Webinar on Demand: Learn from GSK’s Risk-based TPRM Strategy
Plus, see a demo of the SAFE One TPRM platform for a holistic view of third party risk data
If you’re looking for both a strategic and an operational approach to third party cyber risk management (TPRM), this webinar covers all angles. Marek Jakubczak, Cyber Risk Leader, GSK, tells how the global pharmaceuticals giant is restructuring cyber risk management to drop the traditional but ineffective techniques of vendor risk management and move to a risk-based, quantitative, next generation program. Marek is joined by Ram Vemula, SAFE’s Product Management – Head of Partnerships, to discuss how the SAFE TPRM solution advances that shift to the next generation.
You can watch this webinar on demand:
FAIR Institute Webinar Sponsored by SAFE
How GSK Built a Next-Generation TPRM Program and Tooling
The problem in pharma is urgent: a 27% increase year over year in reported cyber incidents in 2023, with 48% of the breaches theft of intellectual property. “It’s a huge business for cyber criminals,” Marek said.
And it is focussed increasingly on third parties. “Criminals will attack a smaller vendor with less cybersecurity protection” to get at the first parties, the large companies who are in effect running huge attack surfaces with thousands of vendors (60,000 for GSK).
GSK has followed the standard tactics for TPRM, “yet all we do is not helping us reduce risk.” He presented this long list of failures and two successes.
| NOT Working | Working |
| • Questionnaire based | • Vendor classification (critical, high, medium, low) |
| • Time consuming (avg 2-4 weeks) | • Vendor relationships |
| • Point in time | |
| • Not 100% reliable | |
| • Tools that scan the external presence | |
| • Too many false positives | |
| • No actionable insights based on risks | |
| • Don’t want to become vendor’s security department | |
| • No strong partnership with vendors |
The promising “Working” steps were a beginning at prioritization and getting access to the vendor’s data. But the overall sense at GSK was they were a “chasing company” not leading in a proactive way.
GSK launched an initiative to define and implement the “NextGen TPRM.” “We are looking into scientific methods of quantifying cyber risk to rely much more on the technology and the data…We are partnering with the FAIR Institute, SAFE and other partners.”.
The team defined three core attributes of a new approach:
- Data-driven
- Risk-based
- Continuous
Clearly, neither TPRM questionnaires nor scoring systems nor external scans could meet those criteria.
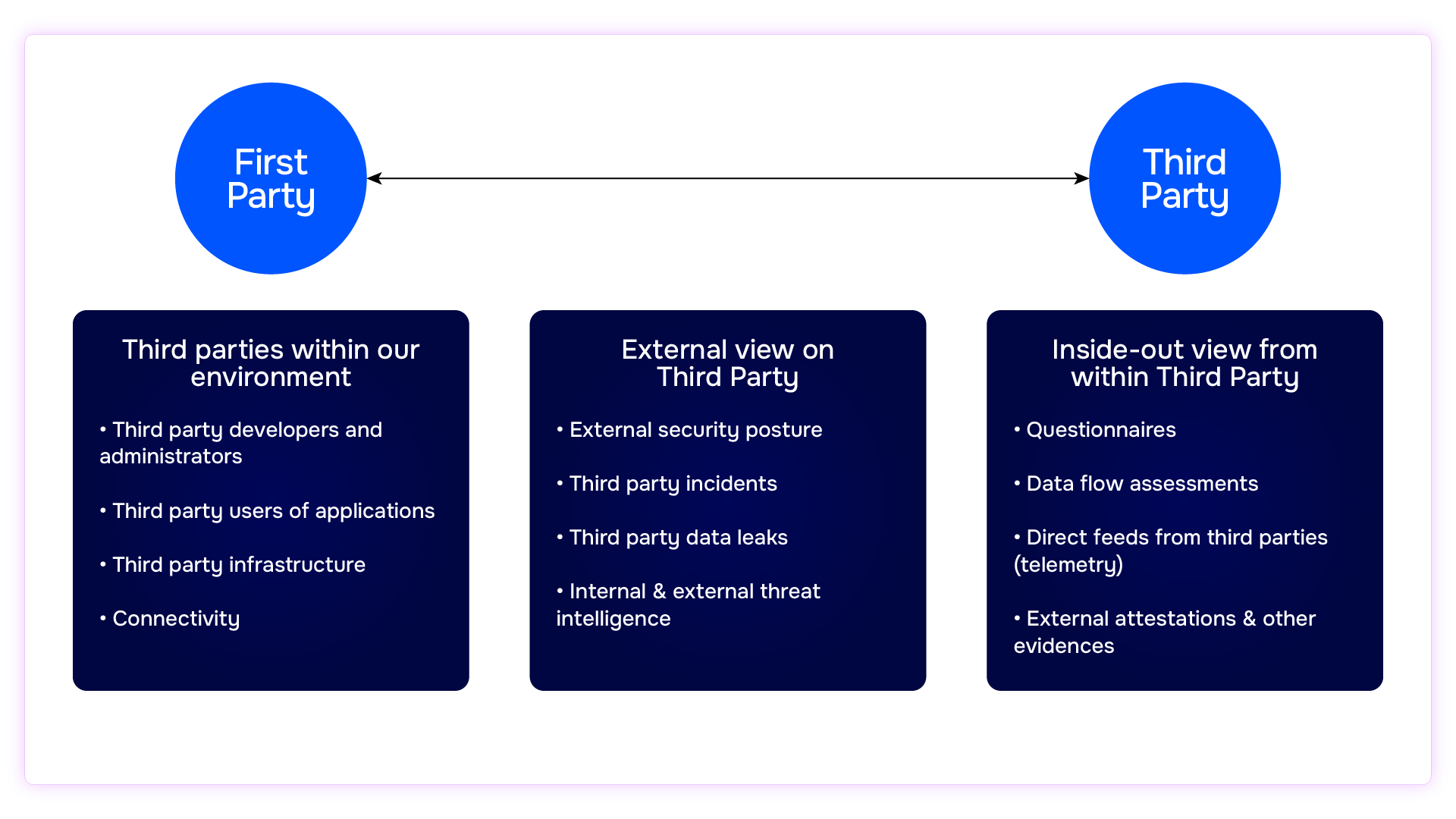
The GSK team grouped their third-party ecosystem three ways:
- Third parties within their environment
- Third parties viewed from outside in
- Third parties viewed from inside out
And under each heading listed the data sources that would give them a direct view into risk data, such as, telemetry, third party incidents, and connectivity details.
Some initial projects:
- Keep questionnaires but minimize questions and automate ingestion
- Automate with LLM the reading of external attestations
- Mapping data flow from first party to third parties “so we have clarity where our data is, what are the controls and what are the effectiveness of those controls (not based on questionnaires).”
Demo of SAFE’s SAFE TPRM Platform
Ram Vemula, third party cyber risk management product line leader, gave a detailed look at the SAFE TPRM third party cyber risk management solution – but really, do yourself the favor of watching the webinar video as SAFE’s solution is highly visual and highly dynamic and interactive.
To cover a few of the features that Ram demonstrated:
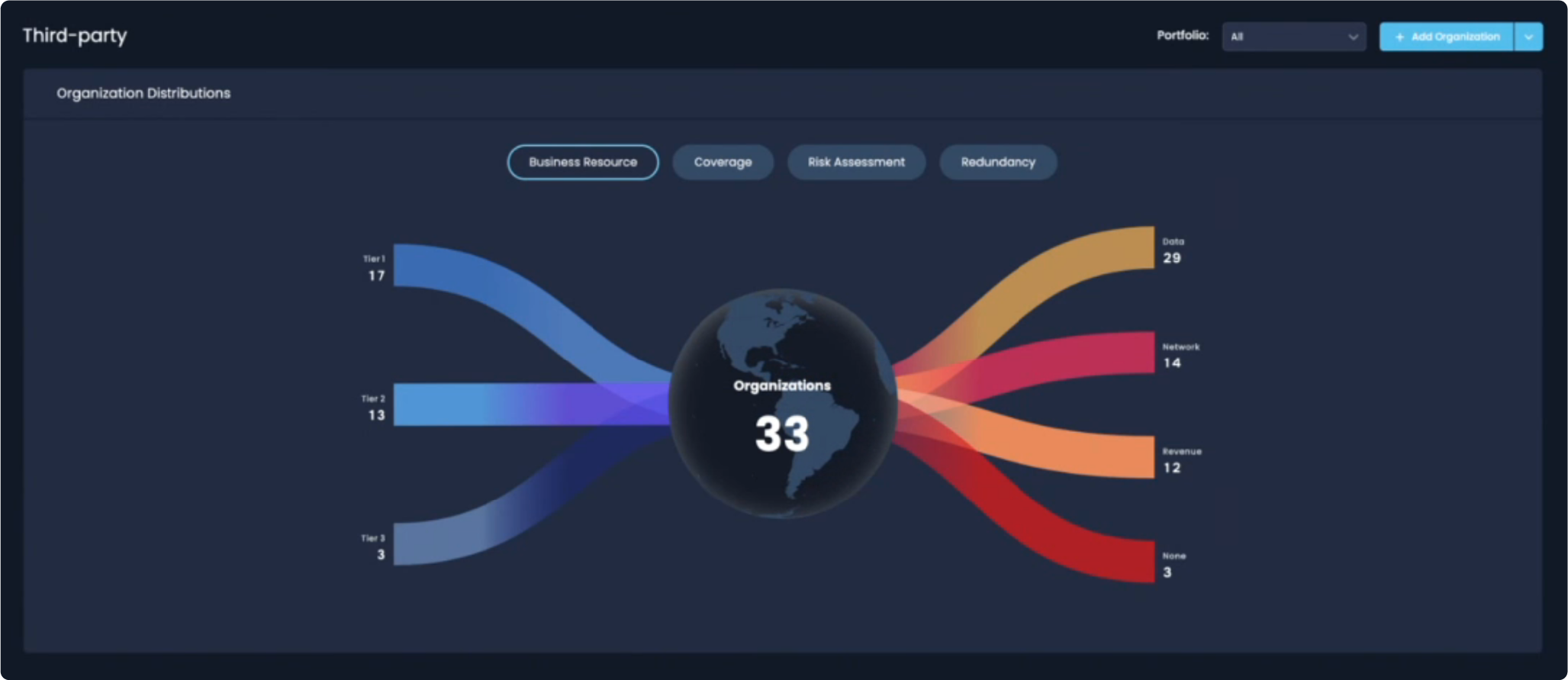
Snapshots of TPRM
This colorful image gives an at-a-glance report on a set of 33 third parties, tiered on the left in blue by their criticality and on the right a breakdown by risk factors (access to network processing sensitive data, etc.) This view can be flipped to a view of what stage of risk assessment each vendor is in or the redundancy level of a third party.
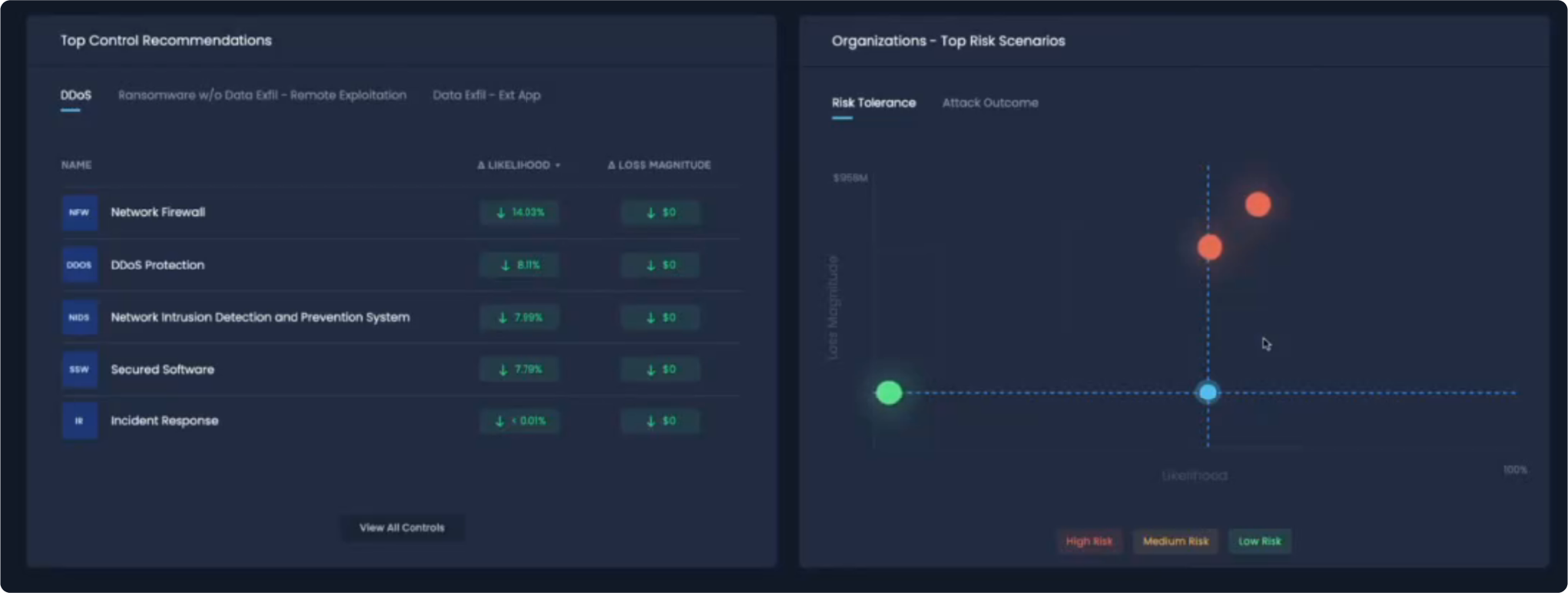
3 Risk Scenarios Out of the Box
As Ram explained “the essence of what we provide is visibility into breach likelihood and loss magnitude.” SAFE TPRM comes at onboarding with three risk scenarios (ransomware, DDoS, data exfiltration) out of the box so clients can start gaining value right away. Onboarding triggers an outside-in scan of all the web-facing assets and reporting of critical findings – followed by recommendations on top controls to implement or raise their maturity level to start burning down risk.
A Holistic Solution to the TPRM Problem
Questionnaires, scans, ratings, attestations – SAFE set out to solve the noise problem in third party cyber risk management that forces risk managers to make sense of all the different and incompatible inputs. “SAFE is a holistic TPRM platform,” Ram said.
The platform has a standard library of 65 controls derived from FAIR-CAM (FAIR Controls Assessment Model). For every third party, the platform assesses the maturity of all 65 across three dimensions: Capability, Coverage, Reliability. Assessments are performed by ingesting
- outside-in security risk ratings
- industry standard questionnaires (NIST CSF, etc.)
- compliance attestations (SOC 2, etc.)
- the first party’s customer questionnaire
- inside out, real-time telemetry
SAFE TPRM normalizes all this to measure control maturity resulting in highly accurate calculation of likelihood for risk scenarios.
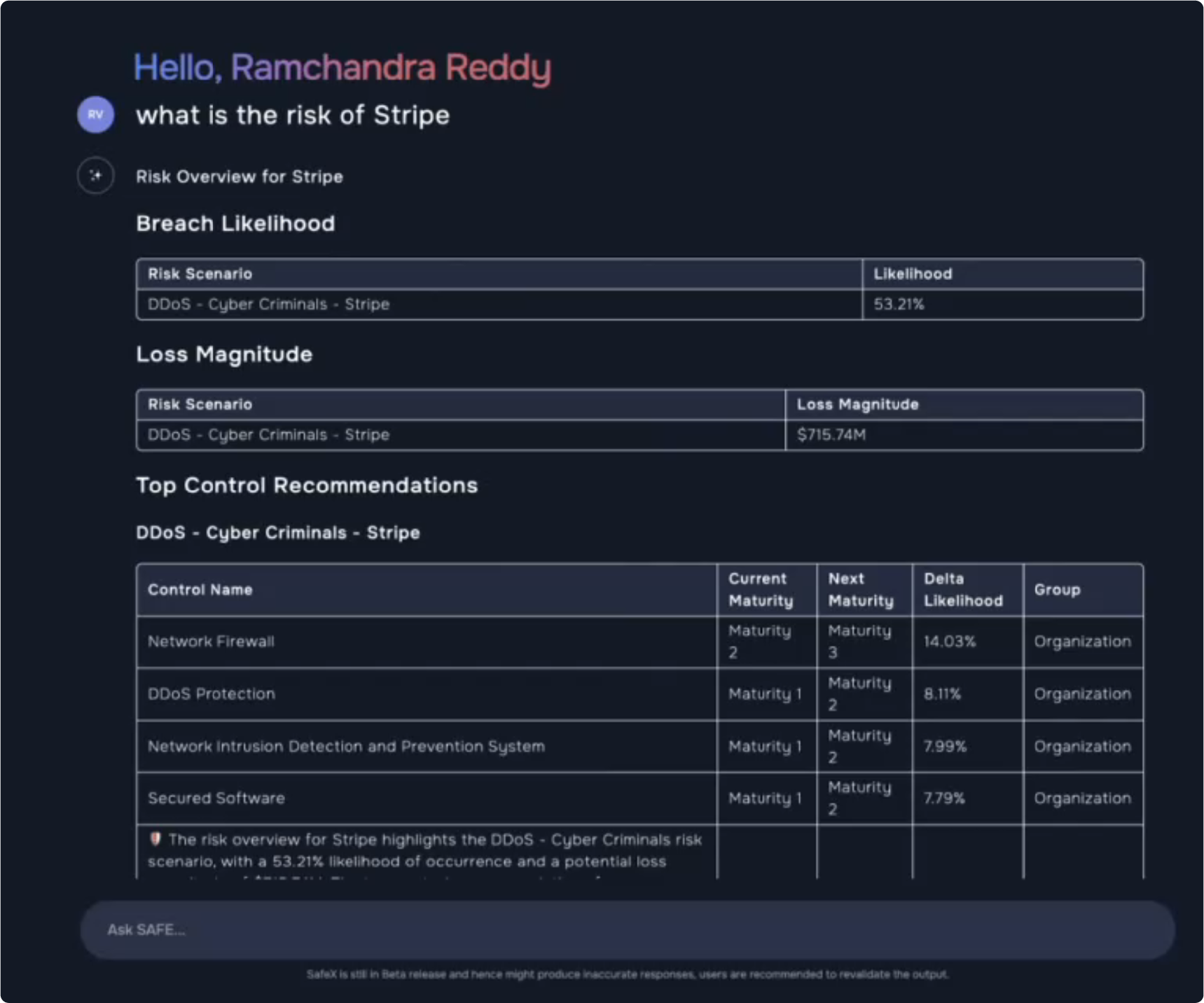
GenAI for TPRM
“We have taken an AI-centric approach,” Ram said. As an example, this detailed output was triggered by AI immediately responding to a simple command:
You can watch this webinar on demand:
FAIR Institute Webinar Sponsored by SAFE
How GSK Built a Next-Generation TPRM Program and Tooling
Want to learn more about SAFE TPRM? These resources might be useful:
- SAFE TPRM Solution Brief
- SAFE TPRM Datasheet
- Why Cybersecurity Risk Ratings Are Just a Feature, Not the Full Picture
Ready to uplevel your Third-Party Risk Management? Request a TPRM demo with a cyber risk expert today!



