Top 10 Cybersecurity Frameworks to Minimize Your Cyber Risk
Just remember: Compliance with a framework alone does not directly reduce risk
Organizations looking to get their arms around managing cybersecurity risks have some great choices for a cyber security risk management framework that will offer a ready-made risk management strategy and guidance on maintaining an effective security posture.
What Is a Cybersecurity Framework?
A cybersecurity framework is a set of best practices to achieve cyber risk management.
What’s cyber risk management? Maintaining an acceptable level of loss exposure through a combination of people, policies, processes and technologies.
In this blog post, we will introduce the 10 most commonly used frameworks and standards in cyber risk management:
- NIST CSF
- FAIR
- MITRE ATT&CK
- ISO 27001 (and 27002 update)
- NIST 800-53
- CIS Controls
- PCI DSS
- HITRUST
- COBIT
- FFIEC CAT
1. NIST CSF (National Institute of Standards and Technology Cybersecurity Framework)
By far, the most-adopted cybersecurity framework is a thorough and extensive compendium of recommended controls and best practices in 23 categories and 108 subcategories grouped under the headings of Respond, Detect, Protect, Identify, Recover and a new, superseding heading of Govern, described as “The organization’s cybersecurity risk management strategy, expectations, and policy are established, communicated, and monitored.”
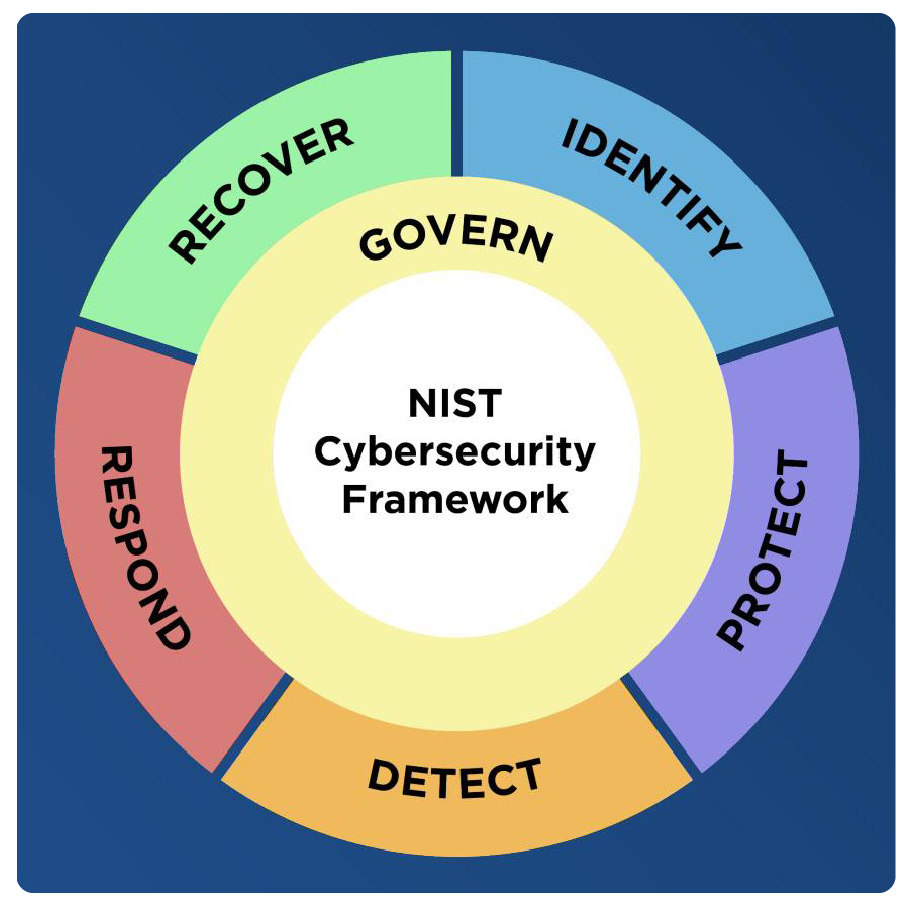
By far, the most-adopted cybersecurity framework is a thorough and extensive compendium of recommended controls and best practices in 23 categories and 108 subcategories grouped under the headings of Respond, Detect, Protect, Identify, Recover and a new, superseding heading of Govern, described as “The organization’s cybersecurity risk management strategy, expectations, and policy are established, communicated, and monitored.”
The release of Govern in the NIST CSF 2.0 update was a clear reorientation of the CSF from a strictly technical bias (that equates risk reduction with adding more controls) to a broader, risk-based approach that equates cyber risk with risk to the whole business (and encourages analyzing cyber risk in financial terms).
Among the recommended steps:
- “Determine your organization’s unique risks and needs. Discuss the current and predicted risk environment and the amount of risk your organization is willing to accept.”
- “Analyze risks at regular intervals and monitor them continuously (just as you would with financial risks).”
- Develop a cyber risk management strategy “based on your organization’s specific cybersecurity objectives, the risk environment, and lessons learned from the past and from others.”
Note that NIST also maintains a framework similar to the NIST CSF but tailored for government agencies: the NIST RMF (Risk Management Framework).
2. FAIR™ (Factor Analysis of Information Risk)
FAIR is the recognized standard for analyzing cyber risk in quantitative terms, recommended for risk analysis by the NIST CSF and other authorities. Unlike the NIST Cybersecurity framework, a list of best practices, FAIR is a model that describes how the component factors of risk can be quantified and set in relation to each other to produce an overall quantitative view of risk as frequency of cyber events (expressed as an annual percentage) and magnitude of financial impact (expressed in dollars). FAIR is an open standard unlike many solutions in the cyber risk management space that run on proprietary, black-box algorithms.
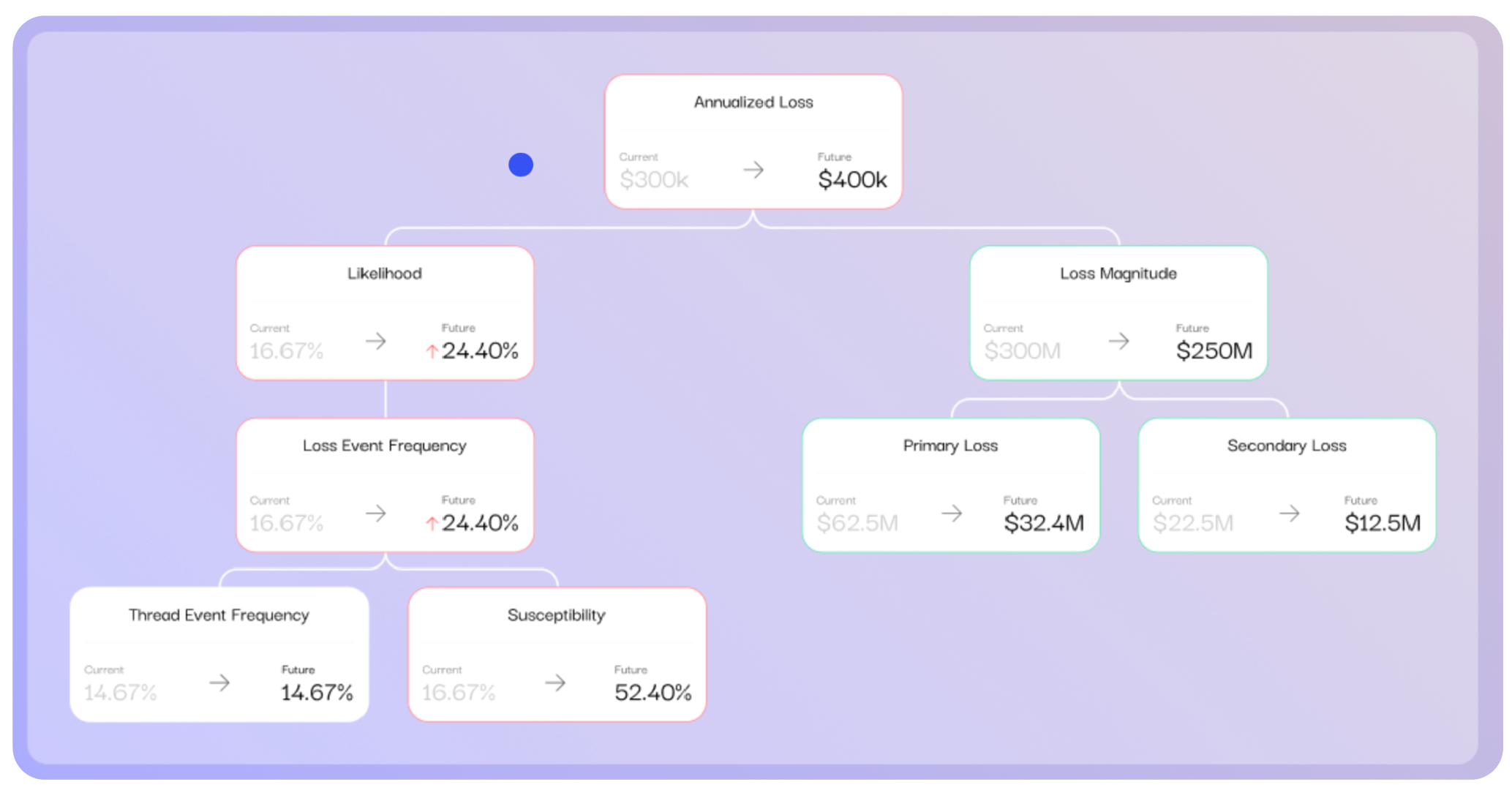
A FAIR analysis focuses on a cyber risk scenario with a specifically defined threat actor, attack vector, and asset at risk so that each analysis accurately addresses a real business problem.
Feeding FAIR analysis are two important sub-models:
This model provides explicit, quantitative descriptions of the control functions that affect risk, as well as the relationships and interdependencies between control functions. While the framework-compliance approach asks if a control is present or absent, FAIR-CAM takes a more nuanced approach, asking if a control is working at its intended efficacy or in a variant state, for example anti-malware gone out of date. FAIR-CAM Loss Event Functions feed the various factors in FAIR, bringing quantification even to some areas that formerly were left to guesswork by subject matter experts – notably Susceptibility to successful attack.
This model expands and focusses the Loss Magnitude side of the FAIR model by categorizing and quantifying risk as a CFO might, using 10 categories that go into depth on costs of a cyber event, ensuring a high level of accuracy that could stand up to regulator scrutiny (for instance, if the materiality of the incident were in question.) 701
3. MITRE ATT&CK
The MITRE ATT&CK framework is the bible of cyber threat intelligence, a knowledge base that catalogs a vast number of cyber threat-actor groups, their tactics and techniques. If you hear about a new threat, you can consult ATT&CK to understand the likelihood of the threat hitting your network. Or conversely, start with the technique and understand the bad actors. The framework also tracks how threats gain a foothold and move laterally through your network to help you plan your defenses.
4. ISO 27001 and 27002
Organizations in financial services, web services or others that handle sensitive data often also seek to reassure customers and management with certification in the ISO 27000 set of standards, particularly ISO 27001 (and an update ISO 27002), requirements for information security management systems (ISMS) and ISO 27005, requirements for implementation of information security based on a risk management approach. This standard mandates a risk assessment but doesn’t specify what method to follow.
5. NIST 800-53
An authoritative listing of cybersecurity controls. You might use this standard with FAIR-CAM for a complete picture of your controls environment.
6. CIS Controls
The CIS Controls are an 18-category set of best practices, popular as a lightweight framework. It includes a risk assessment process aimed at meeting a legal-oriented “due care” or “reasonableness” standard.
7. PCI DSS
Under this standard, businesses that handle credit card data must perform an annual risk assessment using one of the recognized standards from NIST or other authority.
8. HITRUST CSF
HITRUST CSF offers an “assess once, report many” approach by combining HIPAA, GDPR, IS0 27000, COBIT and many more standards in one certifiable framework. HITRUST also offers a Threat Catalogue that matches threats to relevant controls and assesses their resistance strength. HITRUST CSF regularly updates to account for emerging threats.
9. COBIT
COBIT (Control Objectives for Information and Related Technologies) is a framework for developing, implementing, monitoring, and improving IT governance and management practices such as risk management and performance management, with an emphasis on aligning IT processes with business goals.
10. FFIEC CAT
Banks and other regulated US financial institutions follow the Financial Institutions Examination Council Cybersecurity Assessment Tool (FFIEC CAT) as part of their regular examinations. The framework provides a structured approach to gauge how well an institution meets risk management norms. The tool covers two main components, an Inherent Risk Profile assessed against several risk factors, and a measure of Cybersecurity Maturity, based on the controls implemented.
5 Benefits of Cybersecurity Management Frameworks
Adoption of industry-recognized standards and frameworks like NIST CSF, FAIR, ISO wins you these benefits:
- A list of best practices to implement and a roadmap for increasing your maturity level with implementing more approved practices.
- A systematic way to approach risk management, ideally with the goal of prioritizing security investments
- Meet regulatory or other compliance requirements. Industries required to meet certain cybersecurity standards – such as for handling sensitive personal financial or health data – can point to compliance with recognized standards as a defense.
- Enable audits for a merger or other situation requiring a due diligence check on cybersecurity, following a cybersecurity risk management framework is a necessity.
- Reporting to stakeholders with a track record of compliance with a framework reassures investors or the board of directors that good governance is followed.
How to Get the Most Risk Reduction out of Cybersecurity Standards and Frameworks
Except for FAIR, the standards and frameworks covered here have a limitation. They encourage a compliance-based mentality: Add the recommended controls or processes to your stack and you will reduce risk; add more and you will have even less risk.
The cybersecurity world is moving more in the direction of FAIR: a risk-based approach. It starts with prioritizing among risks based on a quantitative analysis of the loss exposure they present. Then prioritizing among controls to add (or subtract) them for how they effectively reduce those risks.
Another emerging principle for managing cyber risks: Comprehensive, continuous monitoring of both risks and controls effectiveness—an approach that demands a high degree of automation. The old expectation of an occasional risk assessment has been far outpaced by the reality of the threat landscape.
The frameworks and standards we know will still have relevance as baselines – but the risk-based future of risk management will move them into a whole new paradigm.
SAFE’s SAFE One platform automates FAIR risk analysis as well as controls monitoring via FAIR-CAM and financial potential impact data via FAIR-MAM. No matter what framework you now use – NIST CSF, CIS, ISO – we can import your controls lineup to our platform and start you on an automated, risk-based program for cyber risk management today. Contact us for a demo.



