Forrester reports:
“TPRM is shifting from a nice-to-have tool for compliance checks and onboarding automation to a must-have technology for leveraging the benefits of third-party relationships without creating undue risk to the organization, complete with new AI-enabled use cases and the ability to support the entire lifecycle of a third-party relationship.”
Recent cyber incidents drive the point home: The ransomware attack that shut down UnitedHealth Group’s Change Healthcare, the principal payments platform for medical insurance in the US, quickly drove many healthcare providers to the brink of financial failure.
At the same time, the tools and techniques of cyber risk management for third party partners are badly in need of a refresh. The bottom line: Every organization needs to reassess its approach to TPRM. Our training session will give you a strategy and action steps to get going.
Agenda:
Understanding TPRM
–Lifecycle of TPRM
The maturity curve for third party cyber risk management starts with building a minimum awareness by creating a basic directory of vendors.
Next up the curve, organizations begin to demand in contracts that third parties demonstrate ISO or SOC2 compliance – or they may contract for outside-in scans of web-facing controls. Positive steps but they just infer that risk is being managed, not measure risk reduction.
The most mature organizations exercise proactive risk management, starting with cyber risk quantification (CRQ). They apply zero trust practices to treat third-party risk on a par with first-party. They employ continuous monitoring of third parties with an inside-out view.
Register for this live training session now!
Why TPRM Is Broken:
–Identifying the flaws and challenges in current TPRM practices
Examine the most popular methods – and understand why so many sophisticated CISOs and cyber risk managers think their third party risk is basically unmanaged.
For example,
–Cybersecurity ratings. Usually black-box methodologies that are based on data collected from outside-in (external and public) scans. They often are a compliance requirement, even though they do not provide any insight into the third-party’s internal controls. Scores from these services should not be confused with cyber risk quantification (CRQ) which provides insight into a business’ risk exposure, the financial impact of cyber risks and the likelihood of cyber attacks.
–Questionnaires. Often 150-200+ questions that vendors are required to fill out and update, typically on a yearly basis.
The flaw: Questionnaires do not assess the vendors’ control maturity (coverage, capability, and reliability of controls) For example, if a company deploys multi factor authentication on only a few cloud servers, it can truthfully answer “yes” to MFA – when in reality, the coverage of the control is spotty. Questionnaires are essentially check-the-box compliance exercises when enterprises would be better served proactively measuring their third-party risk.
Read the whitepaper: TPRM Program Blueprint: Your Guide for Transforming Third-Party Cyber Risk Management.
FAIR Institute Research on TPRM
The FAIR Institute is the leading organization for the study and advancement of quantitative measurement of cyber and operational risk with Factor Analysis of Information Risk (FAIR), the international standard for risk analysis recommended by the National Institute of Standards and Technology. SAFE is Technical Advisor to the FAIR Institute.
The Institute recently added to the FAIR standards the FAIR Third-Party Assessment Model (FAIR-TAM). The standard is built on some foundational concepts:
- Risk-based prioritization. Run a FAIR assessment of the risk the vendor poses to your organization as a first party.
- Comprehensive, continuous monitoring. Instead of questionnaires or outside-in scans, use inside-out telemetry from first and third parties as they access your network, reporting on a continuous basis through automation.
- Actionable Mitigations. Treat third parties as part of your attack surface. Apply Zero Trust Principles to TPRM.
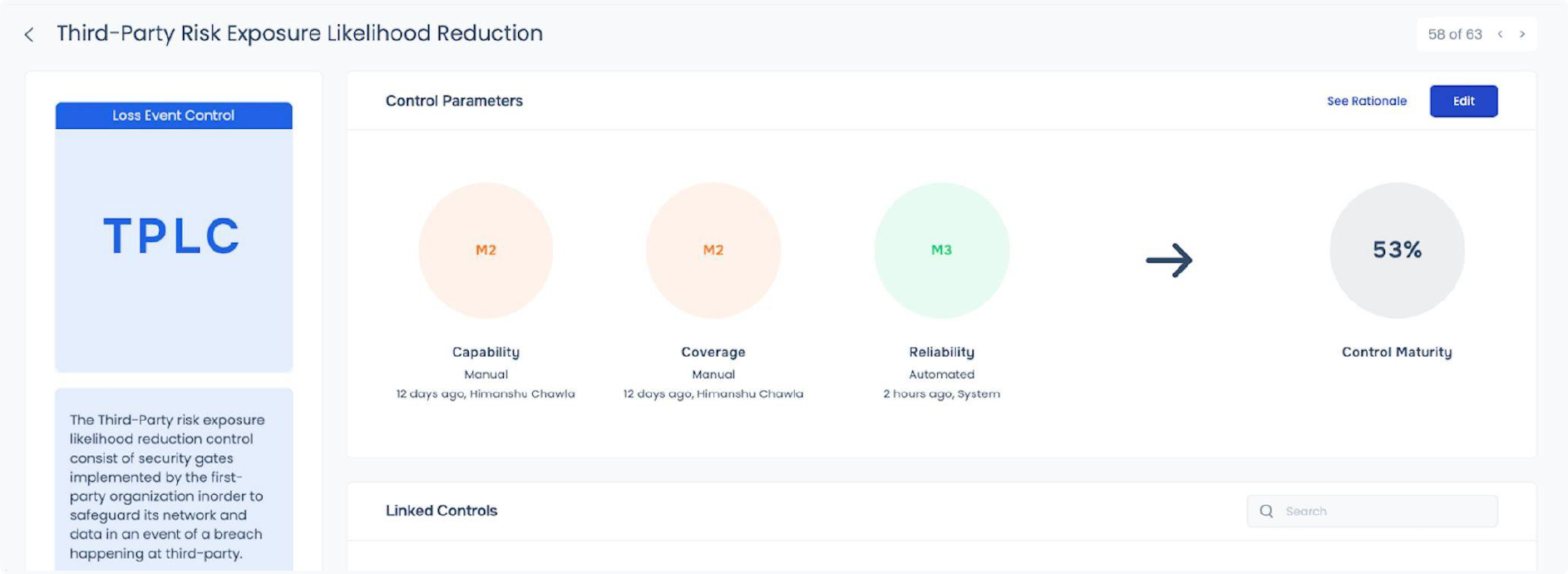
TPRM on SAFE’s platform
SAFE One Platform Preview:
See how our quantitative cyber risk analysis and management platform operationalizes FAIR-TAM with SAFE TPRM – and solves for the nagging problems of TPRM as it is commonly practiced.
Key features/functionality of the platform:
- Quantification of the financial impact of a third-party-originating risk on a business’s bottom line and the likelihood of the risk causing a successful cyber attack
- Zero trust principles drive SAFE TPRM and provide real-time visibility to an enterprise’s internal resilience controls facing its third parties. SAFE TPRM buckets enterprise controls into third-party likelihood reduction and loss magnitude reduction that equip a business to safeguard itself against potential data breaches
- Continuously consolidated third-party risk data using 100% automated controls telemetry from outside-in scans, questionnaires, and inside-out assessments.
- Simple, swift, and efficient collaboration with supply chain partners using AI-assisted training and onboarding modules. 24×7 support to vendors who have a direct SAFE platform access.
What You’ll Learn
This session will give you a comprehensive understanding of how TPRM can be effectively managed and improved. You’ll gain insights into the latest research from the FAIR Institute and see how our SAFE One platform can help automate and enhance your TPRM processes.
How to Register:
Don’t miss this opportunity to enhance your TPRM knowledge and skills.
Click the link below to register:
We look forward to your participation in this informative session!
Live Training Session: Understanding TPRM for Cyber Risk Professionals
Date: Thursday, July 18th
Time: 11:30AM-12:30PM EDT
Led by: Vince Dasta, Senior Partner, Risk Strategy, and Mark McKinney, Risk Advisor, TPRM Consultant, SAFE
Register now!



