Webinar on Demand: Introduction to Third-Party Cyber Risk Management
Learn where TPRM has been stuck — and a promising new way forward.
If you’re looking for a foundational understanding of third party cyber risk management, SAFE recently hosted a webinar that you can watch on demand that covers where TPRM has been stuck and shows a promising new way forward.
The crisis in vendor risk management isn’t something you can turn away from: In the latest incident, a faulty CrowdStrike update knocked out Windows systems worldwide, disrupting airlines, banks, hospitals and quite possibly your business.
Watch the Webinar on Demand on the SAFE Academy Site
“TPRM for Cyber Risk Management Professionals”
Vince Dasta, Senior Partner, Risk Strategy, SAFE
Mark McKinney, Risk Advisor, SAFE
Subscribe to SAFE Academy to watch
Already a Subscriber? Find it under Featured Courses
Here are some of the key insights of the webinar:
TPRM grew out of vendor onboarding, not risk management – and that’s created problems
The cycle of onboarding and offboarding a vendor with annual risk assessments differs from the always on-guard mentality of risk management – and vendor management is often siloed in the hands of privacy, legal or procurement teams, not risk managers. One result is over-complicated flow charts for third party oversight that suck up time and attention. Teams tend to fall back on compliance with standards like ISO 27001, good practices but don’t give a read on risk from a business point of view.
Common TPRM tools in use don’t give a complete picture of supply chain risks
The main approaches to TPRM are good partial steps but each have some serious limitations and risk managers struggle to reconcile their outputs, often on a spreadsheet.
- Questionnaire-based assessments are time-consuming to collect and assess, cover only one point in time, and take a superficial inventory of controls, in other words, without an up-to-date status report on their coverage, capability and reliability.
- Cybersecurity risk ratings are based on outside-in scans of public-facing controls, an incomplete picture of the entire controls environment. These numeric ratings should not be confused with cyber risk quantification (CRQ) which provides insight into a company’s risk exposure: the financial impact of cyber risks and the likelihood of cyber attacks.
TPRM must evolve to the level of other forms of risk management in the enterprise.
The state of play in third-party or supply chain risk management “is where we were in cyber risk management years ago,” said SAFE’s Vince Dasta, before the advent of CRQ-based risk management techniques such as FAIR (Factor Analysis of Information Risk), the model that underlies SAFE’s solution. “Let’s do the same transition in third party cyber risk management…We want to look at this risk like we do other risks in the organization to understand it in terms of business processes.”
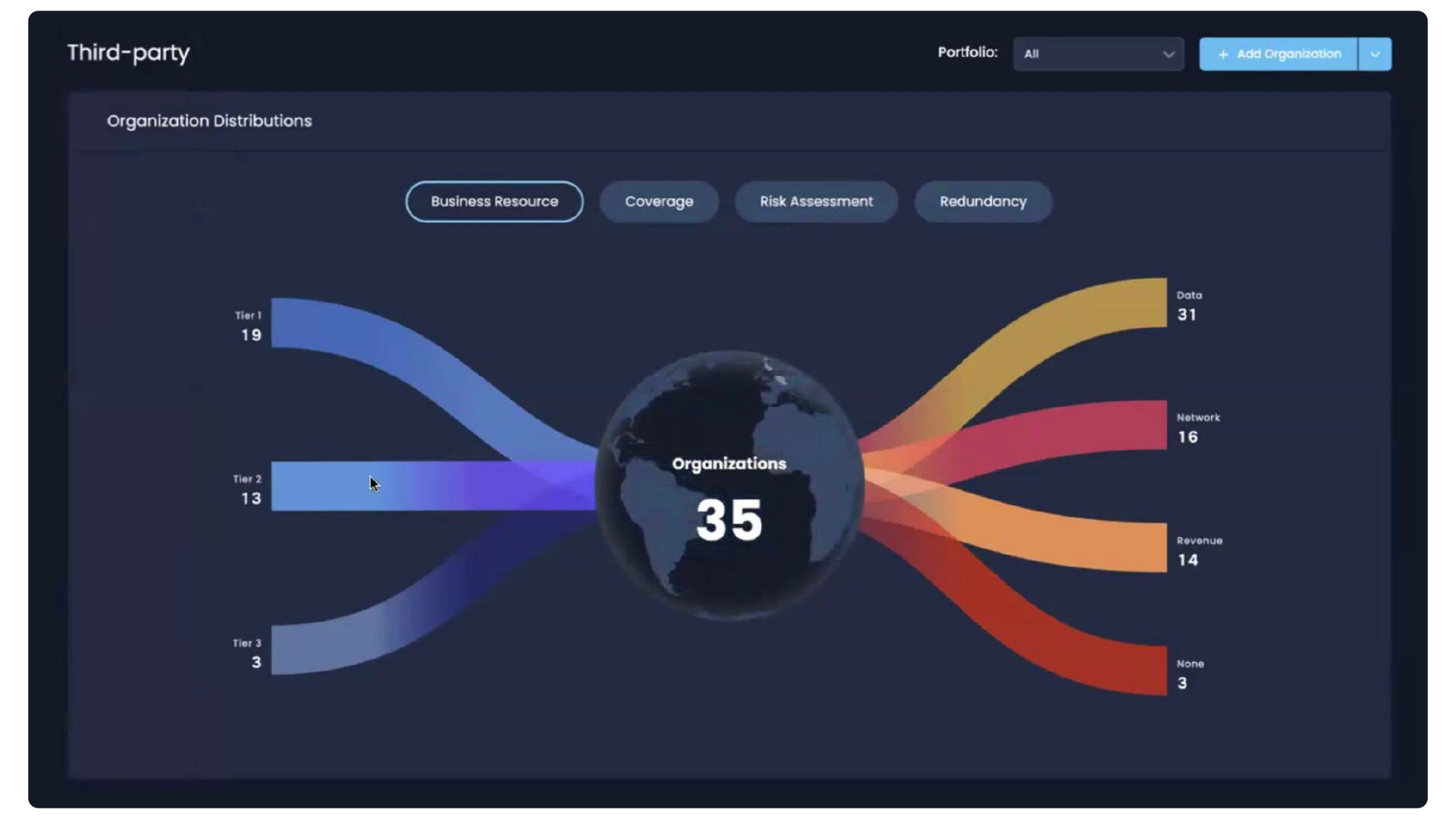
The typical large company engages in thousands (and even 10’s of thousands) of third-party supply-chain relationships. The only practical way to manage the risk is to first identify the inherent risk each poses then to prioritize them into tiers. Some prioritization factors:
- Business resources at risk via the third party
- The threat landscape the third-party faces
This analysis enables us to pull together the elements of FAIR risk analysis: the magnitude of probable loss and the frequency of probable attacks.
Next step: Sort the third parties into tiers by employing the standard TPRM tools (questionnaires, risk ratings) at levels of increasing rigor.
For the critical vendors, apply the highest level of scrutiny, continuous inside-out risk assessment of their controls and your vendor-facing first-party controls. “The good news is that more and more organizations that have critical relationships are being able to do this both contractually as well as kind of culturally,” Vince said.
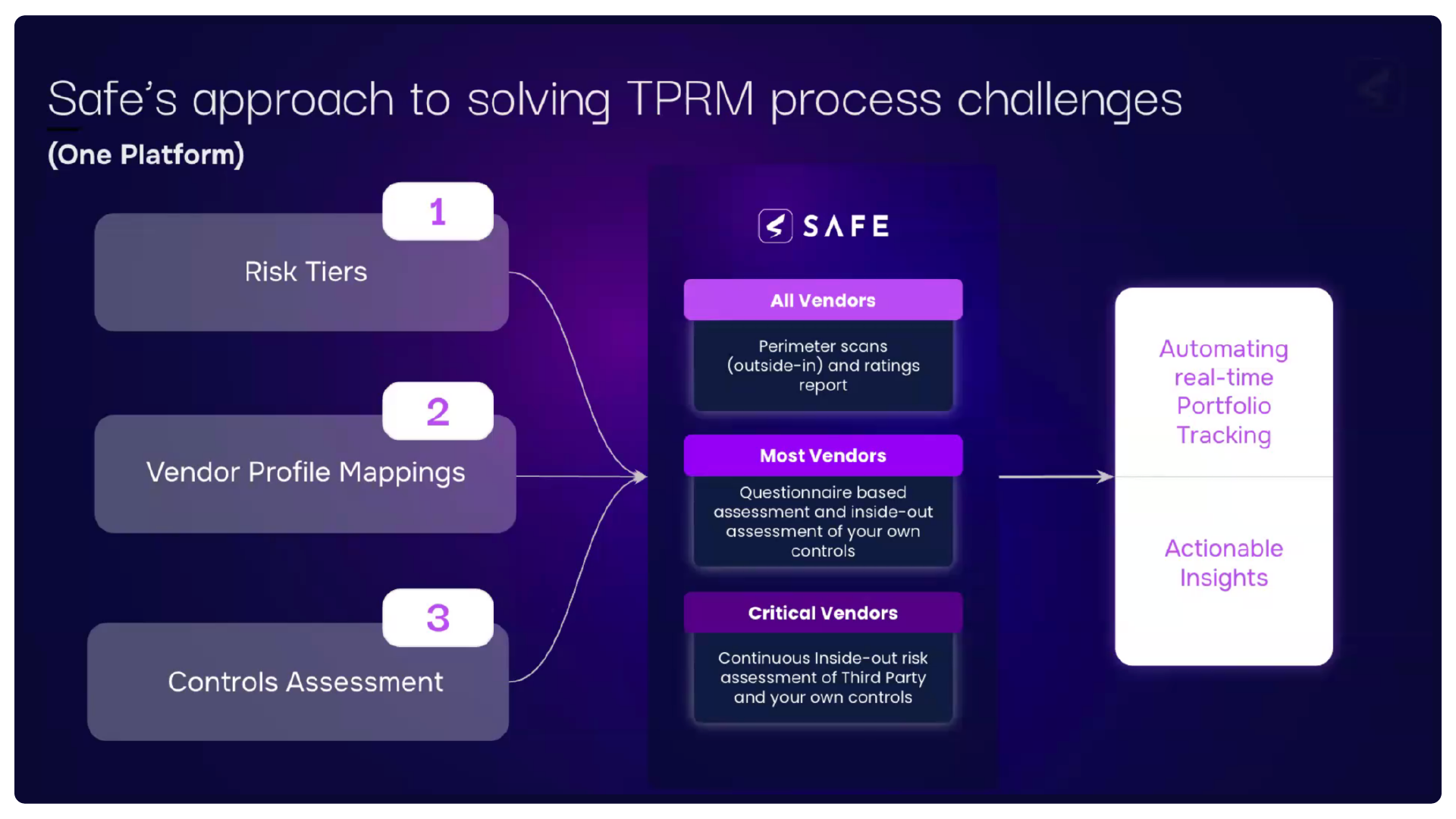
Finally, you want an action plan for TPRM
The SAFE One TPRM platform brings TPRM down to an actionable level. SAFE, working with the FAIR Institute, has identified the top controls for both first-party (zero trust) and third party cyber risk management that you can monitor for performance with direct evidence, gathered into the platform with APIs. Altogether, you have a single view of your risk posture. With that level of specific information, you can also work with your critical third parties to optimally maintain their controls – and continuously prioritize and manage third parties based on risk to your business.
Watch this webinar to see the SAFE One TPRM solution in action.
TPRM for Cyber Risk Management Professionals
Subscribe to SAFE Academy to watch
Already a Subscriber? Find it under Featured Courses.



