Okta Breach and Third-Party Cybersecurity: Addressing TPRM with Risk Quantification

The Lapsus$ group first made headlines in December 2021 after a ransomware attack against the Brazilian Ministry of Health, exposing the PHI of millions of people. It has since targeted multiple large companies including Nvidia, Samsung, Microsoft, Ubisoft, and now – Sykes Enterprises.
Sykes, a business service outsourcing unit owned by the Sitel group, disclosed that one of their employee’s Okta accounts containing customer data was breached in January 2022. Documents leaked by the Lapsus$ group raised questions about both Sitel’s and Sykes’ security defenses, which highlights a pertinent challenge faced by businesses: third party cyber risk management.
Lapsus$ used remote access services and publicly accessible hacking tools to navigate through Sitel’s network over five days. They disabled security scanning tools that could have alerted Sitel about the intrusion sooner. Sitel’s Azure cloud infrastructure was also compromised.
“In January, we did not know the extent of the Sitel issue – only that we detected and prevented an account takeover attempt and that Sitel had retained a third party forensic firm to investigate. At that time, we didn’t recognize that there was a risk to Okta and our customers.” – Statement by Okta.
Okta’s statement is a succinct summary of how most businesses manage cyber risk arising from third parties – without confidence, and with limited visibility. Before diving into the solution, it’s important to understand the third party threats that businesses are up against – and why.
Why are third party breaches becoming the go-to for adversaries?
With third party vendor networks expanding, one-to-many or ‘buffalo jumping’ data breaches will become more frequent. The Lapsus$ data breach is not the first third party data breach – and certainly, not the last (remember SolarWinds, Kaseya, and Codecov?). But why is the frequency and impact of such attacks increasing? There are three major reasons:
- Adversaries are becoming more sophisticated, better funded, and well organized.
- The Conti group’s chats reveal a hierarchical structure with quarterly strategies for growth, expansion, and hiring.
- As their business-focus increases, they plan data breaches that yield maximum financial reward with minimum effort.
- Poor visibility of the cyber risks inherited from direct and indirect vendors.
- Businesses inherit the cyber risk posture of their direct vendors (third party) and their vendors’ vendors (fourth and nth party). A report published in 2022 reveals that 34% of organizations use more than 50 SaaS apps and over 16% use more than 100 SaaS apps.
- 63% of businesses don’t have visibility into the level of access and permissions external or internal users have - they have a limited-to-no view of the extent of third party access to their network, or even when and why third parties have accessed their network.
- Relying on traditional, reactive methods in a dynamic cloud-first environment.
- Businesses still depend on age-old, point-in-time snapshots of cyber risk postures of their third parties. Questionnaire-based surveys and outside-in scans of third parties during their onboarding are still the most widely used forms of third party risk assessment.
- Gartner’s research revealed that more than 80% of legal and compliance leaders agree that third party risks were identified after initial onboarding and due diligence, suggesting traditional due diligence methods in risk management policy fail to capture new and evolving risks.
These methods are akin to clicking a photograph of an individual and trying to guess the status of their health. While they provide an overview, the findings might be misleading and give a false sense of security.
Cybersecurity and Infrastructure Security Agency (CISA) instructs businesses in its ‘Shields Up’ guidance that “the first step to resilience is to reduce the likelihood of a damaging cyber intrusion.” To reduce the likelihood of an incident, and follow the current reporting guidelines, an organization must first know and measure the likelihood of a data breach happening. This knowledge is fundamental in the journey toward adopting proactive cybersecurity.
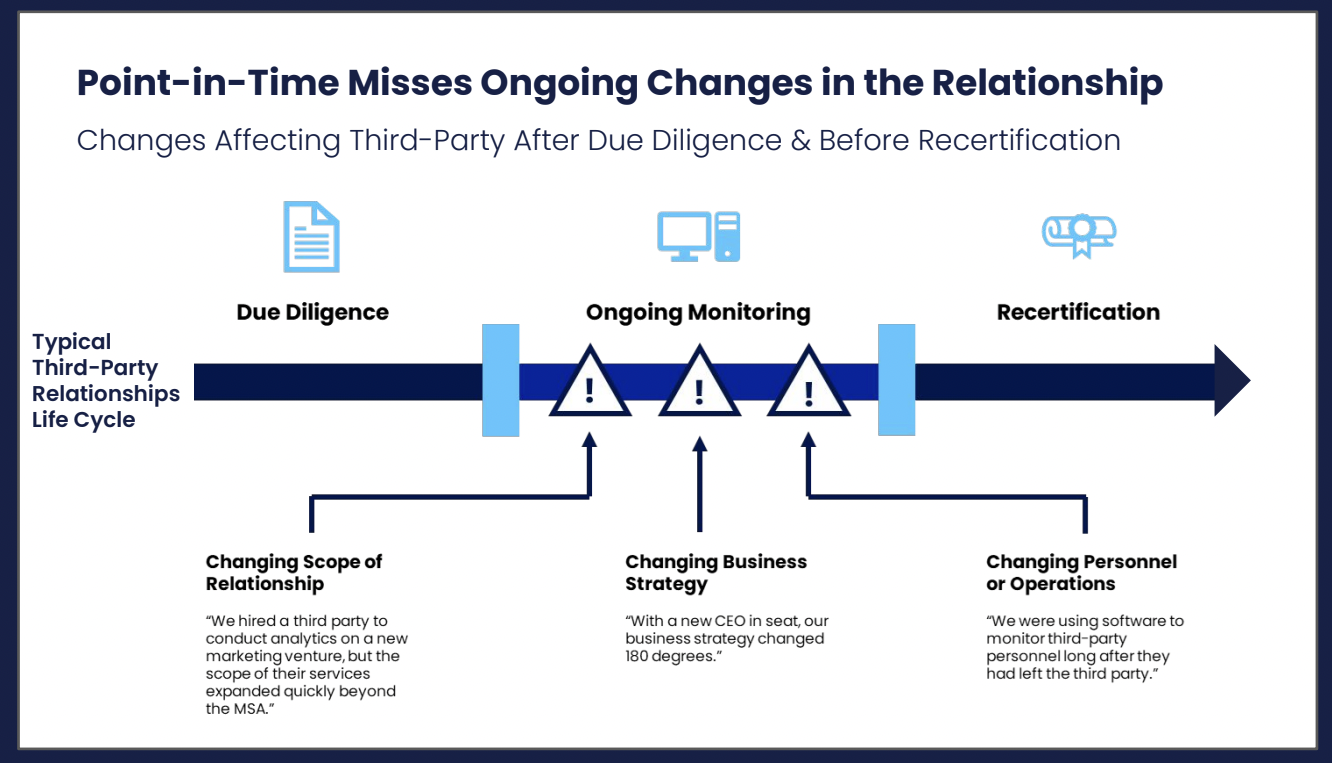
Figure 1: Point-in-Time Assessments Miss Ongoing Changes in the Relationship, Gartner
Third-Party Cyber Risk Management: Three steps to shifting from detecting to predicting a breach
When it comes to proactive security, you’re already on your way with the volumes of valuable data generated by a variety of cybersecurity initiatives. There’s a great deal of visibility to be unlocked when you invest in a method to aggregate this data. Moving beyond the collection and storage of data, to quantifying it using cutting-edge data-science-backed technology, you’re in the unique position to prioritize, mitigate, transfer, or accept this. You cannot make these decisions soundly without full transparency that can only be achieved through risk quantification.
Step I: Categorize
- Categorize vendors into tiers based on their size and the level of critical server or network access available to them – descending by the level of risk exposure
- Tier 1 vendors: Assess cybersecurity risk in real-time
- Tier 2 vendors: Assess risk daily
- Tier 3 vendors: Execute weekly assessments.
By categorizing them in this way, you are able to immediately identify your riskiest vendors and have a clear rank of priority for any activity you carry out. It reduces taxing your already strained resources while enabling your security team to focus on the threats most likely to be the reason for your next breach.
Step II: Digital Footprinting
Scan the entire digital footprint of every third-party vendor in a non-intrusive, outside-in risk assessment. This should include:
- Email Security
- DNS Security
- Application Security
- Network Security
- System Security
Along with an assessment of:
- Breach Exposure for the identification of inadvertent or intentional exposure of potentially sensitive information.
- Compromised Systems to detect systems and applications involved in malicious and/or unusual activity.
- Cyber Reputation to identify threats that may damage your brand reputation and eventually affect your revenue. In Okta’s case, their share price dropped by more than 7% when news of the Lapsus$ breach reached the market.
Step III: Managing risks
Understand your risk to prioritize its management and mitigation. Risks posed by your third party network can be classified as:
- Critical: Root-level compromise of servers or infrastructure devices with devastating consequences.
- High: Elevated privileges and significant data loss, or downtime, indicating high priority remediation
- Medium: Exploitation provides limited access but should not be ignored.
- Low: Very little impact and low priority security alarms.
- Informational: Security gaps that do not need immediate remediation.
Building your essential source of truth for Cyber Risk Management
Point-in-time audits open your organization up to significant risk exposure. The continuous, always-on tactics of threat actors mean that you need a continuous, real-time solution to monitoring and mitigating cybersecurity risk. This is why SAFE has been designed to provide you with the essential capability to ingest, process, and predict third party data breaches.
SAFE enables security and risk management leaders to visualize their risk posture in depth by combining signals across their estate into a central, real-time dashboard where you can prioritize risk across your organization.
You’ll have a real-time indicator of how likely your organization is to be breached:
It helps measure the efficiency and effectiveness of various cybersecurity policies, initiatives, and strategies. This enables everyone in the organization to be on the same page when it comes to the cyber risk posture of the business and promotes a culture of cyber resilience across the enterprise.
You can successfully communicate your risk exposure to the board
Deliver your highly technical understanding of risk exposure in the language and context that your board wants to understand: What is the cost to business? As the industry becomes more attuned to cybersecurity risk, it’s becoming more evident and accepted that the buck will always stop with the board. In this scenario, the representation of cyber risk as the potential financial loss –and of cybersecurity as the potential financial savings) – can change the game for security leaders.
You can justify your cyber insurance premiums
Organizations that proactively mitigate cybersecurity risk often see this reflected in their premiums. SAFE helps your business define your cyber risk appetite, understand your risk tolerance, and adjust risk-sharing techniques accordingly, helping you secure the most appropriate coverage at a justifiable premium.
With SAFE, any suspicious activity by vendors (third, fourth, nth party) or SaaS service providers such as a change in access settings to cloud assets, misconfigured S3 AWS buckets, or unexpected employee activity would trigger a significant drop in the overall and third party SAFE score, sending real-time alerts to the relevant stakeholders, alongside a detailed cybersecurity report of where the gap is, how much it will cost the business, what can be done to fix it, and the steps you should take to successfully manage the risk before it gets identified in your next audit.
Rethinking risk management through quantitative methods will enable organizations to take a smarter approach to cybersecurity: choosing informed decision-making over guesswork. Check out our 25-point checklist created to help you in your journey towards proactively managing third party cyber risk with data-driven decisions.



