How to plan a proactive defense strategy for cybersecurity
Brute force attack, zero-day attack, compromised credentials, distributed denial of service (DDOS) – technical terms for the “attack vectors” (or “threat vectors”) that cyber criminals, spies and other threat actors ride to gain unauthorized access to computer systems – terms that increasingly pop up in daily life, due to the record number of data breaches.
What is an attack vector and how can you secure yours? Let’s dig into this must-know segment of cyber risk analysis.

What Is an Attack Vector?
An attack vector is defined as the method or combination of methods that cybercriminals use to breach or infiltrate a victim’s network or system. They can use various pathways through which attackers can exploit vulnerabilities, gain unauthorized access, and carry out malicious activities such as data theft, system compromise, or service disruption.
Let’s get grounded by turning to the MITRE ATT&CK framework, the bible of cyber defenders looking to understand their adversaries. MITRE ATT&CK is a vast knowledge base documenting attacker “TTPs”:
- Tactics. The “Why” The adversary’s tactical goal (let’s says data exfiltration)
- Techniques. The “How” (compromised username and passwords for initial access, etc.)
- Procedures. The specific technical steps the adversary goes through
The framework gives details on all the reported TTPs – you can see them in this representation of the ATT&CK Matrix for Enterprise. Look at the third column, “Initial Access.” In the narrowest definition, those are the attack vectors in cybersecurity to break into your operating system (see “phishing” in this column for a well-known example).
But in the broader, more useful sense, the entire framework describes the many facets of an attack vector as it plays out in your system.
Now for some good news. The MITRE ATT&CK framework also extensively catalogs mitigations for each of the attack vectors.Under “Phishing” you can find cybersecurity controls such as Antivirus, Software Configuration (for anti-spoofing and email authentication) or User Training (to recognize a social engineering attack) – all helpful for cybersecurity teams to plan their defenses. —
What Attack Vector Requires No User Interaction?
“Zero click,” is particularly insidious technique to gain initial access launches on mobile phone systems with no human interaction or awareness. It leverages vulnerabilities in applications, services, the operating system or even at the kernel level that protects the hardware.
—
Key Terms: Distinguishing Attack Vectors from Related Concepts
Let’s take a moment to define some key terms, related to attack vectors:
1. Threat Actor: A person or group capable of causing a loss to our organization.
2. Attack Vector: A means for a Threat Actor to gain initial access to cause a loss to our organization. (Alternative term: Threat Vector)
3. Attack Surface: Assets or persons in our organization that could be points of initial access for a Threat Actor.
Attack Surface
An attack surface refers to the sum of all potential security risks and vulnerabilities present within an organization’s environment. It encompasses all known and unknown vulnerabilities, as well as the security controls related to all hardware, software, network components, and personnel.
It used to be a more manageable concept in the days when IT was all on-premises, defended by a perimeter firewall. Today, enterprises are overwhelmingly opting to buy rather than build digital capabilities to streamline operations, drive growth, and scale swiftly while maintaining competitive pricing.
This leads to a growing reliance on third-party technology, data, and services for strategic business initiatives, spreading the attack surface among an army of vendors, including cloud and applications hosts.
One of several recent catastrophic failures due to third-party dependency was the outage of CrowdStrike, a leader in antivirus endpoint security that pushed out buggy code to its clients. It turned out that CrowdStrike was operating at the “kernel” level of Microsoft Windows, taking down Windows systems around the world; just one effect was a global “ground stop” on flights of major airlines.
In other words, the attack surface for CrowdStrike customers was at the deepest level of their operating systems.
Threat Vector
A threat vector, often used interchangeably with an attack vector, refers to the specific methods or pathways that cybercriminals utilize to gain unauthorized access to a computer system, network, or application.
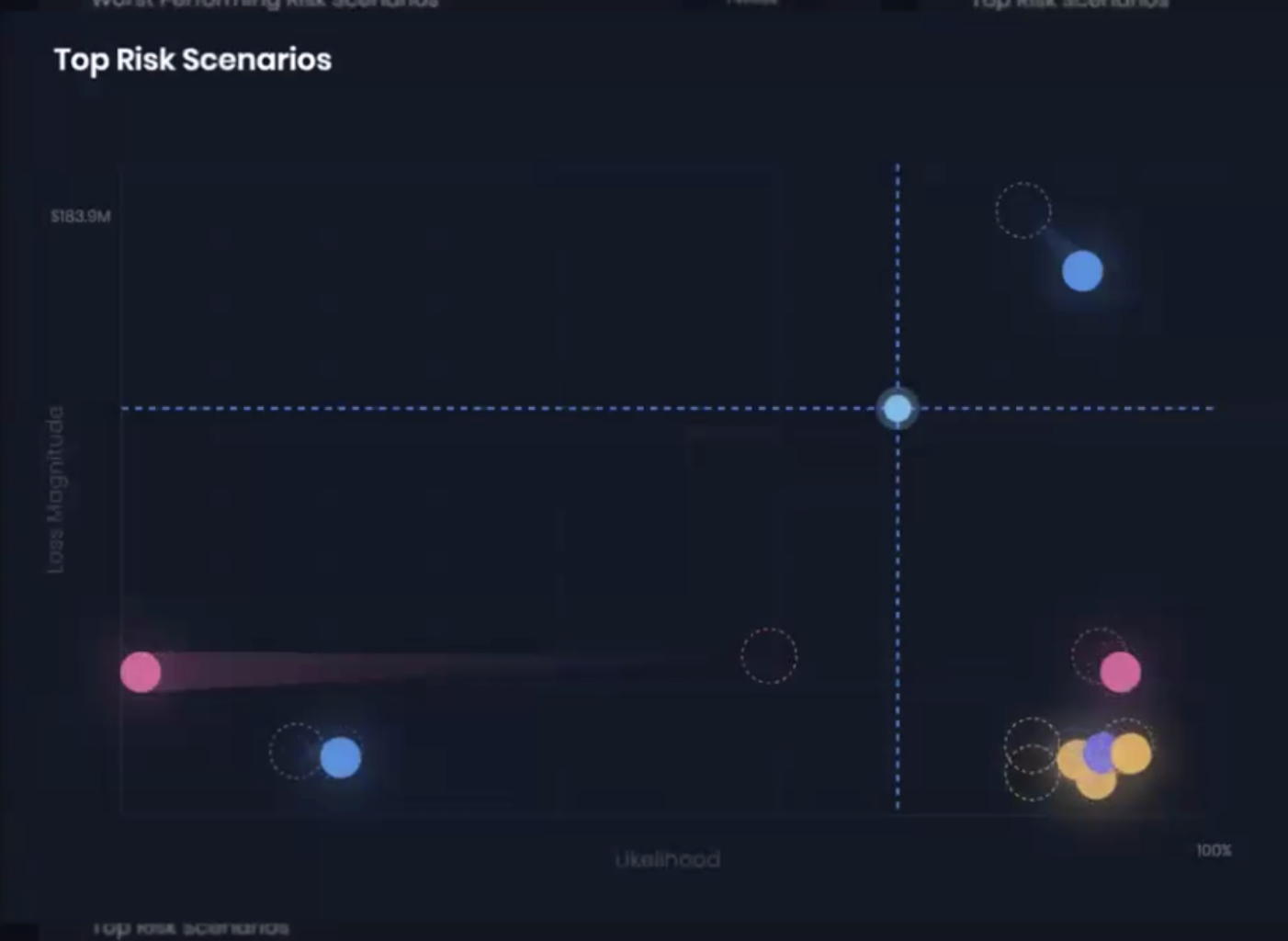
Risk scenario analysis on the SAFE One Platform
Threat Actor
In cyber risk management, the best way to think about risk is through risk scenarios, as defined by the FAIR Model for cyber risk quantification.
Scenario example:
“Analyze the risk associated with malicious external actors breaching the confidentiality of sensitive company data accessible on a lost/stolen mobile device.”
Formula:
Specific threat actor(s) impacting specific asset(s) by some specific means resulting in a loss.
Any of those four elements missing, we don’t have a risk.
However, there may be many types of threat actors or groups of threat actors:
- Nation states committing espionage
- Cyber criminals deploying ransomware – including, in a modern twist criminals renting ransomware-as-a-service such as Black Basta
- Privileged insiders who have gained access to critical systems and non-privileged insiders (everybody else) who may be acting maliciously to damage the organization or non-maliciously (emailing the wrong attachment containing sensitive information).
- And in the emerging threat-actors category: AI systems accidentally leaking data or creating other novel problems.
As we saw with MITRE ATT&CK, defining our threat actor of concern is critical to understanding the tactics, techniques, and procedures (TTPs) that could be used against us – and by extension understanding the capabilities of an attacker. Quantifying threat-actor capability, along with the strength of our protective controls enables us to get a accurate read on our susceptibility to attack, important to understanding our overall loss exposure.
Third-Party Risk Management and the Attack Surface
Conventional third party cyber risk management (TPRM) struggles to keep up with this stretched attack surface. Traditionally, TPRM has been limited to
1. A check for compliance with accepted operational standards (SOC2, ISO or PCI-DSS), often done yearly – a major burden for both first- and third-parties to collect and process reporting from dozens of vendors
2. An outside-in scan of web-facing security applications, giving a partial, point-in-time, unreliable view of an organization’s cybersecurity controls.
In the cyber field, that practice is rapidly being outpaced by a new standard
1. Continuous inside-out monitoring of controls status at the third party to keep up with the rapidly changing digital risk landscape.
2. “Zero-trust” controls on the first party’s network to limit damage from a system intrusion that originated with a third party.
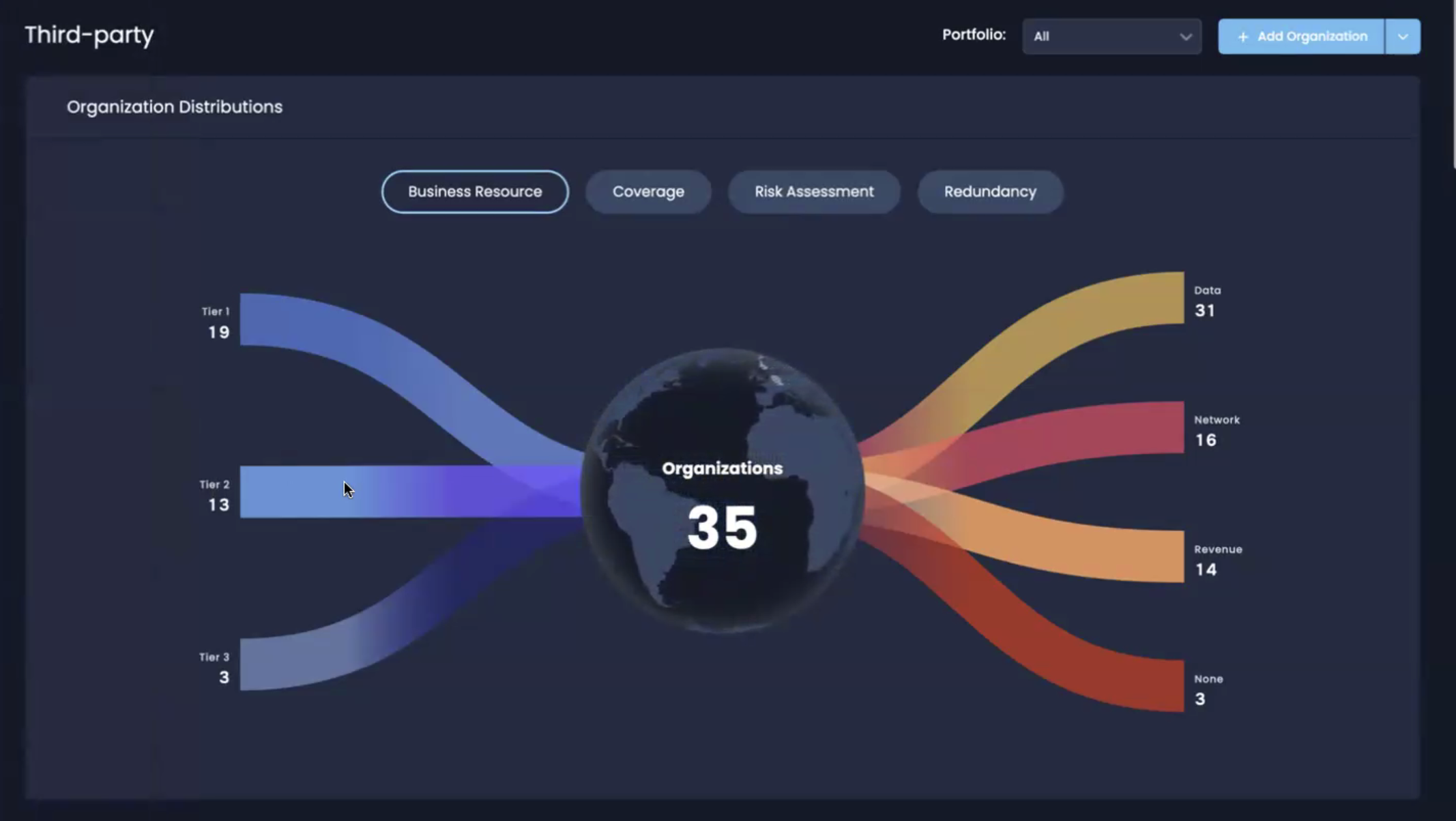
Third-party risk management on the SAFE One platform
What are Common Types of Attack Vectors You Should Know?
Attacks come in a huge variety of forms, and threat actors are always innovating on them. Here are the 15 cyber attack vectors most often seen in the wild.
1. Social Engineering
Manipulation of individuals into divulging confidential information or performing actions that compromise security. This is typically done through deception or exploiting human psychology. Examples would be phishing, business email compromise, or “deep fake” impersonation of a business leader in a voice mail.
2. Compromised and Weak Credentials
Through phishing, buying identities on the dark web, brute force or other means, an attacker acquires valid credentials to an existing account, and bypasses controls to operate within a target system.
3. Weak or Missing Encryption
An attacker gains access to transmitted network traffic by bypassing encryption to tap into confidential communications.
4. Third and Fourth-Party Vendors
Increasingly an attack vector as organizations outsource data storage and applications. For instance, organizations may create a single point of failure by over-reliance on a payments processor (as in the Change Healthcare hack). In a supply chain attack, malware can be distributed by surreptitiously slipping it into a legitimate software update (see the SolarWinds attack). Or a trusted vendor with deep access to systems can inadvertently distribute a corrupted software update (as in the CrowdStrike incident).
5. Insider Threats
An insider threat refers to a cybersecurity risk from within an organization. Thai typically involves a current or former employee, or another individual with direct access to the company’s network, sensitive data, and intellectual property (IP). These insiders possess knowledge of business processes, company policies, and other critical information that could facilitate an attack.
Attackers may be malicious (seeking to harm the organization for vengeance or profit) non-malicious (innocently making mistakes that cause a loss) – privileged (with access to sensitive applications or data) or non-privileged. It’s important to note that not all insider threat actors act with malicious intent. Some may unknowingly become unwitting accomplices, having their digital assets compromised and exploited by external threat actors.
6. Security Misconfigurations
Security features not turned on, unnecessary services left open, default passwords not changed – are among the many ways that web-facing applications can be left vulnerable. A survey by Qualys found 31% of Amazon S3 buckets were open to the public in 2023.
7. Malware and Ransomware
A fast-growing, high-profit industry: A survey by Splunk found that 83% of organization’s paid the ransom. Ransomware is a multi-step event, starting with a malware payload delivery via email or other means to an unsuspecting human, with a stealthy execution on the target system. The victim organization’s data may be encrypted at the source or exfiltrated with a demand to pay to prevent public release. A troubling recent trend is ransomware-as-a-service, pre-packaged attacks sold to would-be extortionists, no special expertise required.
8. Brute Force Attacks
Attackers acquire passwords for initial access or to maneuver within systems. Methods might be to systematically guess weak passwords or use services that leverage previously acquired password data such as hashes.
9. Phishing
Social engineering, typically delivered by email or social media to fool the victims into clicking a link to execute malicious code on their systems. In spearfishing, a particular person or industry is targeted.
10. SQL Injections
Exploiting database vulnerabilities by injecting malicious code into a system, often through an unprotected data-entry form on a website, leading to a data breach.
11. Zero-Day Vulnerability
In this type of attack vector, a software defect unknown to the developer or the public, is discovered by attackers before patching, and delivered to users (often through phishing) to gain system access and execute malicious code.
12. Trojans
Malware disguised as legitimate software, encouraging a victim to click and download a malicious package.
13. Cross-Site Scripting (XSS)
Attackers typically inject malware into a form field on a web page often to steal log-in credentials or inject scripts that users can unknowingly execute in their browsers.
14. DDoS Attack
The Dedicated Denial of Service tactic overwhelms an endpoint or network with malicious traffic to degrade or shut down services.
15. Man-in-the-Middle Attacks
Also known as Adversary-in-the-Middle, an attacker inserts itself between networked devices perhaps with the intention of forcing devices to communicate through the attacker’s system to collect information.
Why Do Cybercriminals Target Attack Vectors?
As we’ve seen in our discussion of the MITRE ATT&CK framework, the cybersecurity and cyber risk management professions are heavily focussing on threat intelligence on cybercriminals and other threat actors. CISA (the US Cybersecurity and Infrastructure Agency), the FBI and private threat intel companies also have eyes on this threat community. All work to expose the tactics, techniques, protocols, capabilities and goals of the threat actors so cyber defenders can focus on the processes and controls that have maximum effect on thwarting and mitigating attacks.
For cyber criminals, the motivation is always money, but the specific attack vectors and crimes vary widely:
Ransomware: Attackers seize control of critical data and systems, and hold them hostage for ransom or exfiltrate it and threaten to make it public (“double extortion”)
Ransomware-as-a-Service: Criminals rent the tools to commit ransomware crimes to others.
DDoS for Ransom: Threat actors bombard a business from a bot net until the victims pay up.
Data Theft: Stealing personal information for purposes of identity theft or to commit insurance fraud. Capturing credit card information for fraudulent payments.
Business Email Compromise / Funds Transfer Fraud: Through spoofed email (phishing) or voicemail (vishing) or SMS text messages (smishing), a criminal may induce an employee to pay on a phony invoice or otherwise give up money.
Account Takeover: Through a brute force attack or credentials stealing, gain access to a bank or credit card account to make unauthorized payments.
Espionage or Sabotage for Hire. Unscrupulous corporations or nation-states may employ skilled cyber criminals as contractors.
Active vs Passive Vector Attack
Attack vectors generally fall into two categories: passive and active.
Passive Attack Vectors
Passive attack vectors involve monitoring a victim’s system for vulnerabilities. This can include open ports, misconfigurations, or unpatched software. The goal is to gain access to data and sensitive information without disrupting the system.
Examples include port scanning and social engineering. Passive attacks can be difficult to detect as they don’t alter the environment.
Active Attack Vectors
Active attack vectors are used to alter a system or disrupt its operation. While data theft is still a common goal, active attackers may also aim to cause chaos in the victim’s IT environment.
Examples include malware, ransomware, DDoS attacks, and credential theft. Active attacks directly impact the system, making them easier to identify.
8 Best Practices to Protect Attack Vectors
- Employee training and awareness programs
Valuable education in how to recognize phishing emails and other defensive measures. But companies must be careful to align productivity goals with security concerns so mixed signals are sent to employees.
- Encryption
Scrambling data at rest or in transit so that only authorized users who have a key can convert it back to plaintext information. End-to-End encryption is the gold standard, using two different keys and creating an asymmetrical system.
- Cloud Protection
Handing off your data to a major cloud vendor like Amazon should buy you first-class security out of the box, and indeed Amazon offers encryption services – if you configure your bucket correctly – and many users don’t.
- Implementation of multi-layered security measures
Increasingly organizations are following “zero trust” principles mandating verification for every access request…and/or “least trust” principles restricting users to only those activities that fit their job duties…typically under the control of an Identity and Access Management (IAM) system.
- Continuous monitoring and threat intelligence integration
Advanced security applications now make possible a unified, real time view of the attack surface, the threat landscape and controls status. With threat intel, risk managers can quickly create what-if scenarios after detecting an attack, anticipate the tactics of the attackers and make risk-informed decisions on deploying controls.
- Regular security audits and vulnerability assessments
Advanced applications also can ingest an organization’s NIST CSF or other security documentation, inventory controls to identify gaps and give continuously updating reports on controls status.
- Patching vulnerabilities
Effective patch management relies on effective risk analysis. A cyber risk quantification model like FAIR saves the security team from scrambling to remediate every audit finding of unpatched vulnerabilities, and keep focus on the risks that threaten more serious loss exposure.
- Regularly update third-party software
Third-party risk management (TPRM) has emerged as a leading cybersecurity concern after high-profile third-party software fails (see SolarWinds and CrowdStrike).
Conclusion: The Importance of Proactive Defense Against Attack Vectors
It’s game on with the biggest, most dedicated team of adversaries you will ever face: cyber attackers. They will never stop innovating to find new attack vectors into your systems and your data. A passive, reactive stance – relying, for instance, on “maturity models” that rate the number of controls you have implemented – won’t meet the challenge. You need a proactive defense that combines:
- Continuous attack surface monitoring for threats
- Continuous monitoring of controls status and their effectiveness at risk reduction
- A quantitative, risk-based approach to prioritizing security investments that empowers you to react strategically to threat vectors
- Continuous updating of threat intelligence to identify the latest TTPs for attack vectors – and analysis of the strength of the organization’s relevant controls
SAFE can help you stay proactive.
SAFE One is the only data-driven, unified platform for managing all your first-party and third-party cyber risks in real-time.



