Navigating the Convergence of Cyber Risk and Business Risk with NIST CSF 2.0 and SAFE One
By Resha Chheda

In the wake of high-profile data breaches and an expanding digital threat landscape, the National Institute of Standards and Technology (NIST) has updated its cyber security framework – NIST CSF 2.0 – signaling a paradigm shift that recognizes cyber risk as not just a tech issue, but a core business risk.
NIST CSF 2.0’s Proactive Stance With The New ‘Govern’ Function
NIST CSF 2.0 isn’t just about preventing breaches – it’s about understanding cyber risk in the same nuanced terms as other strategic enterprise risks such as financial risk. This revision introduces a significant ad dition in the form of the new “Govern” function. This update reflects NIST’s commitment to enhancing cybersecurity practices across organizations of all sizes and industries. The inclusion of the “Govern” function within the framework’s core functions, alongside Identify, Protect, Detect, Respond, and Recover, underscores the need for a more strategic, integrated approach to cybersecurity, one that is commensurate with the business’s overall risk posture.
Importance of ‘Govern’ Function
The Govern function provides context that helps organizations establish and monitor their cybersecurity risk management, strategy, expectations, and policy. NIST describes the Govern function as “cross-cutting,” and it’s designed to help security teams prioritize the outcomes outlined in the other five functions.
In essence, the govern function elevates cybersecurity risk to a board-level, whole-of-business concern, aligning with the current trends in corporate governance. This movement is reflected in the NACD Director’s Handbook on Cyber-Risk Oversight and recent regulations, including the Securities and Exchange Commission’s requirements for disclosing practices and processes related to cyber risk management. This shift underscores the increasing recognition of cybersecurity as a critical aspect of overall business operations, prompting organizations to integrate robust cyber risk management into their strategic decision-making processes.
Key Updates Include:
1. Understanding and Assessing Specific Cybersecurity Risks
The GOVERN function mandates a detailed understanding and assessment of an organization’s specific cybersecurity risk requirements. This involves not just standard risk assessments but a thorough comprehension of the tailored cybersecurity strategy that the enterprise needs to create based on unique objectives and environmental risks.
2. Tailoring Risk-based Strategy
Developing a robust, risk-based strategy tailored to each enterprise’s objectives and the actual threat environment is crucial. This form of strategy does not flourish in isolation but through continual interaction and adaptation to the evolving cyber landscape.
3. Continuous Monitoring of Third-Party Cyber Risks
Perhaps most crucial in an age where network security is only as strong as its weakest link, the GOVERN function emphasizes the need for detailed and continuous monitoring of third-party cybersecurity risks. Integrating first and third party cyber risk management ensures a holistic approach to cybersecurity strategy.
This updated framework recognizes that effective cyber risk management requires the ability to anticipate, detect, respond to, and recover from security incidents.
SAFE One: Your Turn-Key Solution For Implementing NIST Cybersecurity Framework 2.0
SAFE offers an AI-powered platform that unifies first-party and Third-Party Risk Management. By consolidating diverse cyber signals into a single view, SAFE provides organizations with a comprehensive understanding of enterprise security risk. This enables effective measurement, reduction, and tracking of cyber risk over time. With its real-time analytics and comprehensive data insights, SAFE enables organizations to truly understand their cybersecurity posture and align it with business risks.
Our key capabilities include:
Automated, Continuous, Cyber Risk Management Process
SAFE One’s AI-driven platform automates the risk management process, streamlining workflow and reducing the burden of manual labor on cybersecurity personnel. SAFE offers a real-time unified risk view, pinpointing top risks across your entire attack surface. This insight helps security leaders prioritize critical risk scenarios and track progress over time.
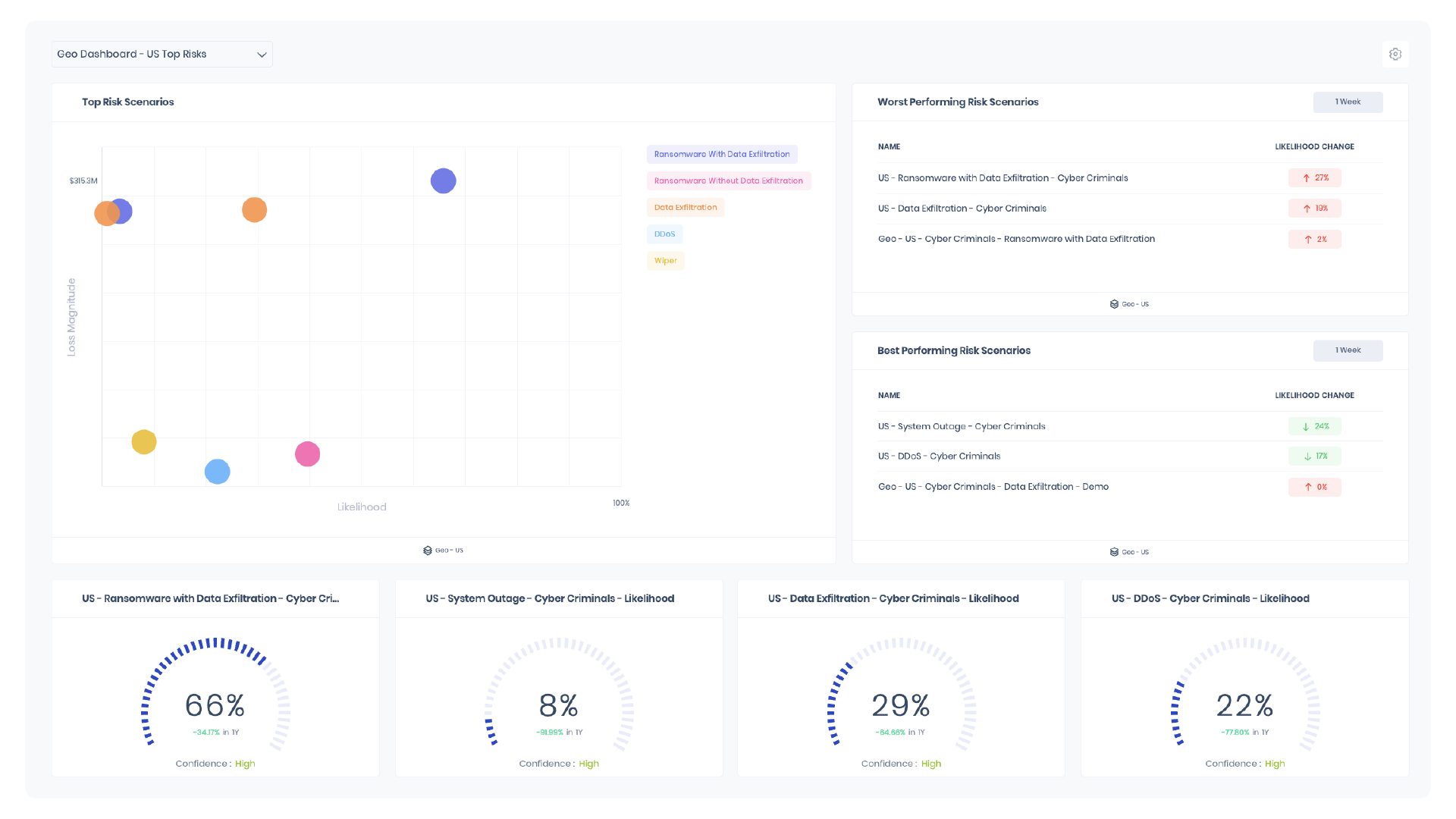
SAFE One supports 100+ integrations and can analyze SaaS solutions out of the box. By consolidating diverse cyber signals into a single view, SAFE provides organizations with a comprehensive understanding of enterprise security risk. SAFE also supports a marketplace of questionnaires to enable context such as industry and geography specific to your business such as NIST CSF and ISO. This automation arm allows for more efficient risk identification, analysis, and response—a core tenet of NIST’s vision for cybersecurity efficiency.

By eliminating the need of manual analysis, CISOs can divert their efforts toward high-value tasks that directly contribute to the organization’s strategic and tactical objectives. This resonates deeply with the NIST CSF 2.0 framework’s directive to prioritize efforts and resources effectively, ensuring they align with the business’s overarching risk management strategy.
Unifying Cyber Risk Visibility Across All Attack Surfaces Including Third-Party Risk
SAFE’s unifies cyber risk visibility across the entire enterprise attack surface. First-party, third-party, and emerging risks are presented in a consolidated, easy-to-digest format, enabling CISOs to make informed, holistic decisions that resonate with the larger business objectives. This unified visibility aligns perfectly with the NIST CSF 2.0 framework’s ambition to fuse cybersecurity risk management to an organization’s overall strategy. It allows SAFE One users to take decisive control of their risk landscape, translating technical threats into tangible business impacts that can be effectively governed and managed according to the enterprise’s risk appetite.
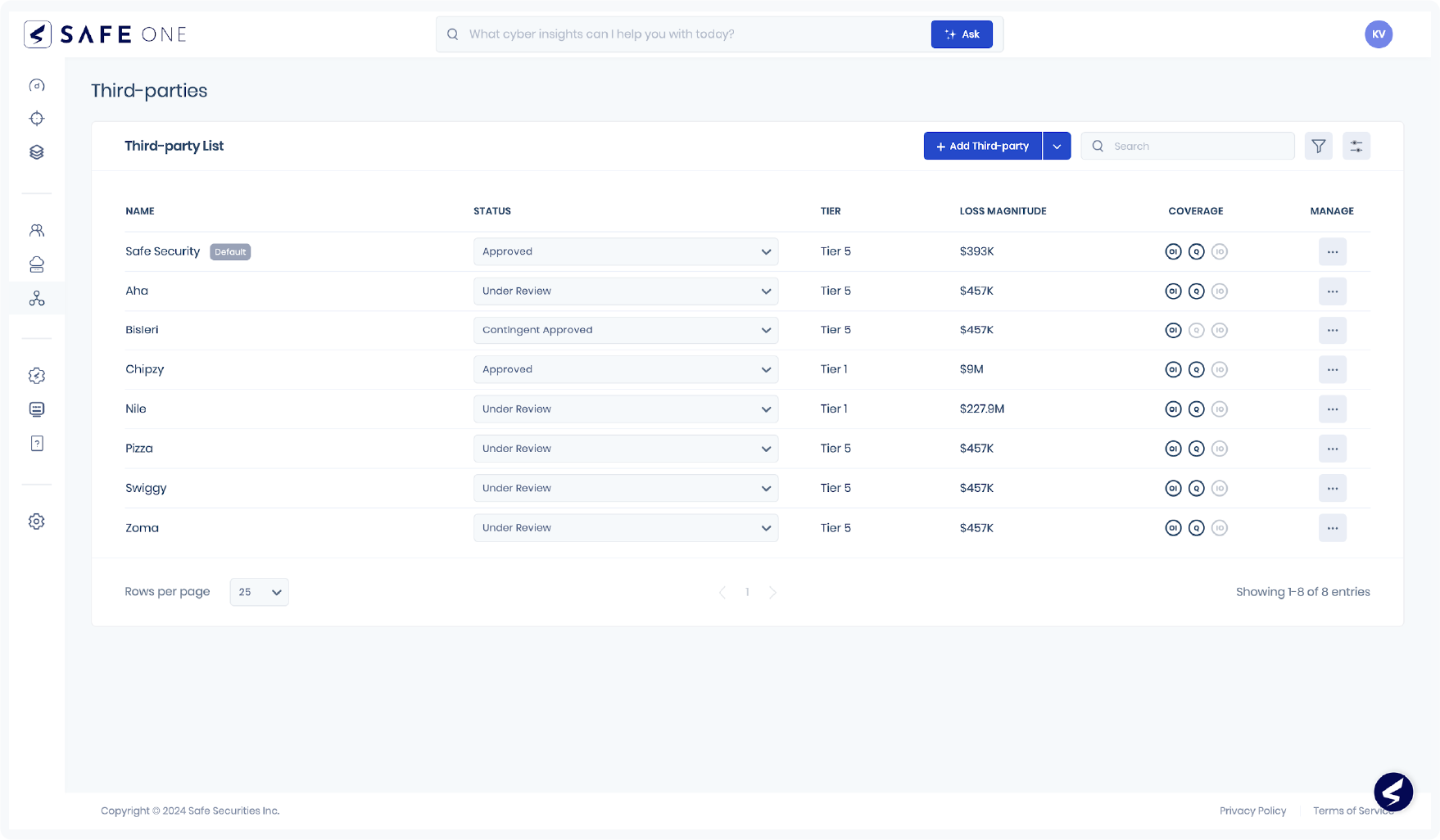
SAFE comes with dozens of out-of-box risk scenarios contextual to your business but also allows users to define granular risk scenarios that generally end up first replicating and over time replacing scenarios defined in the risk registers and GRC tools of companies.
Defensible, Globally-Recognized Standards
SAFE One harnesses the power of globally recognised standards such as MITRE ATT&CK Framework, the FAIR (Factor Analysis of Information Risk) model, and other ancillary standards such as FAIR-MAM & FAIR-CAM to furnish trustable and defensible risk scenarios, underpinning the NIST CSF 2.0 framework’s call for an open, standard-driven approach to cyber risk quantification.
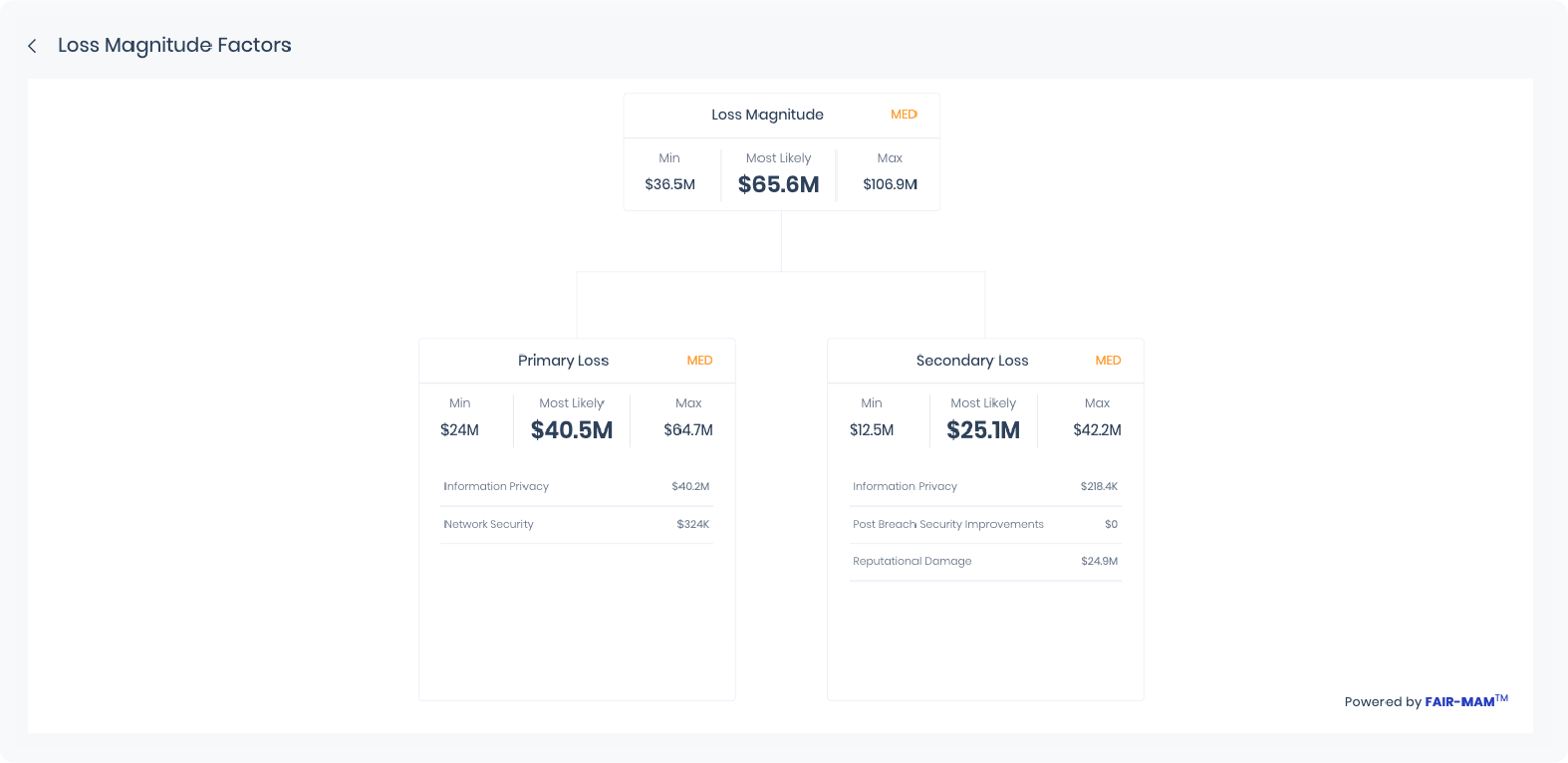
The FAIR model, known for its economic grounding and emphasis on tangible business outcomes, resonates with NIST CSF 2.0 vision for a cost-effective, ROI-centric cybersecurity approach. It enables CISOs to communicate cyber risk with a financial gravitas that stakeholders understand, fostering a common language between the security domain and the business world—a prerequisite for successful integration as per the NIST.
AI-Driven Insights of SAFE-X and OOTB Reports
SAFE One’s interactive SAFE X chat interface, coupled with customizable reporting, provides CISOs a communication channel that is not just intuitive but also effective and impactful. This quick and easy exchange aligns perfectly with the NIST CSF directive for clear and defensible reporting, ensuring that cyber risk is articulated in a manner most digestible to business leaders and regulators.

In addition to SAFE X, SAFE One’s wide array of automated reporting tools augments the platform’s versatility and utility, enabling CISOs to present complex cybersecurity data in a manner that is accessible and actionable. This capability is intrinsically tied to NIST CSF 2.0’s focus on effective risk communication, enabling SAFE One users to deliver sophisticated cybersecurity insights with minimum friction and maximum engagement.
Conclusion: Turning Cyber Risk Management into a Business Enabler
With NIST CSF 2.0, leaders are encouraged to consider cybersecurity as a strategic business enabler rather than a technical or compliance burden. By aligning cybersecurity strategies with business objectives, organizations can ensure that their security practices truly safeguard their most critical assets and business functions. SAFE exemplifies a solution that makes this possible, charting the path for others to follow in this new era of cyber readiness.
If you want to take your first step to improving your cyber risk management program, we would be delighted to help. Request a demo!


