What Is Third-party Risk Management (TPRM)? – Ultimate Guide
By Sachin Jha
CISOs and third party cyber risk management (TPRM) practitioners are anxious. As enterprises increasingly choose to buy rather than build, third-party technology, data, and services are becoming not just tools but integral components of business strategies. Yet an RSA Conference survey in 2024 found that “87% of Fortune 1000 companies were affected by a significant cyber incident at a third party in the past 12 months.” There’s a stark contrast between TPRM as it’s currently practiced and the rising dependency of enterprises on third-party vendors and supply chain partners.
What Is Third-Party Risk Management (TPRM)?
Think of your business as a busy city that depends on various external services like electricity and transportation, much like companies rely on third-party vendors. Third-party risk management (TPRM) is like city planning, ensuring these essential services run smoothly and do not disrupt business operations.
Third-party risk management is often used interchangeably with several other industry terms, including vendor risk management (VRM), vendor management, supplier risk management, and supply chain risk management. Nonetheless, TPRM is generally regarded as a comprehensive discipline that covers all categories of third parties and various types of risks.
In corporate terms, TPRM involves identifying, assessing, monitoring, and mitigating risks from outside vendors, service providers, or contractors whose actions can significantly impact a company’s operations, security, and reputation.
What is the goal of TPRM?
The goal of third party cyber risk management is to give the enterprise a 360-degree view of these external relationships, the products or services they provide, their criticality to business operations, the redundancy in place (if any), and the controls at the first party or third party that limit damage.
A TPRM team should inform the Finance team of the organization’s loss of exposure to third parties and the Legal and Compliance teams of contractual or regulatory obligations related to third parties. TPRM managers should be in dialogue with the IT, Cybersecurity, or Cyber Risk Management teams on legal, regulatory, or business-continuity risks created by data storage or software as a service (SaaS) applications.
Third-party risk management has traditionally been defined as checking for an organization’s compliance with accepted operational standards (for instance SOC2, ISO, or PCI-DSS) upon onboarding and then perhaps yearly, fulfilled by questionnaires or attestations from the partner or vendor. The goal is to assure the first party that proper protective controls are in place.
In the cyber field, that practice is rapidly being outpaced by a new standard, 1) continuous monitoring of controls status at the third party to keep up with the rapidly changing digital risk landscape and 2) “zero-trust” controls on the first party’s network to limit damage from a system intrusion that originated with a third party.
While the relationship between first parties and third parties is one of mutual benefit, it’s the role of third-party risk managers to regard every third party as a potential threat. A third party could deliver buggy code because of an innocent error – or because cyber criminals had hijacked a software update. In either case, the loss exposure to the organization could be significant. By implementing a robust TPRM program, organizations can proactively identify and mitigate risks, for themselves and their partners. The goal should be to increasingly involve third parties in the strategic direction of the organization so that the security concerns of both parties are baked in as the business grows.
What Is Considered a Third-Party?
Call it a third-party vendor, or supply chain partner, it’s the practice of outsourcing to specialists and it goes back centuries. What’s new is the range of digital services on offer and the ease of engaging a new partner or terminating an old one. No wonder that large companies may do business with thousands of vendors to subcontract products or services in manufacturing, operations, distribution, and many front-office and back-office functions. Some services today are simply unimaginable without third parties: Think of recruiting and hiring or data storage.
But here’s a key distinction in this new era of digital outsourcing. Every new third party onboarded increases the “attack surface” of an organization. Let a third-party SaaS application handle your healthcare benefits or customer relationship management, and you increase your risk that an employee at the third party misconfigures a cloud storage account resulting in a data security breach of your sensitive employee or customer information. Share documentation of valuable intellectual property with your law firm and your IP protection is only as good as your attorney’s.
Why Is Third-Party Risk Management Important?
To grasp the vital role of effective TPRM, let’s consider two recent, impactful incidents:
UnitedHealth Group – February 2024
Overview: UnitedHealth’s subsidiary, Change Healthcare, which processes almost half of all U.S. medical claims, suffered a severe ransomware attack.
Scope of Impact: The attack halted medical claims processing nationwide, affecting approximately 900,000 physicians, 33,000 pharmacies, and 5,500 hospitals. This disruption not only strained healthcare services but also exposed sensitive health data, underscoring a significant operational and security breakdown.
Lesson Highlighted: This incident vividly demonstrates the ripple effect that a cybersecurity breach at a third-party vendor can have across an entire sector—healthcare, in this instance—emphasizing the need for robust TPRM to safeguard essential services and sensitive data. Learn more on how you can avoid a similar situation with SAFE.
Okta – October 2023
Overview: A breach occurred at a healthcare vendor handling support services for Okta, the access-management software vendor, leading to unauthorized access to personal and operational data.
Scope of Impact: Information for 5,000 Okta employees was exposed, including sensitive credentials and session tokens, which could potentially compromise client data and access.
Lesson Highlighted: This breach highlights the vulnerabilities associated with third-party vendors and the cascading effects on privacy, security, and trust. It stresses the importance of TPRM in protecting operational capabilities, maintaining customer trust, and compliance with privacy regulations.
The Conventional TPRM Approach
Traditionally, third party cyber risk management has somewhat mirrored that yearly medical check-up—necessary, yes, but hardly sufficient to catch everything. Companies typically conduct periodic audits, where they check in with their third-party partners maybe once or twice a year, ensuring that they comply with contractual obligations and industry standards. Between these audits? Well, it’s often a case of ‘out of sight, out of mind.’
Manual checks are a common feature of traditional TPRM processes. These involve teams of workers reviewing spreadsheets to ensure services comply with regulatory requirements. This method is not only time-consuming but also prone to errors. Despite some benefits, relying mainly on manual checks can lead to oversight and potential risks being missed, like not paying constant attention while driving.
The TPRM Lifecycle in Typical Large Enterprises
Step 1. Identification
- Objective: Identify all third-party relationships that impact business operations.
- Activities: Catalog vendors, suppliers, and service providers.
For existing vendors, organizations typically use several approaches:
Utilize Existing Information: Organizations often gather vendor data from spreadsheets and other sources when implementing third party cyber risk management software.
Integrate with Current Systems: Existing systems, such as Configuration Management Databases (CMDBs), Single Sign-On (SSO) providers, contracts, and procurement platforms, often contain valuable vendor information. Organizations can connect to these systems to centralize their vendor inventory in one software solution.
Carrying Out Assessments or Interviews: A brief assessment directed at business owners across departments—such as marketing, HR, finance, sales, and R&D—can help uncover the tools currently in use within the organization.
To identify new third parties, many organizations implement a self-service portal as part of their TPRM program. This portal allows business owners to build their inventory and can be shared via links from your intranet or SharePoint. Self-service portals also help collect preliminary information about new vendors, including:
- Personal information involved
- Vendor name
- Contact Information of Primary vendor (email, phone, address)
- Business details
- Engagement scope
- Hosting details
- Privacy Shield
- Scheduled procurement date
- Types of data involved
- Prior security reviews
- Prior Certifications
Step 2: Evaluation and Selection
In the evaluation and selection phase, organizations review Requests for Proposals (RFPs) and choose the vendor that best meets their needs. This decision is influenced by various factors unique to the business needs and requirements.
Step 3. Risk Assessment
Vendor risk assessments can be time-consuming and resource-intensive. To streamline this process, many organizations utilize third-party risk exchanges to access pre-completed assessments. Regardless of the approach, the primary goal remains the same: to understand the risks associated with each vendor.
- Objective: Evaluate the potential risks associated with each third party.
- Activities: Conduct security, financial, and compliance assessments. You can carry out a vendor risk assessment or third-party risk exchange based on your resources.
- Common standards for evaluating vendors include:
- ISO 27001 & ISO 27701
- SIG Lite & SIG Core
- NIST SP 800-53
- CSA CAIQ
Additionally, there are industry-specific standards such as:
- HITRUST
- HECVAT
Step 4. Due Diligence and Onboarding
- Objective: Thoroughly vet third parties before formal engagement.
- Activities: Verify credentials, conduct background checks, and integrate third parties into business systems.
Step 5. Contract Management
- Objective: Establish clear and enforceable contracts.
- Activities: Draft contracts with explicit terms for security, compliance, and performance expectations.
Step 5. Continuous Monitoring
- Objective: Monitor third-party performance and compliance continuously.
- Activities: Regular audits, performance reviews, and real-time monitoring of relevant metrics.
Step 7. Incident Management
- Objective: Respond to and mitigate any issues arising from third-party interactions.
- Activities: Implement incident response plans and corrective actions.
Step 8. Reporting and Review
- Objective: Maintain transparency and improve third-party relationships.
- Activities: Regular reporting on third-party performance and annual reviews of the TPRM process.
Step 9. Offboarding
- Objective: Securely terminate third-party relationships when necessary.
- Activities: Cancel access to any accounts or apps or physical entry to premises. Ensure the third party deletes intellectual property or sensitive data from any servers or devices.
Why Is the Current Process Broken?
As we explore the landscape of third party cyber risk management (TPRM), several challenges emerge that underscore the need for a shift in how businesses approach these crucial processes. Let’s dive into these challenges:
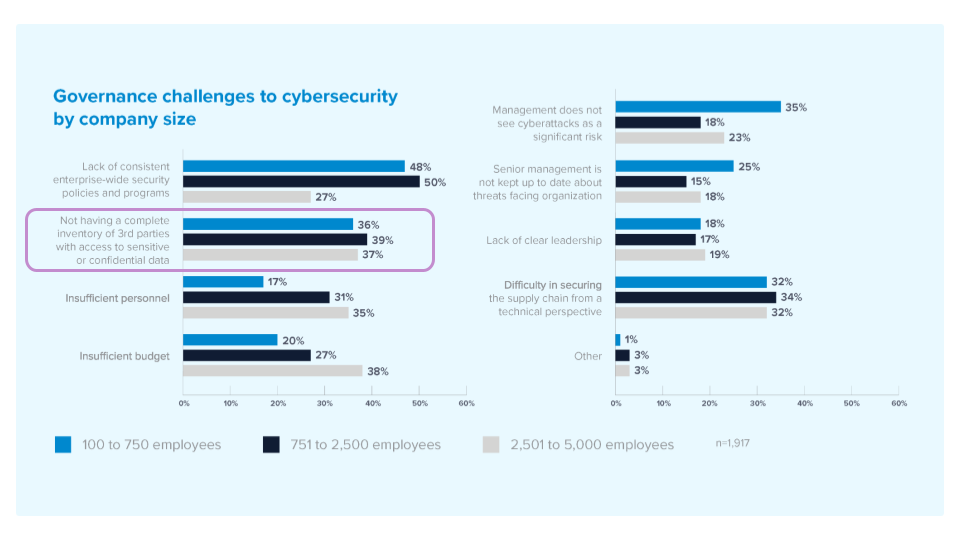
Challenge #1: Misguided Tiering and Incomplete Inventory of Third Parties
- Current State: Third parties are often ranked based on contract value rather than actual risk and struggle to maintain a complete inventory.
- Problem: A report by Barracuda highlights a critical issue: many organizations do not maintain a complete inventory of third parties that have access to sensitive or confidential data. This oversight and a limited understanding of which third-party vendors represent the highest risk can result in significant vulnerabilities.
Challenge #2: Lack of Automation and Scalability
- Current State: While many firms believe they have robust third-party risk programs, the reality often paints a different picture.
- Problem: Managing thousands of third-party relationships with a limited team can be overwhelming. Without automation, scaling the TPRM processes to handle increasing third-party numbers becomes an uphill battle, leaving teams stretched thin and risks unmanaged.
Challenge #3: Inadequate Prioritization
- Current State: It’s common practice to collect findings from all third parties without a clear strategy for action.
- Problem: This results in a mountain of data with little guidance on prioritizing risks. Organizations struggle to identify which issues to tackle first, which can delay response times and increase exposure to potential threats.
Challenge #4: Manual and Resource-Intensive Processes
- Current State: TPRM teams spend considerable time manually analyzing data from various third parties.
- Problem: The reliance on manual processes slows down the risk assessment and increases the likelihood of errors. This labor-intensive approach is inefficient and can lead to inconsistent risk management practices across the enterprise.
Challenge #5: Prohibitive Costs
- Current State: Many organizations use multiple solutions to manage third-party risks, each adding to the overall cost.
- Problem: The cost-per-vendor pricing model makes conducting thorough risk analyses for all third parties financially unsustainable, especially as the number of third-party relationships grows. This financial burden can lead to gaps in risk coverage and uneven risk management efforts across the board.
While traditional TPRM methods have served their purpose in the past, they are increasingly mismatched with the realities of modern business dynamics. The manual nature of traditional practices, the inadequacy of infrequent inspections, and the confusion caused by tool disarray collectively contribute to a TPRM approach that is often reactive, inefficient, and fragmented. As we move forward, addressing these flaws will be crucial in developing more robust, proactive, and integrated TPRM strategies.
3 Key TPRM Best Practices
Numerous best practices exist for TPRM that can strengthen your third party cyber risk management program, whether you’re just starting to focus on TPRM or assessing how to improve your current strategy. We’ve identified three key best practices that apply to almost every company.
1. Prioritize risk management of third parties based on risk
Tier your third parties based on a quantified view of the risk they pose to your data, network, and revenue streams (especially single points of failure) and target risk management accordingly. Large corporations may do business with thousands of vendors; they must prioritize.
2. Take a unified view of first- and third-party risk
Many of the key risk scenarios exist for both. Third parties simply represent an additional attack surface. Malicious actors may target them to achieve the same outcomes they do for the first party (access to confidential data, to disrupt the organization’s operations, etc.). The solution: Orient toward third parties the same zero-trust controls you use for first-party threats. Make sure you always have a reading on the status of those controls.
3. Partner with your key third parties
First and third parties are in this together and must cooperate to succeed in security – and in business. That could include a continuous API connection from third to first parties to monitor the status of controls – or an agreement to more frequent updates to the traditional annual questionnaire for better TPRM.
Why You Should Invest in Third-Party Risk Management
Now is the time to modernize your third-party risk processes – you can convincingly justify a move to an efficient, comprehensive, risk-based approach to TPRM with these benefits:
1. Cost Reduction
A risk-based approach focuses your team on the most cost-effective way to conduct a TPRM program. Prioritizing third parties based on contract size (a common practice), for instance, can generate a costly wasted effort and still leave the organization vulnerable to attacks down the line. With an unfocused approach, some organizations engage multiple vendors on duplicative third party cyber risk management work.
2. Improved Security
Risk-based TPRM guides the deployment of controls for maximum value in risk reduction. A zero-trust solution implemented to handle TPRM has force-multiplier benefits against system intrusion from any direction.
3. Regulatory Compliance
Meeting compliance standards such as SOC 2 or ISO 27001 and 27002 benefits both the first- and third parties in enforcing all-around risk preparedness. The difficulty comes in monitoring compliance at scale over a large body of vendors and suppliers responding to questionnaires, attestations, or other documentation. Look for a TPRM solution that includes AI-driven document management to streamline the process.
Adopt a Risk-Driven Approach to TPRM with SAFE
The traditional methods of third party cyber risk management have shown their limitations in today’s dynamic business environment. Ignoring the critical gaps in these practices—such as overreliance on incomplete data, the reactive nature of risk management, and the lack of integrated risk assessment tools—can expose organizations to significant security breaches, operational disruptions, and compliance failures.
The highlighted issues underscore the urgent need for enterprises to evolve their TPRM strategies beyond the conventional approaches. It’s not just about patching up vulnerabilities but transforming how we perceive and manage these third-party relationships from reactive to proactive, ensuring that risk management keeps pace with the complexity and speed of modern threats.
Our SAFE TPRM solution is the product of careful listening to the needs of the marketplace to advance beyond the ineffective approaches to TPRM. SAFE TPRM running on the SAFE One platform offers these key benefits:
- The only data-driven, unified platform for managing all your first-party and third-party cyber risks in real-time.
- Based on the FAIR standard, SAFE One estimates a range of dollar impact and breach likelihood of different cybersecurity risk scenarios to quantify risk, enabling CISOs to tier their most critical vendors based on loss exposure.
- Most complete third-party risk assessment, covering external and internal assets, combining inside-out and outside-in scans via integrations with all the popular security tools
- First to extend zero-trust to TPRM, driving real-time visibility into how controls are configured to minimize breaches originating at third parties.
- Focus on the top ten controls for managing third-party risk, the result of extensive research into security incidents involving third parties.
- AI-powered to build and scale TPRM at your pace – automates the vast majority of TPRM chores such as ingestion of questionnaires.
Let us show you how to make your move to risk-based TPRM. Schedule a 1:1 demo today!


