Prioritizing Risk in Cyber “Risk” Quantification and Management
Too many organizations are trapped in the past. They run what might be called a legacy cyber risk assessment handed down over the years without questioning. It starts with an uncritical definition of risk. Ask yourself, what are the risks of these risks?
- Cybercriminals
- Weak passwords
- Internet-facing web servers … to name a few
If you answer in spreadsheets or “high, medium, or low” – or add a visualization of red, yellow, and green – based on your opinion – let’s call it a mental model – you’re practicing legacy risk assessment on subjective standards that can’t be replicated from one observer to the next. How red is your red compared to mine?
What’s more, your “risks” – cyber criminals, etc. – aren’t risks in a way that’s ultimately useful for risk management. To achieve that, you need to create a risk statement as a scenario – a loss event – with measurable elements: “A threat actor (cyber criminals) – gains access to an asset (a crown jewel database) – by some means (a brute force password attack) resulting in a loss of confidential data.”
💡To make well-informed decisions in cyber risk management, we need to quantify risk scenarios, compare their outcomes in dollar terms, and prioritize our efforts for the best opportunities for risk reduction.
- Managing Risk Effectively Starts with Understanding Risk in a Business ContextIt’s all very well to say, “Start quantifying your risk.” But where to start? Where to find the data? The risk scenarios? It’s a business question, not a technical question. You’ll need some knowledge that you probably already know or know where to find:
- The value chain for your businessFrom R&D to manufacturing to sales and distribution to customer service – how your organization makes money.
- The critical assets and processesAlong the value chain, the databases and applications that, if compromised or disrupted, would put you at a serious disadvantage (say, an intellectual property leak) or even cripple your operations (say, payment processing down).
- Loss event scenariosAsk your business or functional unit owners for their cyber nightmares as a starting point – render those into risk scenario statements with a threat, asset, and effect.
- The dataAvailable within your organization or from industry sources, you need data on both the frequency of occurrences and the magnitude of losses. Here, it gets complicated when you try to price the multiplicity of loss types (business interruption, incident response, etc.) or estimate the likelihood of the multiplicity of cyber events (data breach, insider error, etc.) and the presence or absence of protective controls in your environment.⚡️Freshness Warning: The risk landscape is constantly changing. Yet the standard cadence of legacy risk assessment has been quarterly or even yearly reporting – clearly out of date. You need real-time visibility into cyber risks.
Bringing It All Together for a Holistic Action Plan
With a solid foundation in quantitative cyber risk analysis, a risk management team can
- Identify, Prioritize, and Communicate Top Risks for First and Third-Party
Show your organization a transparent analysis process that arrives at a prioritized list of risks based on a balance of likelihood and impact. Stakeholders can challenge your assumptions or inputs, but by implementing FAIR, your methodology is the unquestioned leader in risk quantification.
- Prioritize Strategic Initiatives Based on Return on Security Investment
With risk quantification, you can compare security initiatives for their measurable effect on risk reduction, then apply the same standards that any business spending proposal must meet.
- Adjust Operations to Manage Cybersecurity Cost-Effectively
Which controls or security processes pull their weight in risk reduction, measured in financial terms? Which databases are at too much risk of a breach to be worth maintaining? Quantification – fed by continuous reporting of the status of controls and the attack surface – informs ongoing operations, changing technical discussions into business discussions.
💡You’ve done your job; now get out of the way. You have given decision-makers a set of business decisions they can make with confidence – and elevated cybersecurity from a silo into the mainstream of risk management.
ANSWER THE “HOW TO”
With SAFE and the automated FAIR™ model (Factor Analysis of Information Risk), we can quantify the elements of a risk statement for their probable frequency of occurrence and magnitude of impact (in money terms) and arrive at a range of likely outcomes.
STEP 1: DEFINING CYBER RISK SCENARIOS
The FAIRTM Model of cyber risk scenario creation clearly outlines a 3-step process:
- Context creation: Identifying major loss exposure events concerning your business and industry. This might involve research, speaking with subject matter experts, and gathering intel from industry data.
- Scoping: Combing through your attack surface to create a list of assets, threat actors, and loss effects you would want to include in a cyber risk scenario.
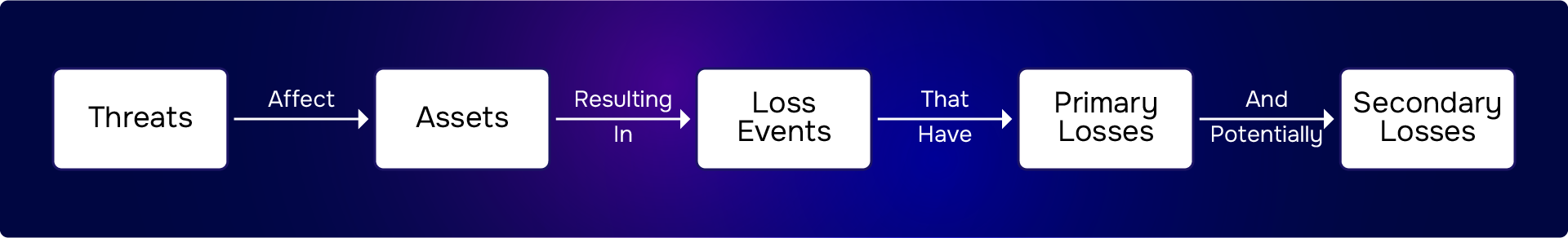
- Loss Flow Diagram: This a high-level visual that considers the threat actor, type, asset, and loss effect and shows how loss can materialize at every step while also considering the controls that are in place or lack thereof that may change the frequency/impact of the risk scenario. This is the most comprehensive and time-consuming step of all.
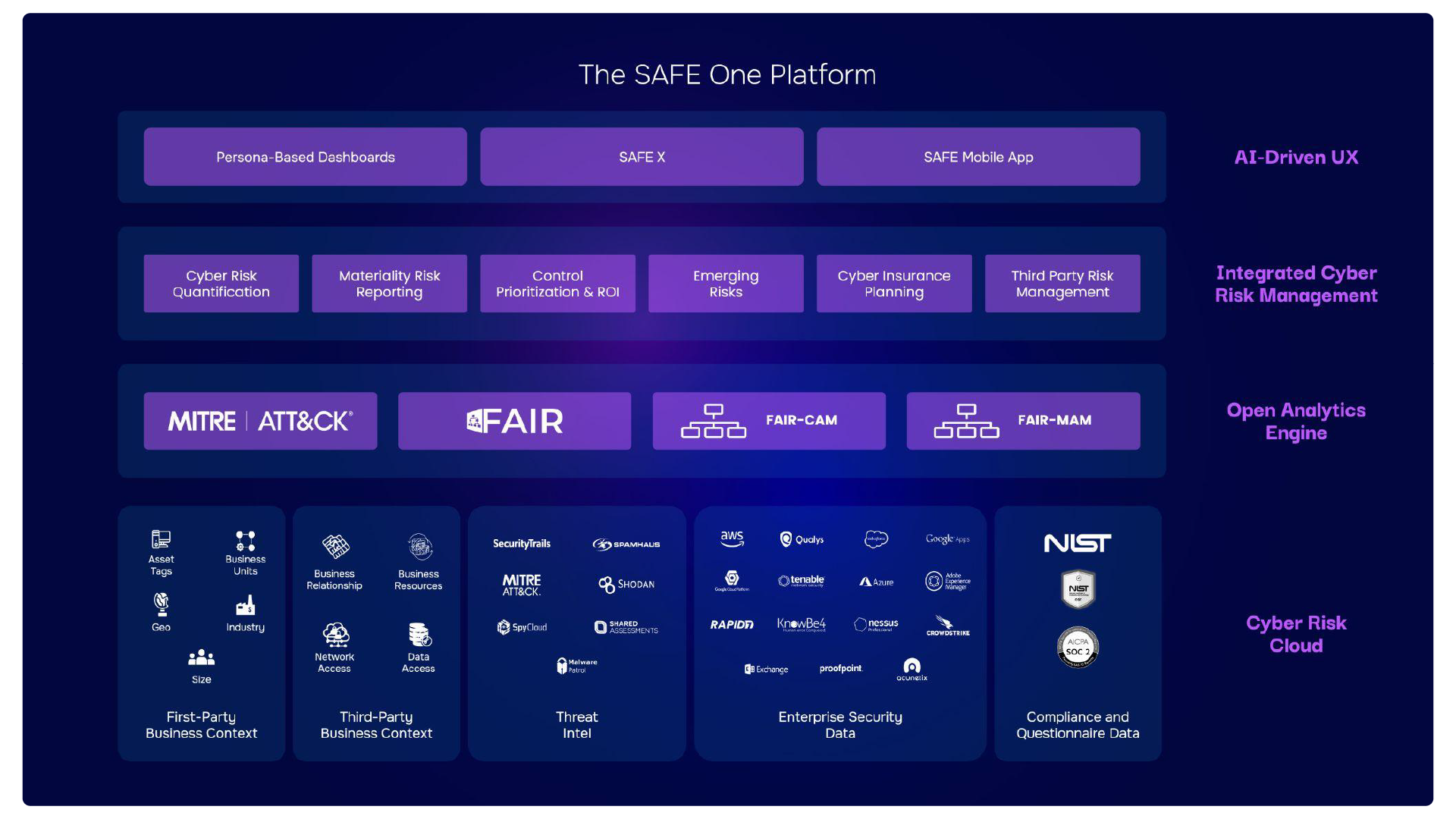
The SAFE One platform automates the process of creating and analyzing cyber risk scenarios for first and third-party risks, reducing the time required from months to just minutes. This rapid turnaround enables your team to quickly initiate and complete risk assessments, streamlining the entire process.SAFE One recognizes that different business functions and vendors carry varying risk and exposure levels. It equips the creation of cyber risk scenarios tailored to your entire organization or specific areas such as geography, business units, departments, or asset groups. This approach offers an overarching perspective of enterprise-wide risk and detailed insights into individual business units and your complete supply chain.💡 Customer Benefit: Different business units often possess unique sets of business resources at risk. Similarly, governance, risk, and compliance requirements can vary significantly between business units in different parts of the world. By generating risk scenarios tailored to each unit, geographic location, or asset, Chief Information Security Officers (CISOs) gain unparalleled visibility into the overall risk landscape of the entire business.Within the platform, you can choose from out-of-the-box risk scenario templates or build your bespoke risk scenarios. While creating custom risk scenarios, the SAFE platform will perform the contextualization, scoping, and loss flow diagram automatically based on your selection of the business resources at risk, threat actors, and loss event outcome.
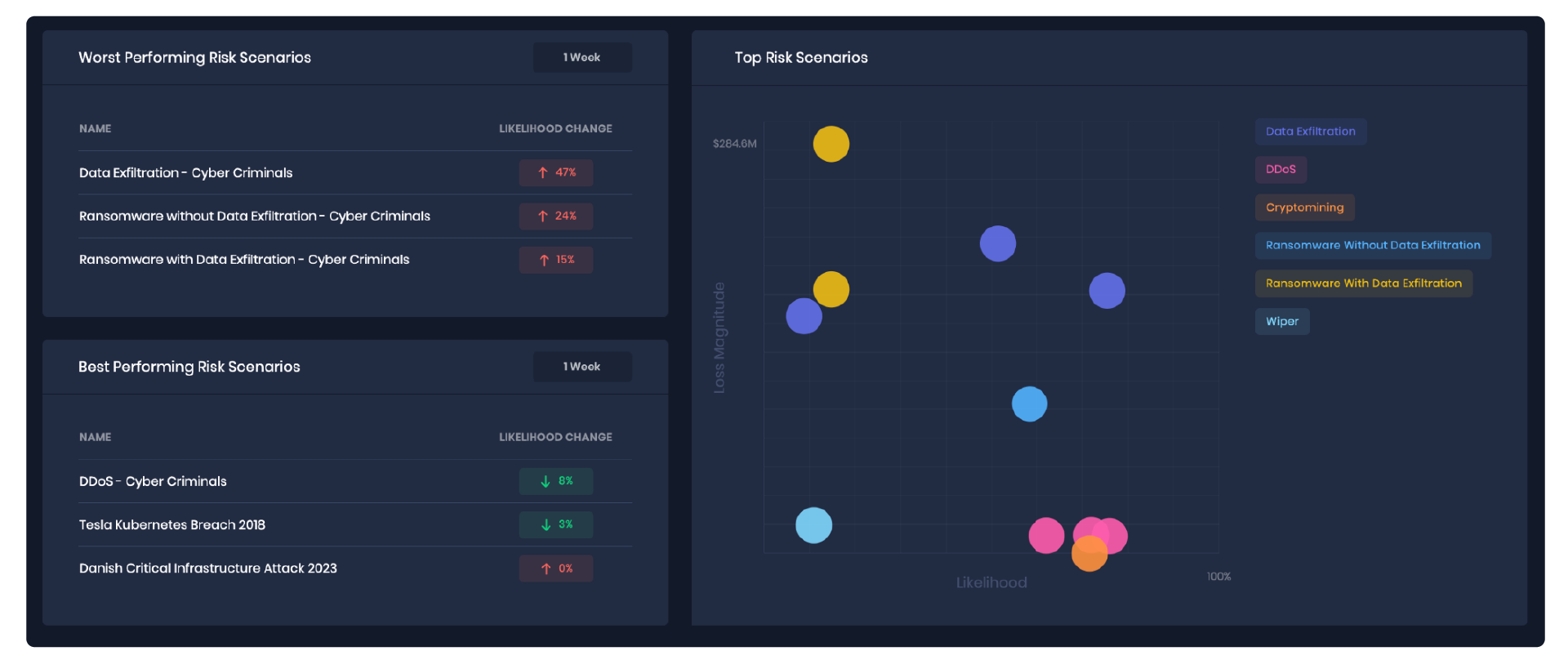
STEP 2: ALIGN ON RISK APPETITE WITH STAKEHOLDERS
After defining cyber risk scenarios, CISOs must align the quantified risk exposures resulting from these scenarios with the acceptable risk exposure determined by key stakeholders, executives, and members of the Board. Historically, CISOs have relied on spreadsheets for this task, which often entail subjective abstractions and lack detailed precision.The SAFE One platform streamlines the process, eliminating manual effort and estimations to furnish stakeholders with precise data. Each risk scenario delineates the loss exposure regarding dollar impact derived from industry benchmarks, 10K filings, annual industry reports, and other reliable sources. Additionally, the platform automatically categorizes loss impact into primary and secondary losses, enabling CISOs to distinctly identify areas of greatest impact.💡 Understanding cyber risk becomes simpler with every risk scenario mapped precisely on a graph. Stakeholders can filter the view per their most pressing concerns and take decisive action. SAFE One empowers CISOs to drive clear, data-led communication with the Board and other stakeholders.The SAFE One platform provides a comprehensive single-dashboard view of the most critical and top-performing risk scenarios. It further compares your business’s cyber risk posture with emerging industry hacks, offering insights into new trends. It actively monitors the evolving external threat landscape to develop scenarios based on real-time global hacks.It consistently suggests relevant ‘trending risk scenarios’ within your industry and provides insights into the likelihood, along with your susceptibility to being breached by various threat actors.Additionally, SAFE One offers a single-screen display illustrating your enterprise’s standing in terms of risk exposure compared to industry peers, facilitating informed decision-making and strategic planning.
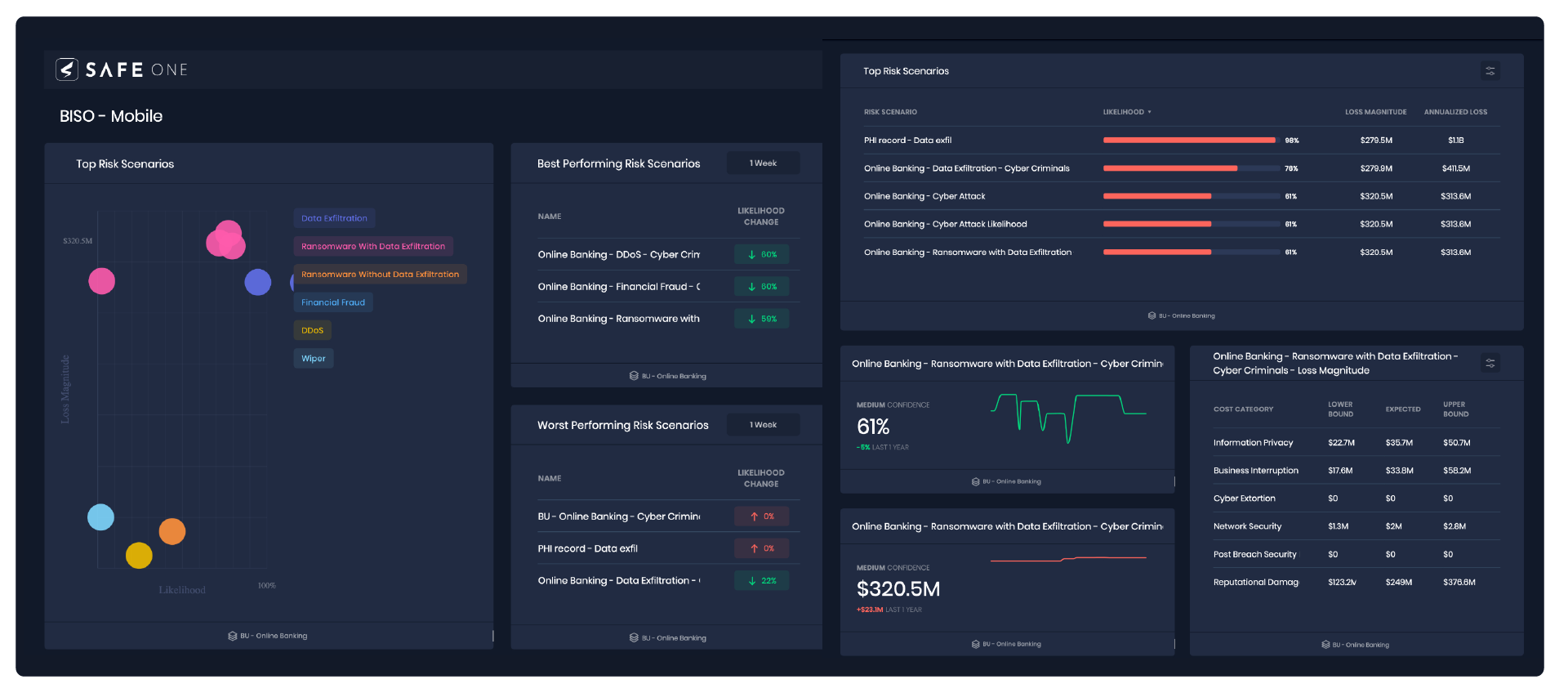
STEP 3: TRANSLATE TACTICAL FINDINGS TO THEIR IMPACT ON RISK SCENARIOS
Your Board still considers cybersecurity a technical issue because you’ve not yet presented cybersecurity as a risk but as a series of tasks that need completion. The most crucial aspect of managing and reducing cyber risk is the efficient management of controls – and putting it in the context of risk reduction. SAFE One aids in strategically planning cyber risk programs for the year and provides prioritized recommendations to reduce risk.💡 Reports suggest that enterprises deploying over 50 tools ranked themselves 8% lower in their ability to detect threats!The SAFE One platform is uniquely positioned to empower CISOs to gain a holistic visibility of their most critical risks concerning the enterprise’s control landscape. Using FAIRTM-CAM, SAFE One can automatically assess how control interdependencies and their impact on overall risk reduction.While organizations typically prioritize only vulnerabilities, SAFE goes beyond this by offering a comprehensive list of findings, supporting true risk-based vulnerability management misconfigurations, malware, user controls, and more to present a unified list of tactical findings to effectively reduce risk in a prioritized manner.
STEP 4: MONITOR AND SEE WHAT’S CHANGED
Your job has just begun! Now that you’ve defined and determined your top risks, aligned each stakeholder on the risks that need to be accepted/mitigated – you have to monitor how your decisions are impacting the business’s bottom line. How well are you reducing your risk exposure?💡 Through its See What’s Changed feature, users can immediately visualize how changes in their control landscape affect risk reduction. This empowers users to make data-driven decisions regarding the addition, removal, or adjustment of control maturity levels.SAFE One is the first and only solution that has implemented the FAIRTM-CAM model to automate and translate controls effectiveness to risk and give you the impact in financial terms. With SAFE One, CISOs can simulate the cost and results of security spending to predict risk reduction; whether it’s new solutions, tool expansion, or technology adjustments.The SAFE One platform automatically evaluates each control based on three criteria: Coverage, capability, and reliability. Leveraging your cyber risk tolerance and appetite, SAFE One offers intelligent and actionable recommendations to enhance control maturity across any of these parameters. This approach ensures a more comprehensive and return-on-investment-driven approach to managing residual risk.
STEP 5: CONTINUE TO OPTIMIZE RISK BURNDOWN
The cybersecurity risk landscape evolves continuously, so your security strategies must be flexible and agile – in real-time. While quarterly board meetings are great for “updating” the key stakeholders on the progress, your cybersecurity strategy needs a way to optimize risk burndown continuously. Now that you have visibility on what’s impacting your risk the most, you need to constantly update your strategy to stay ahead of the curve.The SAFE One Platform offers unique visibility into the various treatment options (risk management plans) a CISO can propose to the CFO, CEO, and Board. Using the “what-if?” analysis feature, the cybersecurity team can curate alternative treatment strategies for every critical risk – including a cost:benefit analysis.💡Users of the SAFE One solution can align cybersecurity investments based on the pre-defined cyber risk appetite and choose from varying risk management options that reduce the loss magnitude, breach likelihood, or both. Security leaders are equipped to justify the dollar impact of security investments on the business’s bottom line. With this clarity and data-driven approach, it is easier to develop an ROI-driven strategy than investing in enhancing the capabilities of existing solutions or buying more tools or products.
SAFE One’s “What-If? Analysis” includes intelligent, actionable recommendations, coupled with the prioritized risk treatment, that enable you to formulate various risk treatment options and visualize the reduction in breach likelihood and magnitude of loss (financial impact) by tweaking cyber control’s maturity parameters.
Prioritizing Risk in the Right Context
The SAFE One Platform is arguably the industry’s most transparent, trustable, and defensible cyber risk quantification and management solution. With its advanced AI-powered approach and FAIR-backed methodology – there isn’t a single value that you can’t click on and explore deeper. As they say, never trust a score you cannot click.
Schedule your SAFE One demo with a cyber risk expert who can assess how this platform can alleviate your cyber risk management woes and elevate your practice.