Webinar, July 23: Don’t Be the Next Third-Party Risk Victim
Let’s learn the lessons from the Change Healthcare hack and build a TPRM program that works
The recent attack on UnitedHealth Group’s subsidiary, Change Healthcare, the dominant clearinghouse for medical insurance claims and payments in the US, disrupted patient care, impacted cash flow, and potentially exposed the sensitive health information of over one-third of U.S. citizens. The estimated cost? A staggering $2.5 billion.
Join Us for a Webinar:
How NOT to Be the Next Change Healthcare
Build a Third-Party Risk Management Program That Works
July 23, 2024
10 AM PT/1 PM ET
Featured speakers:
- Saket Bajoria, Chief Product Officer
- Vince Dasta, Senior Partner, Risk Strategy
- Resha Chheda, VP, Product Marketing
The attack also exposed the vulnerabilities of traditional third party cyber risk management (TPRM) for cyber, which is still manual, compliance-driven, and reactive. Many healthcare providers were driven to the brink of financial crisis because Change Healthcare was a single point of failure and an essentially unmanaged risk. A large organization today may engage with a huge number of third-party software vendors and only monitor a small fraction of them because it can’t practically handle third party cyber risk management at scale.
But there is a better, more effective way to build, automate, and run a cybersecurity TPRM program.
Join us for a webinar to explore:
- Key takeaways and lessons from the Change Healthcare breach
- Best practices for a risk-driven TPRM program that goes beyond compliance checklists
- An AI-driven approach with SAFE that automates and scales your TPRM strategy
Problems of Conventional TPRM
Third-party (or supply chain) risk management for information security as it is commonly practiced fails in conception and execution. Among the flaws:
- Compliance-focussed, not risk-based
- No real science behind any methodology
- Inconsistent risk reporting among applications
- Third-party questionnaires take way too long to complete and process – and then only give a snapshot of a moment in time
- Outside-in scanning applications produce many false positives
- Cybersecurity risk ratings services do not provide any insight into a third-party’s internal control environment
- No actionable insights generated
Learn more in our third party cyber risk management (TPRM) whitepaper.
The candid truth is that these practices persist only because they have become standard practice and are required for audits and compliance reporting. The end result is that a CISO typically can’t confidently answer to “What is our most critical third-party risk, and how efficient is our program in managing that risk?”
SAFE Is the Leader in TPRM for Cyber
SAFE is the category leader in Third-Party Risk Management, offering the first AI-powered third party cyber risk management solution for a quantitative, risk-based approach to TPRM that aligns to business needs. We equip businesses with the benefits of outside-in security ratings, questionnaire-based assessments, zero-trust, and inside-out assessments. Using our unified platform, SAFE TPRM, enterprises can finally manage and mitigate their supply chain risk with confidence.
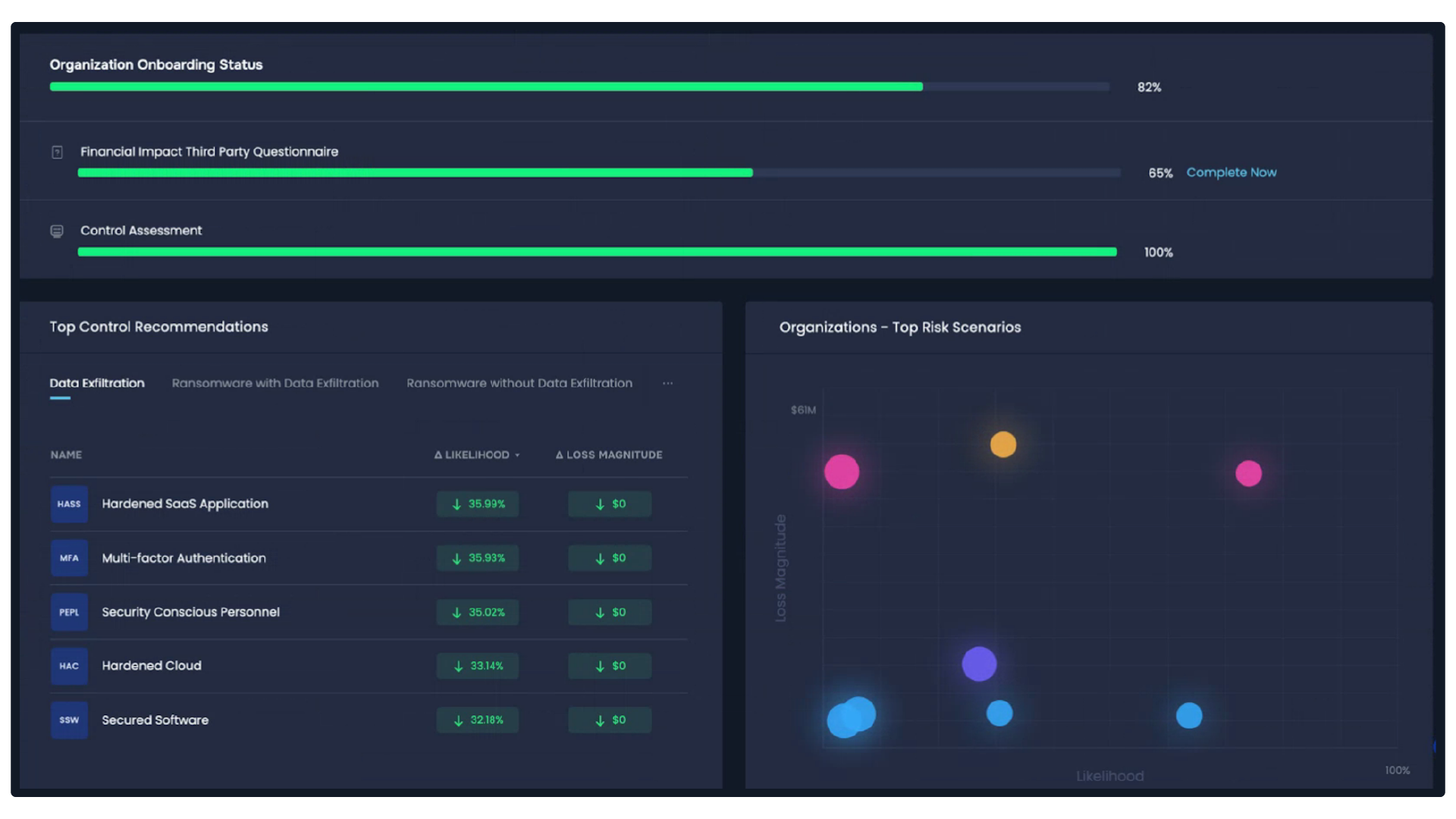
Key Functions/Features of SAFE’s Third-Party Risk Management Solution
1. Prioritize third parties based on risk to your business
It’s the most effective way to get your arms around an extensive supply chain: tier vendors based on loss exposure to your organization. SAFE TPRM assesses the dollar impact and likelihood of the most frequent cyber risk scenarios so organizations can in turn prioritize the most impactful controls to mitigate third-party risk.
2. Focus on critical third-party controls
Derived from extensive research of current and past third-party cyber attacks, we have identified the most critical controls to focus your defense. This eliminates duplication of effort and the emphasis for third parties to respond to questionnaires, shifting the focus from quantity to quality of control assessments.
3. Partner with third parties to improve their security programs
Supply chain partners can access our SAFE One risk management platform to visualize their cyber risk exposure on an “inside-out” basis, enhanced by AI-assisted training and onboarding modules.Assessing effectiveness of zero-trust controls, SAFE One platform
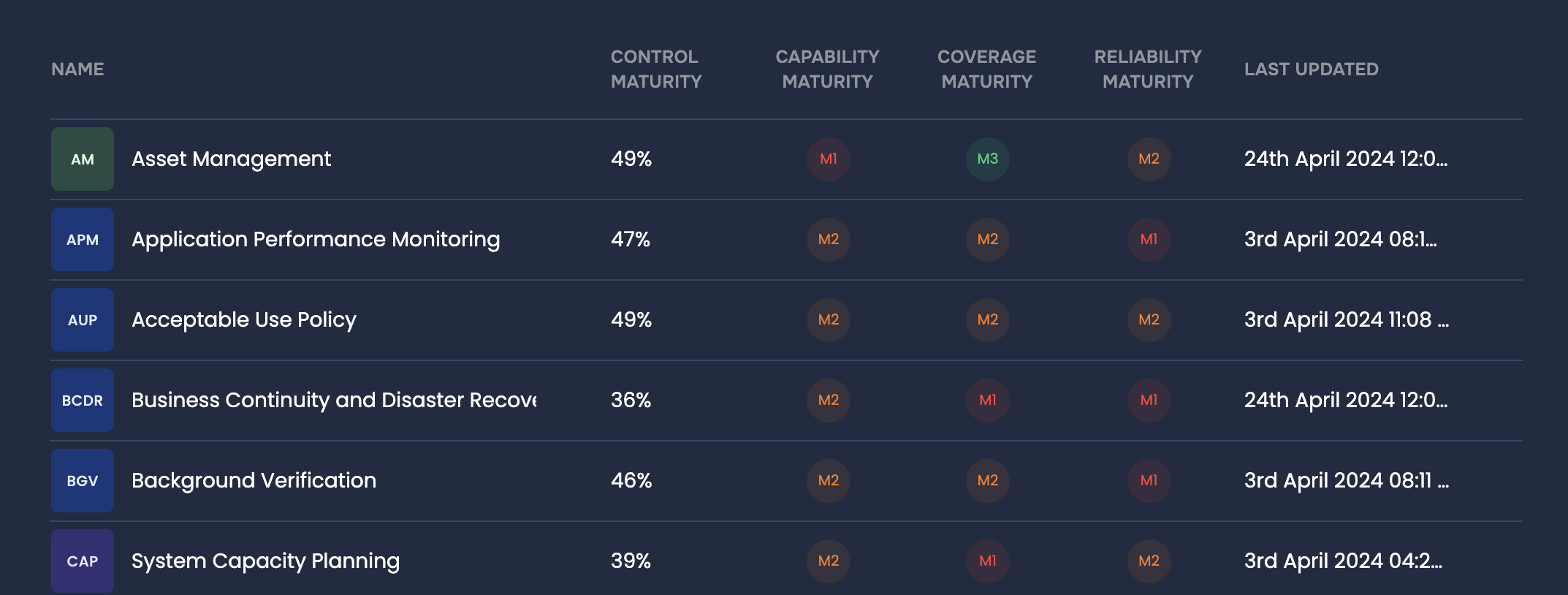
4. Manage third-party impact using zero-trust controls
Always assume your third-parties have not addressed critical security exposures, and that your enterprise needs to safeguard itself. Initiate a zero-trust controls strategy – we’ll guide you to the right set of controls and provide real-time monitoring of controls effectiveness for risk reduction.
5. Reduce cost while covering all your key third parties
SAFE TPRM pricing is independent of the number of vendors – add an unlimited vendor count at a fixed price.
Join us to explore a new, automated approach to TPRM that prioritizes risk, streamlines processes, and effectively manages vendor networks.
Webinar: How NOT to Be the Next Change Healthcare
Build a Third-Party Risk Management Program That Works
July 23, 2024
10 AM PT/1 PM ET
REGISTER NOW!



