SAFE Featured as One of CRN’s “Top 10 Hottest Cybersecurity Tools and Products of 2024 (So Far)”
SAFE features in the top 10 hottest cybersecurity tools and products of 2024 (so far), listed by CRN. We’re excited and pleased to share this space with Wiz, Zscaler, CrowdStrike, Palo Alto Networks, Cisco, Sentinel One, and more. They highlight SAFE’s expansion into the third party cyber risk management (TPRM) space: “The offering stands out by quantifying the risk of specific threats — such as ransomware and data exfiltration — for third-party vendors in an “actionable” manner”
Why Was SAFE Included?
Third-Party Risk Management: The Unsolved Problem
Third-party risk management remains one of the top three challenges for businesses worldwide, yet it remains unsolved. A Gartner survey finds that 45% of organizations experienced third-party-related business interruptions during the past two years.
Third-party risk management needs an urgent and definitive overhaul but currently available solutions simply do not work! CISOs and TPRM leaders are demanding that this process becomes more efficient, actionable, and risk-driven. So, what is the answer, and is there really a TPRM solution that works?
Enter SAFE TPRM.
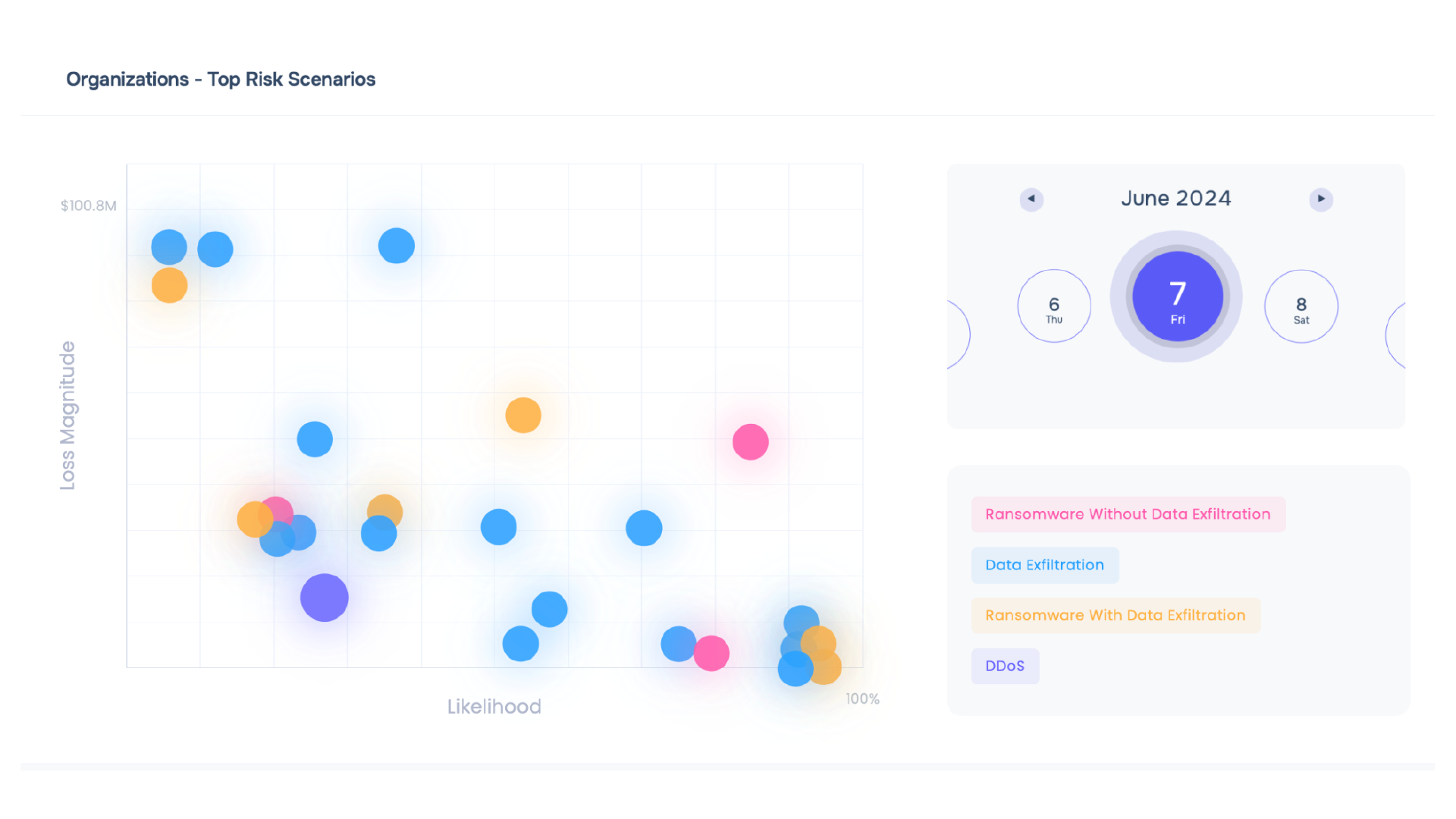
How Is SAFE Transforming Third-Party Risk Management?
The SAFE TPRM offering stands out from its contemporaries because it takes TPRM as you know it and turns it on its head. Saket Modi, co-founder and CEO of SAFE, told CRN “SAFE TPRM provides an actual risk measured in dollars of ransomware occurring at a certain third party – we actually quantify the risk in a way the business can understand it.
SAFE TPRM offers five major benefits over conventional TPRM solutions:
1. Integrate Third-Party Risk Management with Enterprise Risk Management
Current TPRM solutions treat third party cyber risk management as separate entities and do not provide insight into the enterprise’s internal resiliency controls toward third parties. SAFE eliminates this challenge with its unified risk management approach.
CRN highlights, “On top of offering improved third party cyber risk management compared to existing vendors in the space, SAFE also combines the third-party signals with the data on first-party and SaaS risk that the company has already offered. As a result, in one dashboard, you can get your first party, your third-party, and your SaaS applications [risk] all converged into one.”
We advise our customers to always assume their third parties have not addressed critical security exposures and that the enterprise needs to safeguard itself with zero-trust principles.
SAFE TPRM buckets enterprise controls into third-party likelihood reduction and loss magnitude reduction that equip a business to safeguard itself against potential data breaches. By implementing a zero-trust architecture toward third parties, CISOs can confidently answer a fundamental question: “Assuming all vendors are compromised, what are our resilience controls to minimize risk to the business, and how effective are they?”
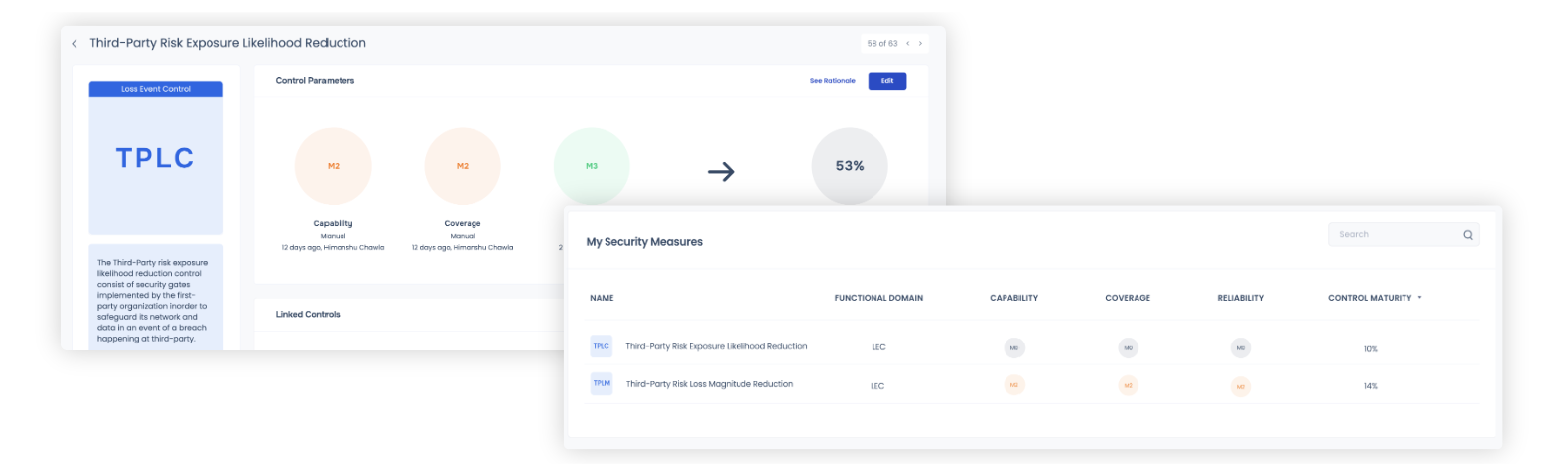
2. Prioritize Third Parties Based on Risk to Your Business
Compliance-driven activities have overshadowed risk reduction in TPRM. Fortunately, this thought-process is already changing as CISOs and TPRM leaders acknowledge the need for a solution that enables them to identify and reduce risk proactively.
SAFE TPRM adds a much-required “risk” context to third party cyber risk management. With SAFE TPRM, enterprises can:
- Tier third parties based on “risk” instead of contract or revenue-based tiering.
- Consolidate third-party risk data using 100% automated controls telemetry from outside-in, questionnaires, and inside-out assessments
- Align the findings to evidence reports (vulnerability assessments, phishing reports, secure software documentation, and more)
- Calculate the vendor’s risk by mapping the extent of data access, network access, and business interruption
- Create cyber risk scenarios to assess the likelihood and potential financial impact of ransomware attacks, DDoS, data exfiltration, and more
Using SAFE’s risk-driven insights, CISOs and TPRM leaders can demonstrate risk burndown and ROI from third-party risk reduction initiatives, adjust cyber insurance investments, and transfer liability to their supply chain in the event of a breach.
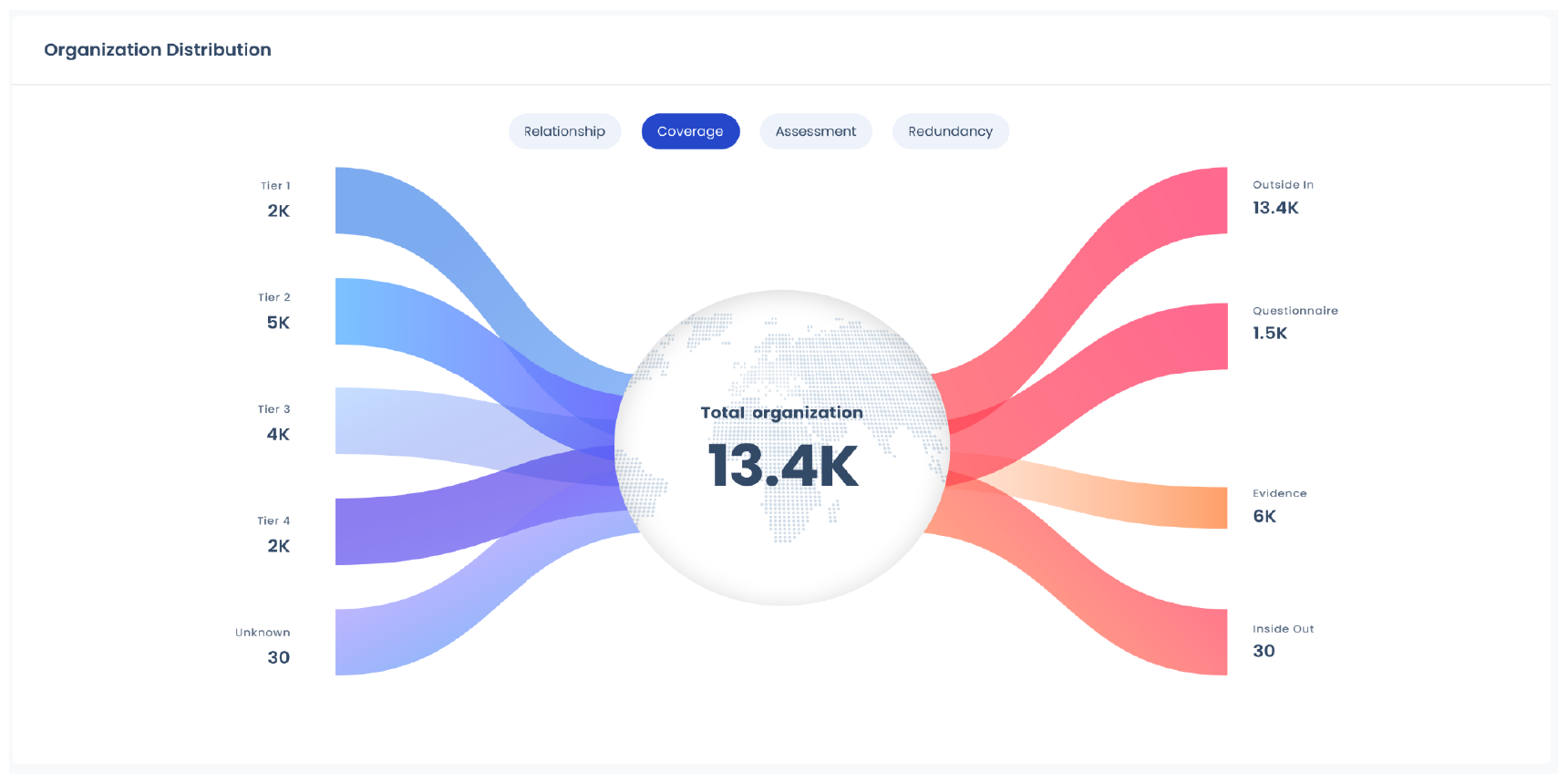
3. Focus on Critical Third-Party Controls
Today, the TPRM methods deployed by enterprises generate a lot of work yet do not help third parties achieve an acceptable security risk posture. The reason? There are simply too many alerts and too much to do without risk-driven prioritization of efforts. To get ahead of this, business leaders are curating a crisp list of security controls they intend to pursue with their vendors.
SAFE TPRM is the industry’s only solution that has automated the FAIR Third-Party Risk Assessment Module (FAIR-TAM). Combining FAIR-TAM with extensive research of past and current cyber attacks with third-party origins, we’ve curated a list of top “priority” 10 controls that organizations must focus on to bring tangible results.
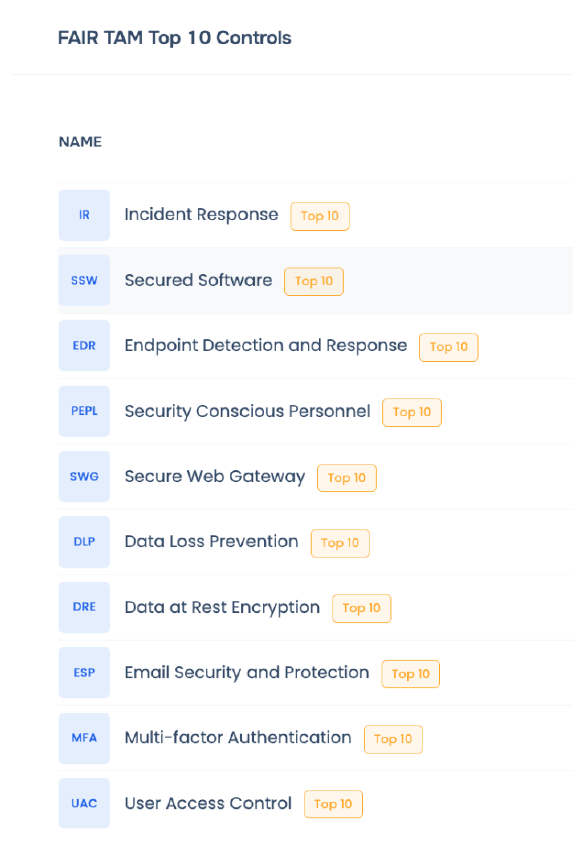
CISOs and third-party cybersecurity teams are relieved of the laborious and manual processes involved in fixing hundreds of controls, leaving them with time and energy to prioritize what matters the most.
4. Partner with Third Parties to Improve their Security Programs
Third-Party Risk Management can only advance if enterprises and vendors can work in tandem to enhance the overall cyber risk posture. However, as vendor networks expand and become more complex, it is impractical to address security gaps with each vendor individually. This is where AI-powered Third-Party Risk Management is a game changer.
SAFE TPRM makes it simple, swift, and efficient to collaborate with your supply chain using AI-assisted training and onboarding modules that provide 24×7 support to vendors. SAFE provided the option of sharing a direct platform access to vendors via role-based access control. So, third parties can leverage SAFE’s dashboards to visualize their cyber risk exposure and effectively prioritize their critical controls.
This unique partnership enables third parties to manage cyber risk more effectively with security profile visualization, self-assessments, and training materials. It shrinks third-party risk assessment cycles from weeks to days.
5. Optimize Third-Party Risk Management Costs
One of the most significant hurdles to scaling and optimizing third-party programs is the exponential increase in investments. SAFE TPRM acknowledges the dynamic nature of vendor risk management and its associated costs. SAFE platform users can add an unlimited number of vendors at a fixed price since SAFE TPRM pricing is independent of the number of vendors – ensuring 100% of vendors are assessed. This scalable pricing model makes it practical to manage the expenses of your growing third-party portfolio as the business expands.
Adopt SAFE’s TPRM Solution That Actually Works
Third-party risk management needs to be urgently addressed in a way that underscores active risk burndown. SAFE TPRM’s defensible risk management approach makes this a reality. Schedule your 1:1 demo with a cyber risk expert to learn more, or explore our SAFE TPRM promotional offer, which can slash your current TPRM investments by 50%!



