How to Manage Cyber Risk Like an Investment Manager
What if CISOs approached cyber risk with financial discipline and strategic focus?
Cyber risk management is often seen as a technical endeavor: patching vulnerabilities, improving controls, and executing projects to build resilience. While these actions are essential, they are primarily tactical, lacking the strategic foresight required for sustainable, long-term success.
What if CISOs approached cyber risk with the same discipline and strategic focus as investment managers? Investment management provides a compelling model, offering guiding principles that CISOs can adapt to manage cyber risk as a business portfolio.

The 20-Slot Rule: Your Decisions Have Financial Implications
Warren Buffett, one of history’s greatest investors, frequently references the “20-slot rule.” Imagine having a punch card with only 20 slots, each representing a lifetime investment opportunity. Once the slots are filled, no more investments can be made. Buffett’s point is clear: success comes from being focused, selective, and deliberate in your decisions.
If Buffett were advising a CISO, his guidance might echo the following principles:
- Focus on the Fundamentals
- Understand the business
- Build a strong foundation
- Know your tolerances
- Prioritize
- Hire the best and maximize talent
- Continuously inspect and address gaps
- Invest
- Stay aligned with business’ go-to-market goals
- Leverage proven technologies
- Re-balance often – cut losses on ineffective strategies
- Measure ROI consistently against security budgets
This strategic framework aligns cyber risk management with business objectives, enabling CISOs to make impactful, data-driven decisions.
Building a Manageable Cyber Risk Portfolio in Three Steps
A successful cyber risk management program requires a structured, measurable approach. Here’s a three-step plan to guide CISOs:
- Risk Identification
- Risk Mitigation (Burn Down)
- Risk Investment (Buy Down)
Your KPIs should tell the story of your progress on each step.
1. Risk Identification
Key Question:
>>How much risk with tangible impact has been discovered, quantified and communicated?
Risk identification starts with a detailed understanding of your business structure—by line of business, critical applications, product lines, locations, etc. For each entity, define risk scenarios with identifiable likelihoods and impacts. Use a reliable risk-analysis model to quantify and prioritize risks.
How SAFE Can Help
The SAFE One platform facilitates scenario-based reporting aligned with business structures. Leveraging the FAIR model (the international standard for cyber risk quantification), it provides dashboards that frame security investments in financial terms, translating technical data into business language.
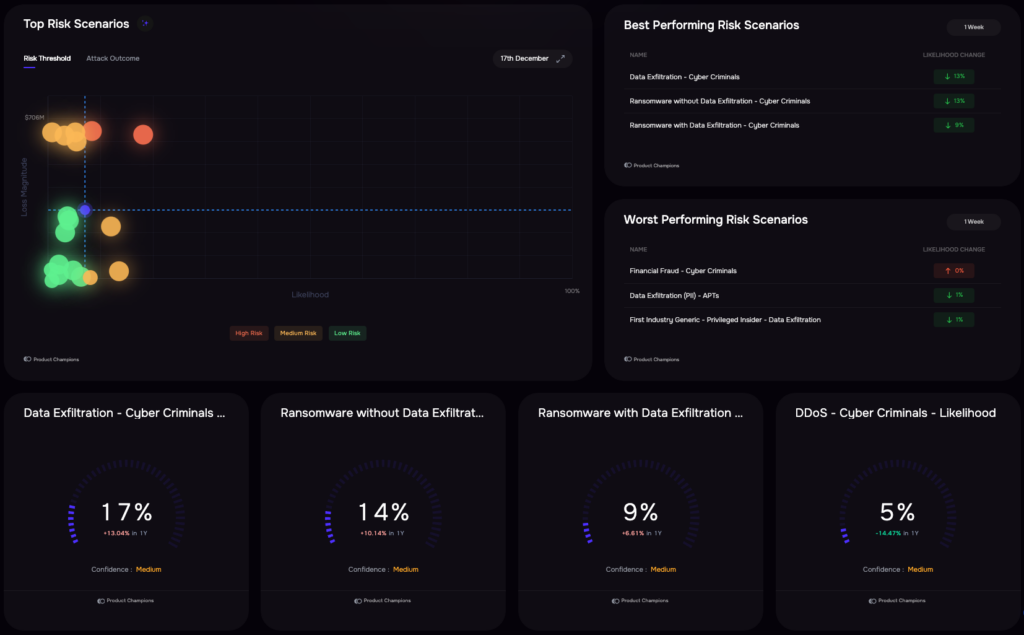
Risk Visibility: Top Risk Dashboard
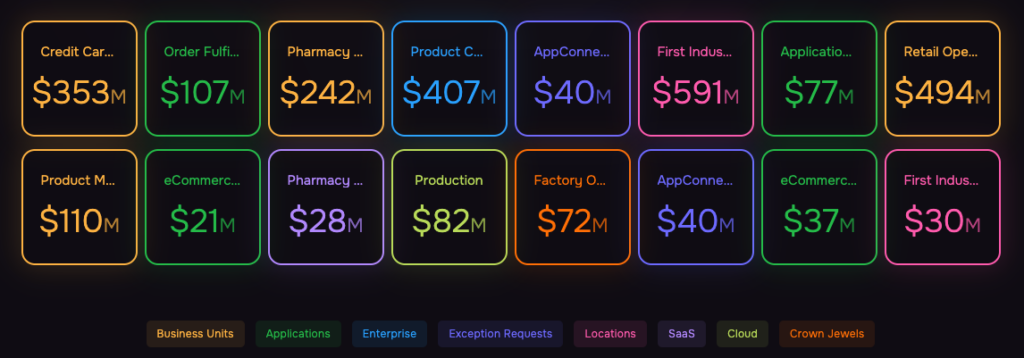
Risk Impact: Aggregated $ Risk
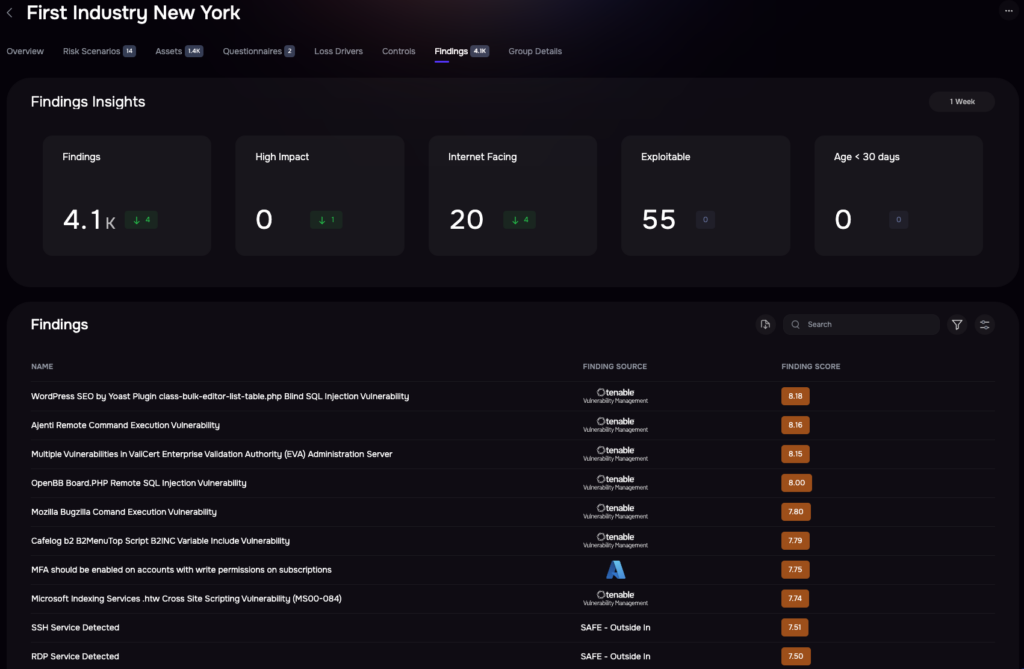
Risk Defensibility: Live Real-time Findings Telemetry
2. Risk Mitigation (Burn Down)
Key Questions:
>>How has risk evolved based on recent actions?
>>Are we improving or regressing?
>>If regressing, what factors are driving the change?
An effective “20-slot” strategy relies on continuous assessment of progress, driven by real-time visibility into risk metrics and trends.
How SAFE Helps
SAFE One’s Control Center offers live updates on your organization’s cyber posture, enabling teams to track progress and tackle security findings collaboratively. Features like the “See What Changed” functionality and Environmental Shifts Display reveal how and why specific risks have changed over time, helping identify drivers of improvement or regression — similar to that of an Investment Manager tracking the portfolio against the S&P 500 index and reacting to those changes.
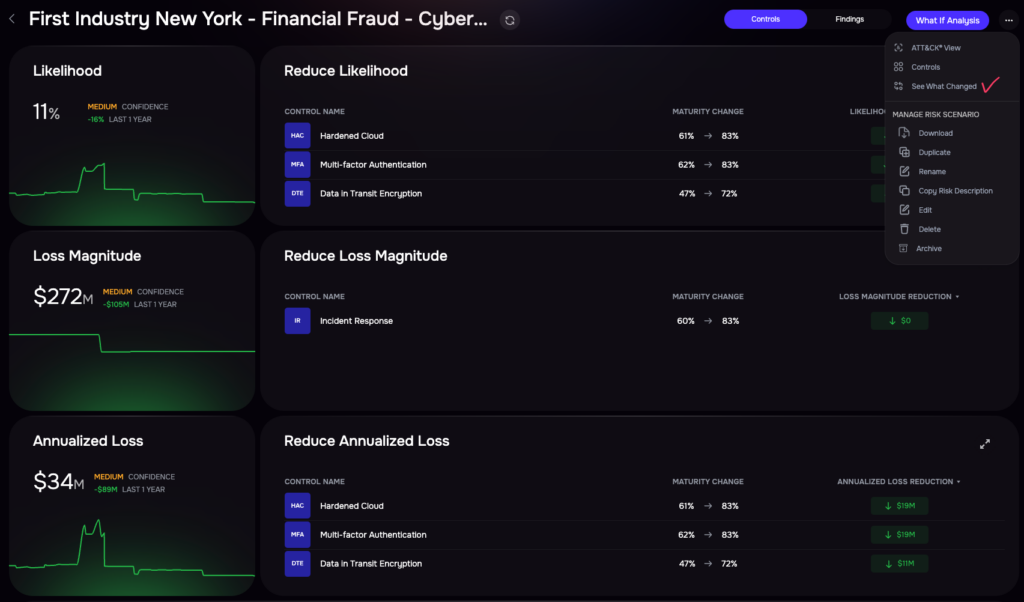
Risk Profile Investigation
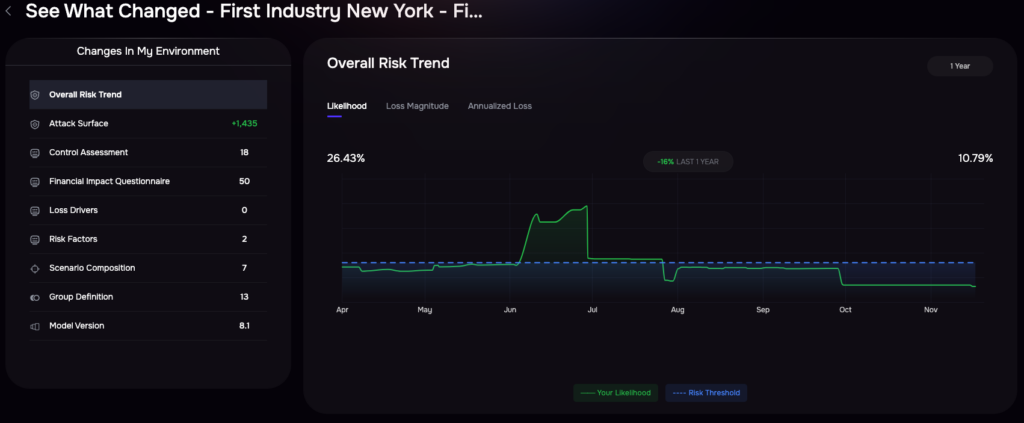
Change in Risk Profile over X Period
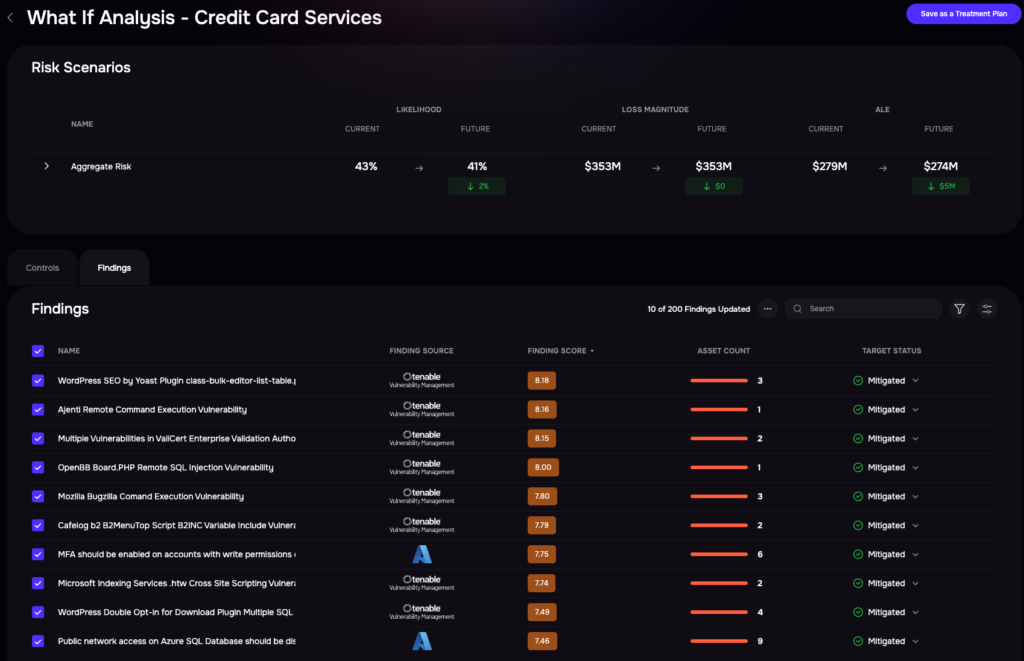
Risk Mitigation Forecasting
3. Risk Investment (Buy Down)
Key Questions:
>>How can I allocate security resources most effectively?
>>Which investments offer the highest ROI?
>>If I invest, would the ROI be worthwhile?
>>Are there underperforming areas (or tech debt) that need rebalancing?
Justifying a cybersecurity budget is a perennial challenge. It requires a quantitative, risk-based approach that adapts to the evolving cyber landscape.
How SAFE Helps
SAFE One enables evaluation of alternative risk treatment plans, assessing their impact on likelihood and loss magnitude while factoring in costs. Using FAIR-CAM (Controls Analytics Model), the platform tracks control performance in real-time, helping prioritize investments with the greatest impact.
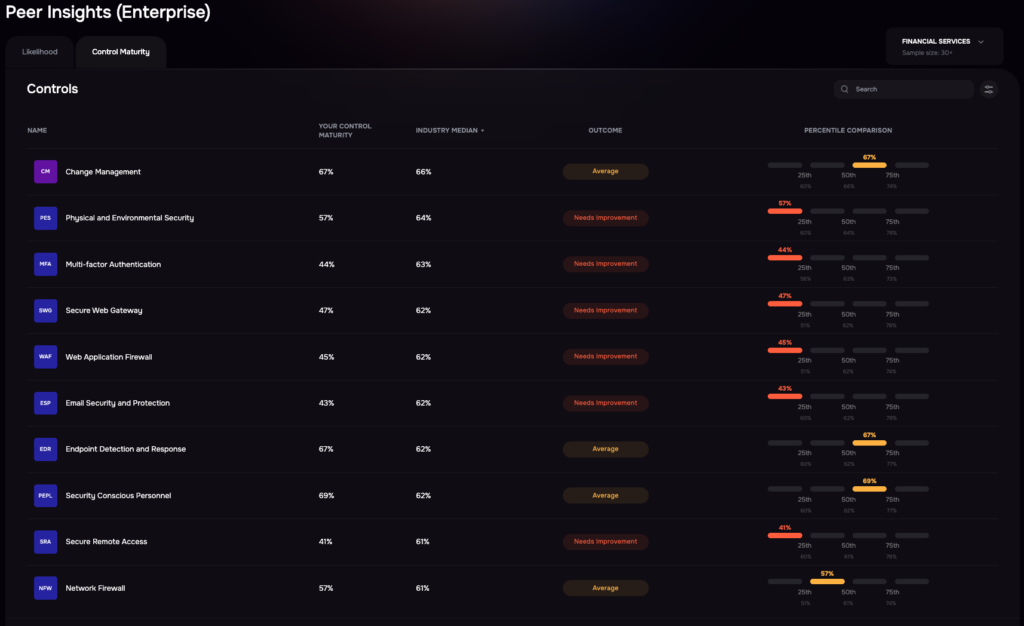
Investing based on Industry Trends: Benchmarks
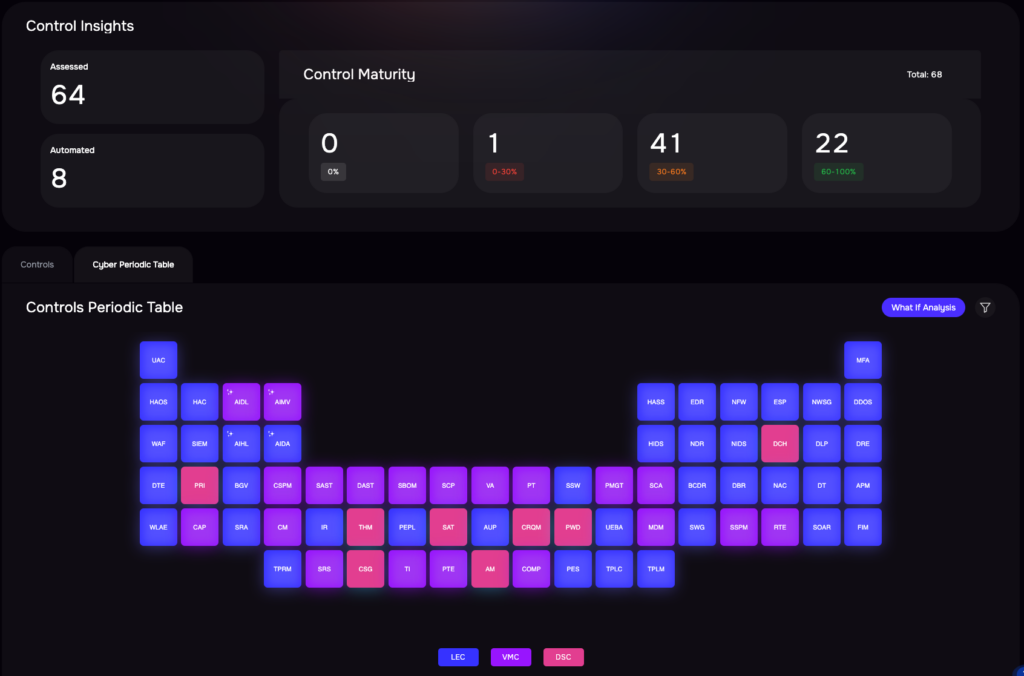
Control Maturity Assessment
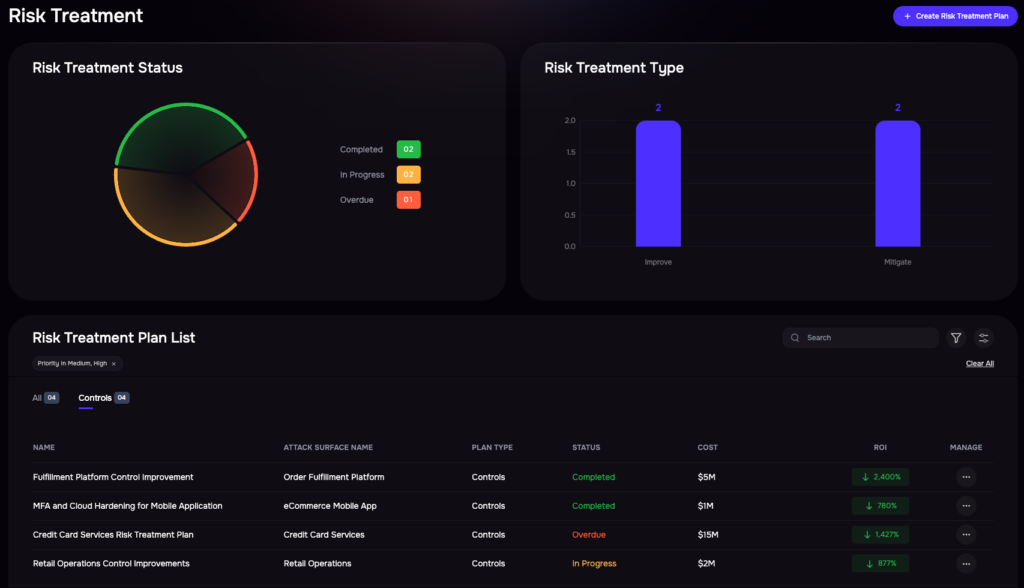
Investment Tracking: All Initiatives & Projects
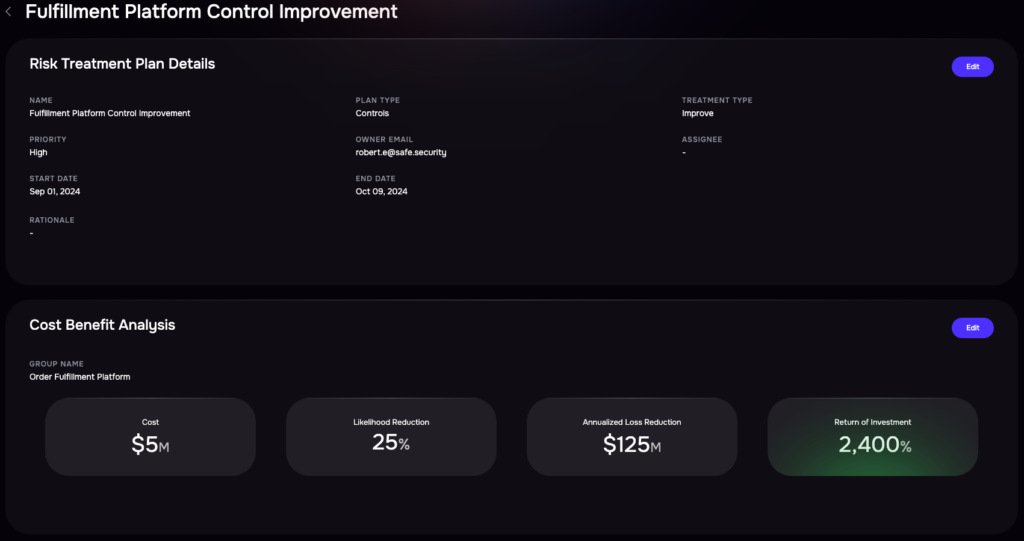
ROI Analysis of all Investments: Current + Planned
Conclusion
Managing cyber risk like an investment portfolio demands a shift from tactical execution to strategic planning. By adopting principles from investment management, CISOs can create a cyber risk program that is effective, measurable, and aligned with business objectives.
SAFE One provides the tools to execute this vision, helping CISOs optimize their security investments while communicating value in terms the business can understand.



