CRQ 101: What Is Cyber Risk Quantification?
“You cannot manage or mitigate what you do not measure.”
Today’s cybersecurity landscape requires agile and data-driven cyber risk management.
Unfortunately, the current cyber risk management practices are broken – they are siloed, reactive, and lack a business perspective. Using the capabilities your organization already has, Cyber Risk Quantification and Management (CRQM) offers a brand new approach to measure, and manage enterprise-wide cyber risk in real-time to drive decisions. CRQM helps CISOs have the right conversations with the board members, the CEO, and the CFO.
“CISOs need decisions, not more dashboards,” Forrester, January 2022.
Cyber Risk Quantification is a must-have for CISOs
Businesses are already doing more than enough and spending billions to identify risk from external (threat intel), and internal signals (from your cybersecurity tools, technology assets, people, and processes) – SOC teams, internal security executives, and analysts are overwhelmed by the number of data signals they have to deal with, daily.
You do not require another product or service to produce another list of actionable recommendations that complicate your job.
Instead, you need a systematic method to consume the data your team already has, parse it through a platform that leverages data science to deliver a simple, easy-to-digest, actionable, and speaks the language your C-suite and the Board understand. This is where Cyber Risk Quantification and Management solutions are a game-changer.
Can you quantify cyber risk? Isn’t it too complex?
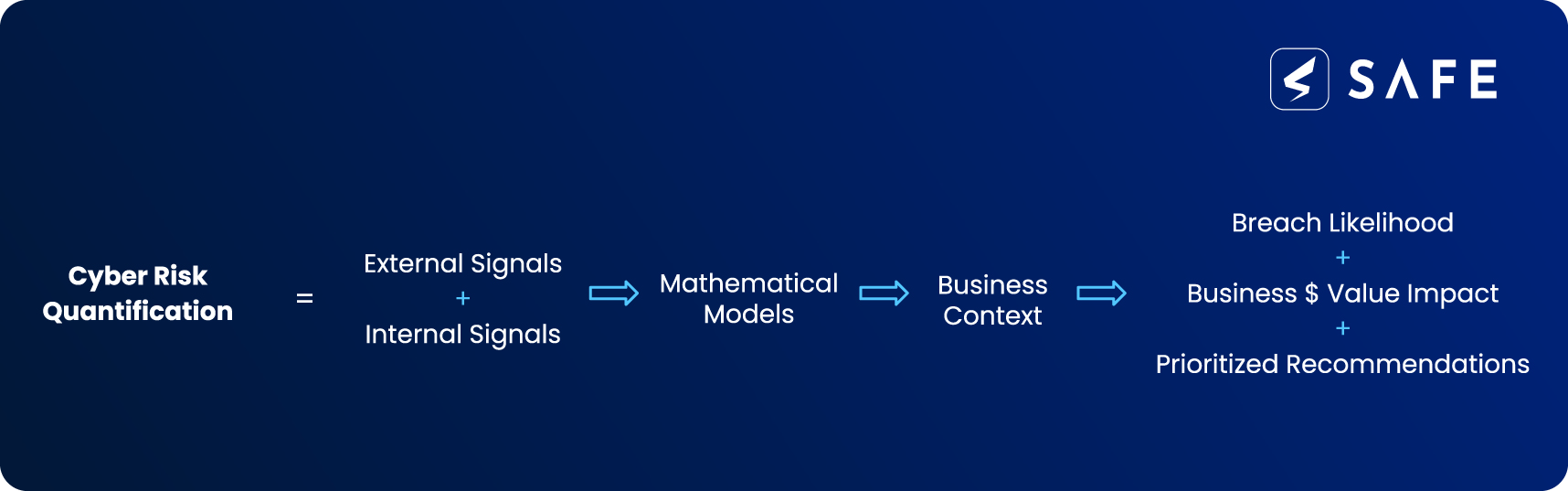
Despite limited empirical data, cyber risk can be reasonably quantified to help security and risk leaders proactively reduce the uncertainty (likelihood) of cyber events. You have more data and need less data than you think. Your business is already collecting pools of data from various sources across your estate – people, processes, cybersecurity products, technology, and third parties. What you require is a method to ingest, parse, and analyze the data in a simple, real-time, and contextual manner.
Cyber Risk Quantification platforms such as SAFE use Bayesian Network-Based models. It incorporates signals through API integrations and generates an output representing a granular view of how likely your organization is to get breached across all vectors. It also calculates the potential financial impact your enterprise faces. At the same time, SAFE’s recommendation engine prioritizes risk management through data-driven insights – enabling you to decide whether your business should accept, mitigate, or transfer the risks.
Watch our interview with Douglas Hubbard, inventor of the Applied Information Economics method, author of “How To Measure Anything in Cybersecurity”, and SAFE Board Advisor.
As a CISO, what do you get from cyber risk quantification?
Since your business’ internal signals are mapped against external threat intelligence and compliances, cyber risk quantification helps you understand which type of breach is most likely – enabling data-driven decision making.
- Understand your cyber health by looking at the likelihood of your business being breached
- Compare your cybersecurity risk posture against your industry peers
- Convert cyber risk jargon into a language the Board and your CEO/CFO understand and appreciate – what is the cost to the business if cyber risk is mitigated, transferred, or left as-is.
- Get the ROI to justify your investments: If you invest $1 to improve your cyber posture, does your financial risk reduce accordingly?
- Get prioritized and actionable insights at an asset level for your security teams and a macro level for the enterprise.
If you’ve considered a way to quantify your enterprise’s cyber risk, or if you have tried and failed DIY solutions, we can help. SAFE is a leader in Cyber Risk Quantification and Management (CRQM) for enterprise-wide challenges in on-prem, hybrid, and multi-cloud organizations. We dynamically measure (and guide you to prioritize and manage) risk across people, processes, technologies, and third parties using API keys you already possess – and we show value in as few as 7 days. To understand how we do it, explore our whitepaper on “How Do You Measure and Mitigate Cyber Risk?”




