How One Client Transformed Cybersecurity to Outsmart Threat Groups
Aligning Risk Management, SOC, Pen-Test and other teams around a common view of cyber risk
We frequently hear from cyber risk management teams about their challenge to make cyber risk analysis actionable across the other teams tasked with cybersecurity. We recently worked with a client who successfully made the transition to that aspirational goal of “risk-based security” – and it’s a story worth re-telling.
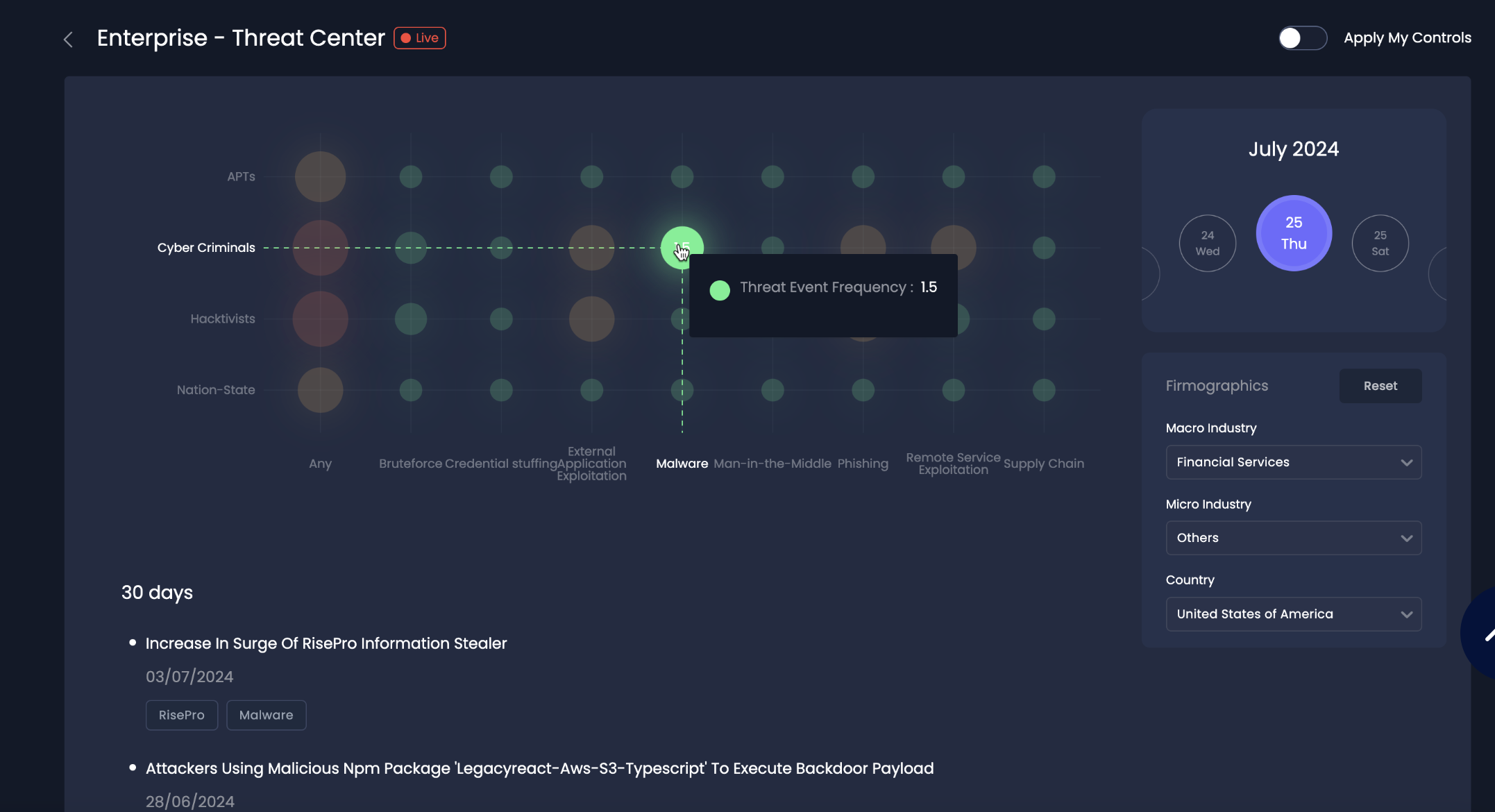
SAFE One platform, Enterprise Threat Center
The client initially came to us with the desire to improve their reporting to the board. Reporting was focused on the eight most threatening threat actors. The board wanted to see a more robust program that serviced all relevant teams in pursuing a shared strategy to drive down risk across the enterprise. The board further directed that the program be quantitative and automated.
The teams lineup:
>>Cyber Risk Management – Coordinates threat analysis, risk reporting and Treatment Planning.
>>Security Operations – Oversees the monitoring and detection of threats in the environment.
>>Penetration Testing (Pen Test) – Validates risk scenarios and provides actionable insights for control adjustments.
>>Risk Reduction – Implements targeted risk treatment plans.
Knowing the client’s focus on threats, we introduced them to the SAFE One platform’s Enterprise Threat Center, with its detailed information on hundreds of threat actors and their techniques, as well as real-time data on Threat Event Frequency (TEF) pulled from 100-plus integrations with security tools. TEF, plus the status of controls captured in FAIR-CAM Controls Center are two of the critical factors feeding FAIR quantitative risk analysis on the platform.
The Threat Center became the central point of contact for the collaborative effort among teams that the board wanted to see.
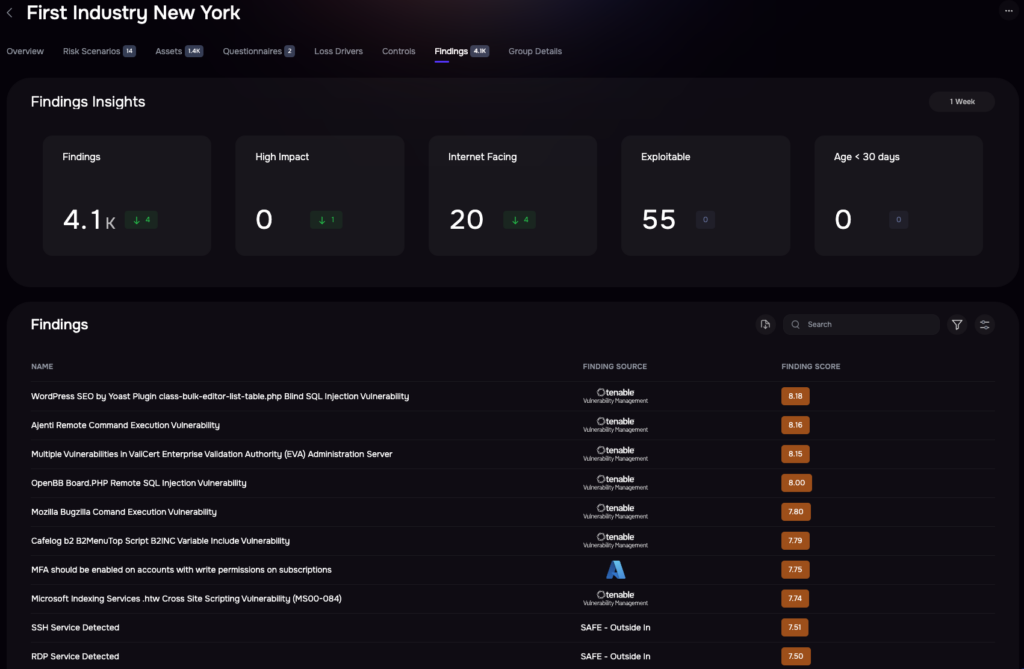
Tracking findings on the SAFE One platform
Program Workflow:
- Threat Identification and Monitoring:
- The Cyber Risk Management team collaborates with the Security Operations team to assess current and emerging threat actors using the Threat Center.
- Threat information is cross-referenced with the organization’s environment via its SIEM (Security Information and Event Management) system to identify relevant Threat Groups of Interest.
- Risk Scenario Development and Validation:
- Identified Threat Groups are monitored to analyze their behaviors and potential impacts. The platform’s Groups function creates unified views for each grouping of bad actors.
- The Threat Center generates key risk scenarios modeled on threat intelligence. The Pen Test team validates the scenarios through targeted penetration testing.
- Results from penetration tests are used to refine the FAIR-CAM Control Library, ensuring controls are appropriately tuned to counter identified threats. Where they find deficiencies, they make control improvements, close vulnerabilities or respond to misconfiguration errors.
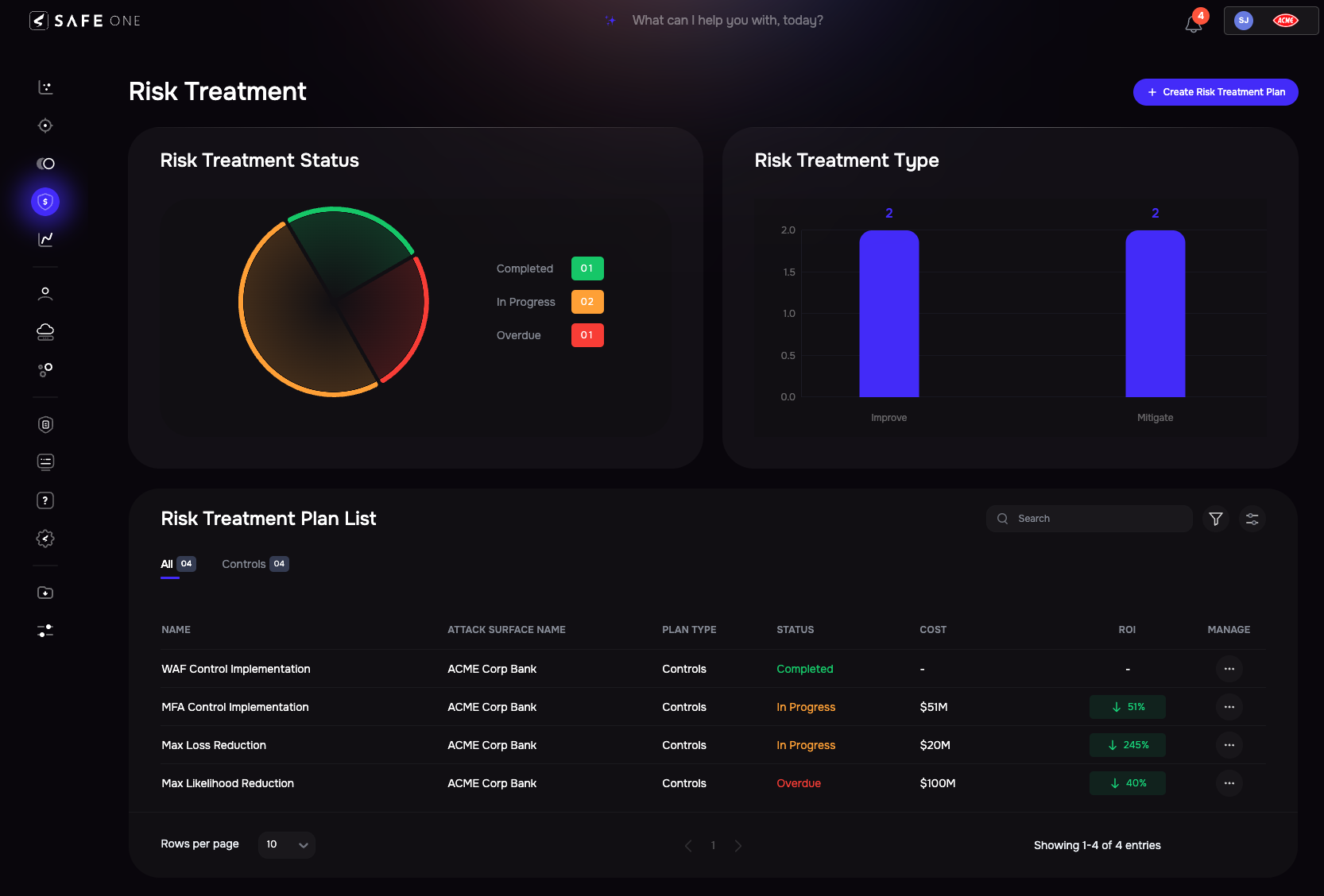
Risk treatment planning on the SAFE One platform
- Risk Treatment:
- SAFEOne’s Risk Treatment Plans are leveraged to prioritize and track remediation efforts.
- Treatment plans outline specific controls or findings to address, focusing on reducing risks associated with high-priority threat groups. The platform’s Findings Prioritization automatically ranks findings and associates them with relevant controls.
- Using the platform’s “What If?” and cost-benefit analysis functions, the team assesses different treatment plans for effect on risk for specific scenarios or across the enterprise.
- In the last step, the Attack Surface Reduction team remediates the vulnerabilities, closes configuration gaps and works with control owners to put in people or processes to improve maturity.
- Progress is measured and reported quarterly, highlighting achievements and areas requiring further attention, aided by the platform’s See What Changed functionality.
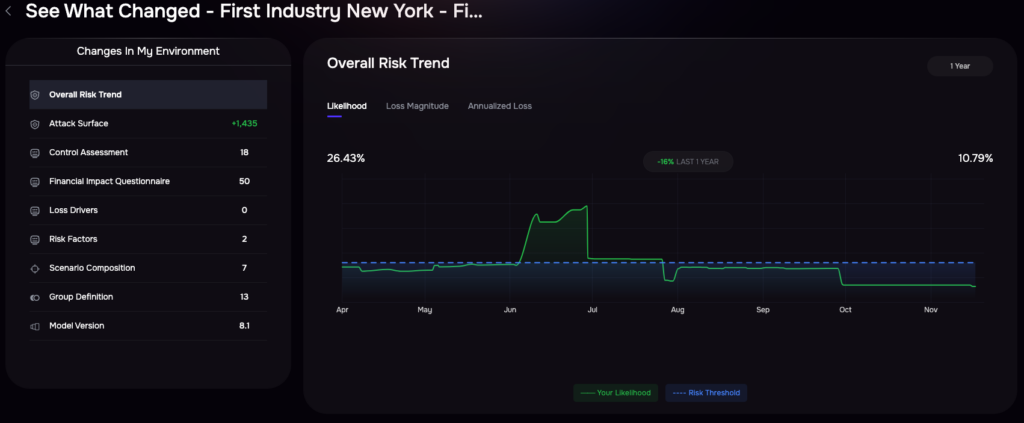
SAFE One Platform: See What Changed
The team showed initial results to the CEO, who was pleased enough to order quarterly reporting to the board — with SAFE One’s output as the core component – showing-quarter over-quarter improvement in measurable risk for each threat group and in the aggregate.
See how SAFE’s SAFE One platform can bring risk-based prioritization to your cybersecurity operations – Schedule a demo now.



