Shifting Your Focus in Third-Party Risk Management
Move Towards Prioritizing Third-Party Controls That Really Matter
Gartner’s research states that “working with critical third parties to mature their cybersecurity risk management practices as necessary results in a 42% increase in enterprise Third-Party Risk Management effectiveness.”
But this is not news to CISOs and TPRM leaders—they know how crucial collaboration with their third parties is to minimize cyber risk exposure from them in the long run. Unfortunately, as the number of third parties in an enterprise’s portfolio balloons, risk leaders are spending more time with fewer tangible results: Seventy-five percent of security and risk management (SRM) leaders report spending more time on activities related to third-party cybersecurity management (TPRM) as compared to 2021, but third-party cybersecurity incidents that resulted in business disruptions increased by almost half (45%).
So what can enterprises do (and how quickly) to shift their focus from check-in-the-box audit tasks to actively reducing risk from vendors through collaboration? Let’s explore.
The Current State of Collaboration with Third Parties
There is an urgency to speed up the process of enhancing vendor cyber risk posture, but current methods do not facilitate or empower enterprises to move at the speed they need to. The Forrester Wave™: Third-Party Risk Management Platforms, Q1 2024 states, “Personalized dashboards along with role-based UIs are no longer sufficient to keep users expeditiously moving through the assigned tasks.” The same Forrester report emphasizes, “Even the most successful risk identification process will have little to no impact on lowering third-party risk if the results are never acted upon.”
Sign up for this webinar as we take you through the lessons from Change Healthcare’s data breach and how to build a third party cyber risk management approach that actually works.
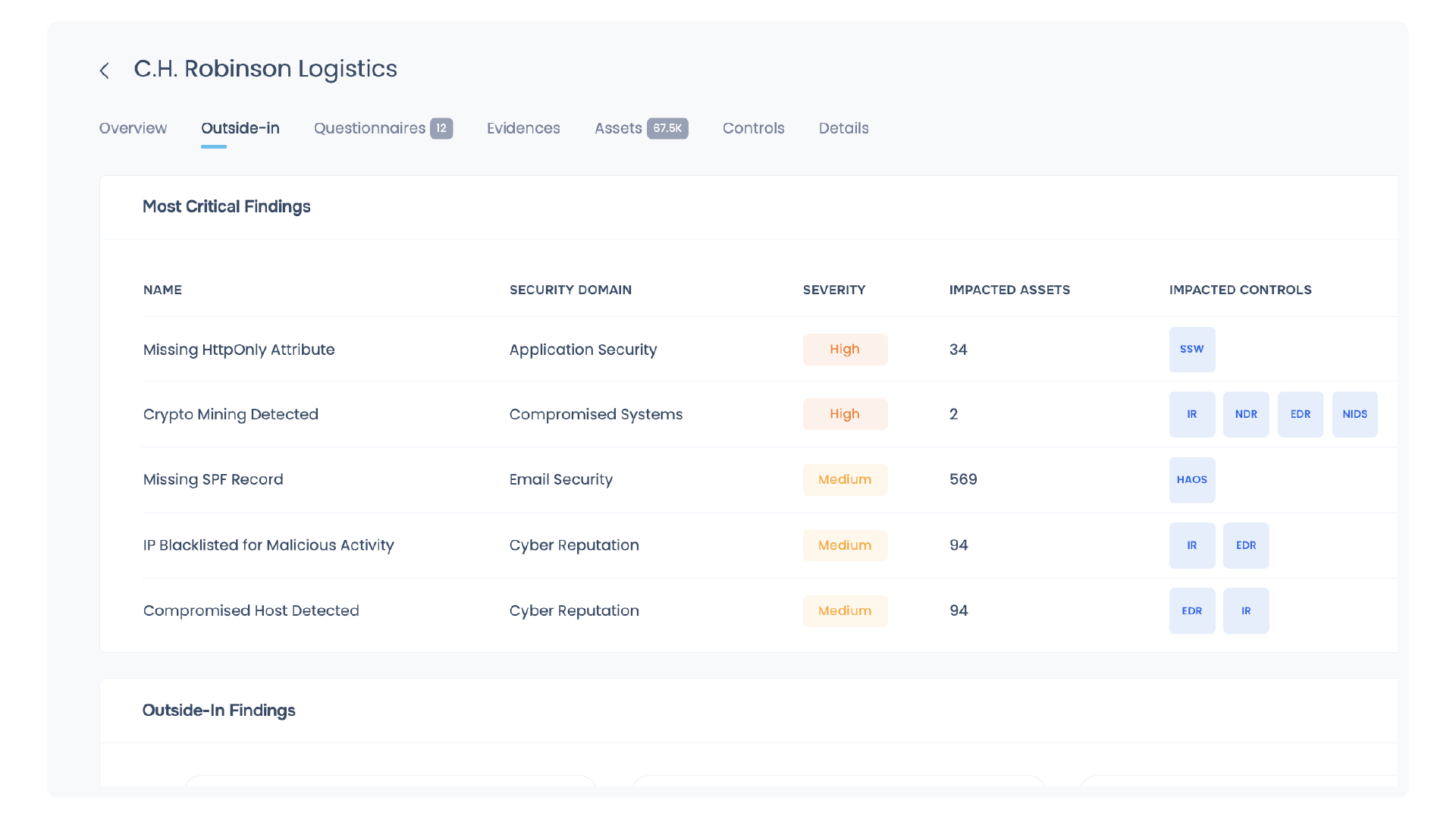
Our conversations with CISOs at Fortune 500 companies have revealed that Security and Risk Management leaders are creating TPRM workflows and processes that equip them to identify a few critical high-risk items that must be prioritized and worked upon continuously. However, this process of critical control and top risks remains dependent on outside-in assessments and questionnaire answers. The CISOs lament that while they do get a fair idea of the risk posed by vendors from cybersecurity risk ratings platforms, they often lack the business context and therefore, aren’t meaningful while creating a repository of top control recommendations. Similarly, while analyzing questionnaire inputs, CISOs have to manage subjective biases and take the answers at face value, leading to the same roadblock.
The Way Forward To Create a Top Controls List: A Singular Risk View
Identifying key or “priority” requirements that third parties need to manage first replaces lengthy workflows and enables a laser-focussed approach to improve vendor cyber risk posture. Enterprises can define this list of priority controls by adopting a consolidated approach that integrates outside-in scans, questionnaire inputs, and inside-out assessments to a singular risk view. This enables businesses to overcome the shortcomings of cybersecurity risk ratings and questionnaires.
The gold standard for identifying high-risk exposures in a vendor’s environment is assessing their true cybersecurity risk posture: What is their data access and network access, and what are their priorities in cybersecurity? This means enterprises will have to apply first-party cyber risk management principles to vendor cybersecurity risk assessment. In other words, conducting inside-out assessments on third parties provides the much-needed perspective to curate a list of key focus areas.
💡 Pro tip: Encourage vendors to regularly provide evidence reports of vulnerability assessments, secure software documentation, phishing, and more. This contextualizes how effectively the controls perform and allows them to make necessary adjustments.
Building a singular, consolidated, contextual risk view gives SRM leaders the data and arsenal to create a list of top controls. The advantages of building and following such a list are numerous:
- Prioritized risk management: Vendors can create a risk-based action plan
- Quicker turnaround time: Vendors aren’t overwhelmed by a long list
- Easier to track progress: Vendors can trace the change in their risk posture
- Scalable security programs: Vendors avoid duplication of efforts
- Liability transfer: Risk reduction becomes a shared responsibility as enterprises and vendors work together
Get your TPRM Program Blueprint: A Guide for Transforming Third-Party Risk Management
How SAFE TPRM Creates a Focus List of Key Controls
While it is possible to manually consolidate and curate a list of key controls, enterprise cybersecurity teams are spread too thin to take this on as well – their energies are better utilized elsewhere. SAFE leverages its proprietary AI-driven engine to ingest all external data and market intelligence (outside-in scanning of domains) of every vendor, parse inputs from all custom and pre-existing questionnaires, and combine this data with inside-out telemetry from third parties. This puts SAFE TPRM’s data and insights in a superior position to curate an actionable list of controls vendors need to prioritize. Why should you trust these controls?
- SAFE consolidates risk exposures across all telemetry sources: outside-in, inside-out, questionnaires
- It contextualizes the data by verifying it against uploaded evidence reports
- SAFE enables vendors to visualize the delta in risk reduction before and after addressing key control parameters through direct portal access
- The platform leverages FAIR-TAM to ensure the controls are truly impacting risk reduction
- SAFE is trusted by multiple Fortune 500 companies to measure, manage, and mitigate third-party cyber risks
Explore why CRN counts SAFE TPRM as one of the hottest cybersecurity products of 2024 (so far). Schedule your live TPRM demo with a cyber risk expert today!



