What is Technology Risk?
Technology risk, IT risk, cyber risk – what’s the difference among these commonly used terms, and is there really a distinction in a time of “digital transformation”? Generally, risk management has looked at the world of risk with this hierarchy:
- Operational Risk: Any event that affects the organization’s ability to operate
- Technology (or IT Risk), a subset of Operational Risk: Any risk to information technology or data or applications that negatively impact business operations. This could cover a range of scenarios, including software failures or a power outage.
- Cyber Risk, a subset of Technology Risk: Loss event scenarios strictly within the cyber realm, such as phishing, malware, data breach.
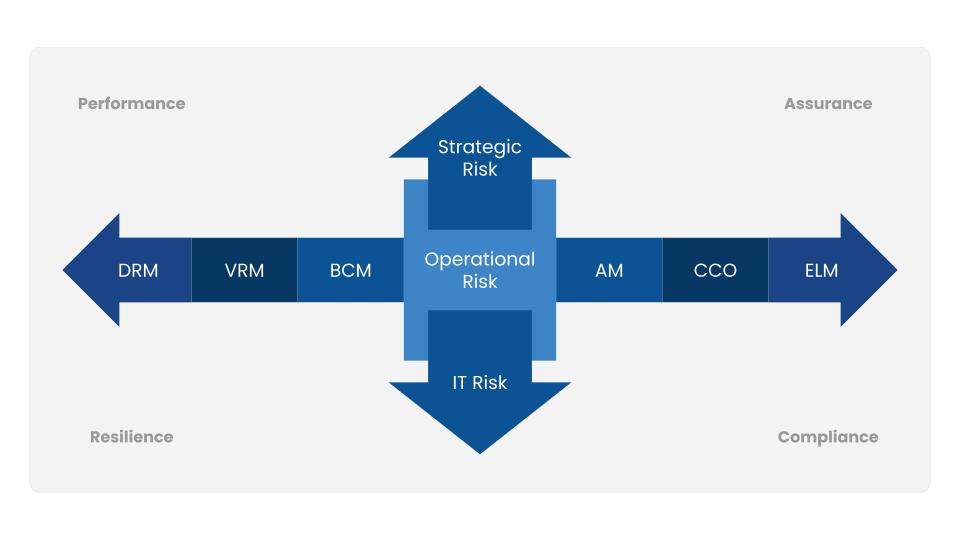
If it sounds like there’s a lot of room for crossover in these definitions, that’s right. Leading technology consultant Gartner has successfully advocated for Integrated Risk Management (IRM) that takes “a comprehensive view across all business units and risk and compliance functions, as well as key business partners, suppliers and outsourced entities.” In Gartner’s view, risk management is a continuum, as shown in this graphic, driving toward Digital Risk Management (DRM, on the left), as business processes all become digital in one way or another.
Defining Technology Risk in FAIR Terms
Factor Analysis of Information Risk (FAIR™) is the standard for quantification of cyber and technology risk in financial terms to enable justification, prioritization, and communication of security investments within an organization.
In FAIR terms, risk is defined as the
“Probable Frequency and Probable Magnitude of Future Loss”
The starting point for FAIR quantitative analysis is a risk scenario or risk statement that addresses a technology problem the business needs to solve. The format is:
“[Threat Actor] impacts [Confidentiality, Integrity, Availability] of [an Asset] via [Some Method]”
For example, for a cyber supply chain attack:
“Analyze the risk associated with an external threat actor establishing a foothold on the network through a trusted security vendor’s application resulting in a breach of sensitive data in our crown jewel asset.”
The FAIR standard shows the way to break the scenario down into factors to quantify the probable frequency and impact of such an event, based on the organization’s experience or industry data.
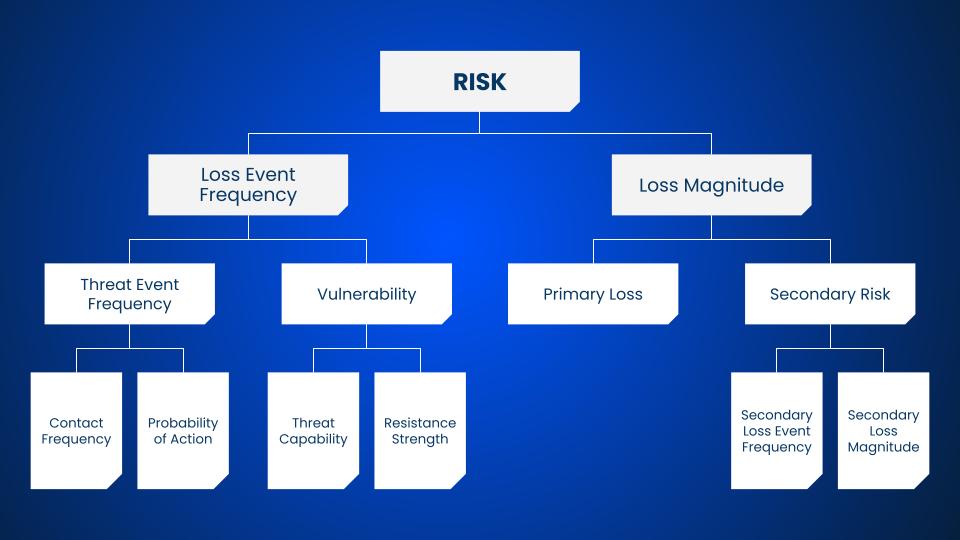
The FAIR model is highly flexible, and still valid with less cyber-centric scenarios.
The FAIR standard is maintained and advanced by the FAIR Institute, an association of more than 15,000 security and risk professionals. Learn more about the FAIR Institute.
SAFE and FAIR
As the technical adviser to the FAIR Institute, SAFE is the leader in implementing FAIR quantitative cyber risk management programs at scale. SAFE offers the world’s most advanced AI-powered automated Cyber Risk Management platform that, combined with the trusted analysis of the FAIR model, firmly positions security and risk management leaders as business enablers.
Case Study for Quantitative Cyber Risk Analysis
A furniture manufacturer wanted to determine if it should keep paying the annual subscription fee for support from the technology vendor for its order fulfillment system or bring the maintenance of the system in-house. If an employee misconfigured the system, what would that accident cost the organization in terms of lost sales, response costs, or other impacts? How would that compare with the ongoing subscription cost?
Scenario: “Analyze the risk associated with a non-malicious privileged insider impacting the availability of the order fulfillment system via a misconfiguration resulting in a suspension of fulfillment.”
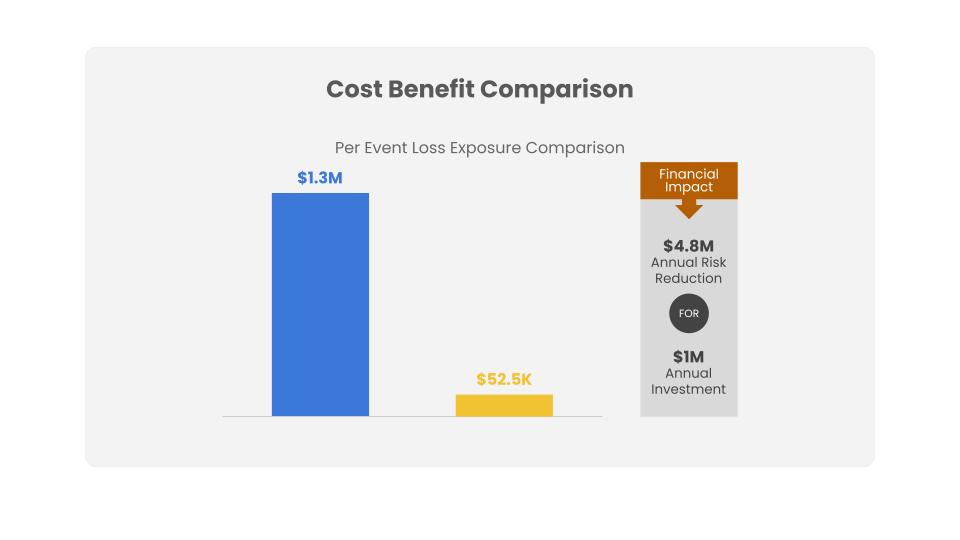
Quantified risk analysis based on FAIR showed that staying with the subscription service would shorten response time to an outage, reducing the impact to a level that justified the $1 million annual investment.
What Is an IT Risk Assessment?
Risk analysis and risk assessment are two more terms often used interchangeably but with an important distinction. While a risk analysis might look at a single scenario, a risk assessment gives a broader look at risk across scenarios to support business decision-making, particularly to justify, prioritize and communicate security investments.
Types of technology or IT risk assessments include:
- Rapid Risk Assessment: Run a quick series of risk analyses to aggregate and compare outcomes, for instance to prioritize top risks for response based on loss exposure in dollar terms.
- Aggregate Risk Assessment: Understand and quantify the organization’s total probable loss exposure for information technology. Gain granular insights by looking across scenarios to spot which threat communities or asset types pose the greatest risk to the organization, or which business units carry the most lost exposure, relevant insight for a CISO (chief information security officer) deciding on how and where to target defenses.
To fully support business decisions, risk assessments should be presented with risk treatment options for the risks identified.
A risk treatment analysis
- Establishes a baseline of loss exposure from the current situation
- Runs “what-if” scenarios to compare the risk reduction (in financial terms) from the current state that alternate proposed controls process changes could achieve.
- May include a cost/benefit or return-on-investment (ROI) analysis comparing the cost of new security investments to their effect on risk reduction.
What Is IT or Information Technology Risk Management?
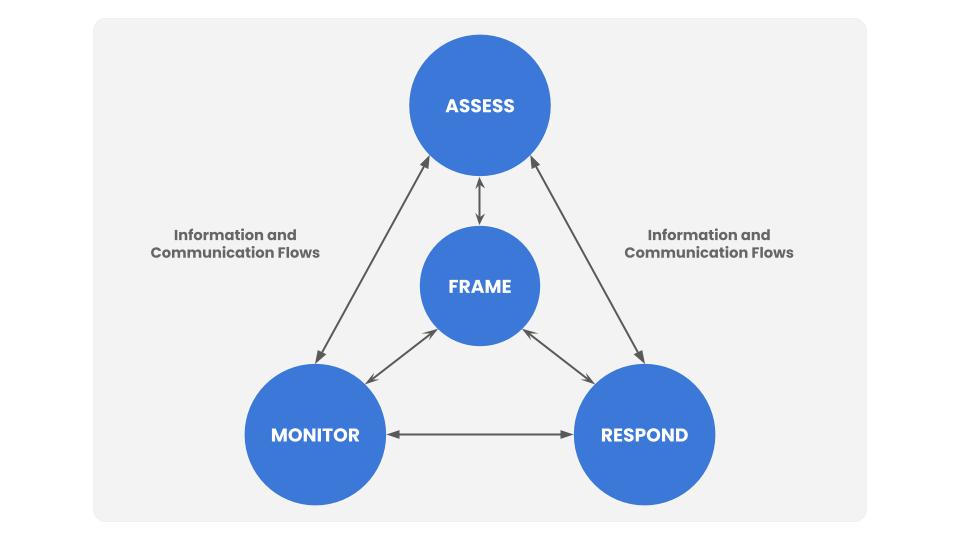
Risk management is a comprehensive process that requires organizations to: (i) frame risk (i.e., establish the context for risk-based decisions); (ii) assess risk; (iii) respond to risk once determined; and (iv) monitor risk on an ongoing basis using effective organizational communications and a feedback loop for continuous improvement in the risk-related activities of organizations.
National Institute of Standards and Technology (NIST) Special Publication 800-39: Managing Information Security Risk
As NIST advises, the first step in risk management is to “frame” risk, in other words establish a common terminology and measurement system – ideally one based on a standard such as FAIR that normalizes risk vocabulary — and based on quantitative analysis that measures risk in the financial terms used to communicate across the enterprise, also the output of FAIR analysis. With risk treatment analysis, organizations can also “respond” and, with ongoing risk assessments, “monitor” through a risk dashboard.
Compliance with IT Risk Management Frameworks
Many organizations make information risk management a less than “comprehensive” process by focusing on compliance with frameworks – treating publications like NIST 800-39 as checklist that recommend various security practices or controls, on the assumption that the more controls implemented, the lower the risk. Without quantitative risk measurement, however, that’s an unprovable assumption.
The frameworks are good foundational guides for a security program. But their strictly technical approach to cybersecurity can’t be fully aligned with business needs, such as determining security investments or communicating the need for budget to the business based on ROI.
Types of Risk Management Frameworks
- Control Frameworks
The SANS CIS Controls is a basic list of cybersecurity controls that should mitigate 80% of attacks. NIST 800-53 is an extensive list of controls that, practically speaking, no organization would ever implement in entirety. - Program Frameworks
ISO 27001 brings in business requirements to a controls list but doesn’t prescribe a specific approach to analyzing risk. The popular NIST Cybersecurity Framework (NIST CSF) maps specific controls to each cybersecurity function for a good technical overview of a risk management program.
Note: The NIST CSF includes FAIR as an “informative reference” among its recommended controls and processes.
Neither the controls frameworks nor the program frameworks can answer the basic questions for business decision-making, such as “if we invest in one security control or another, how much less risk will we have?” FAIR complements the frameworks by providing the missing quantitative risk analysis.
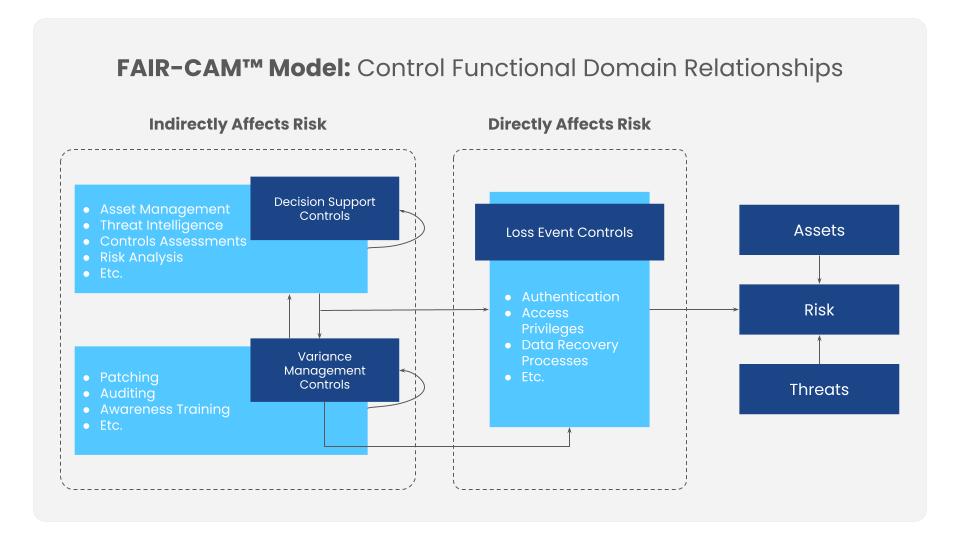
Getting Control of Your Cybersecurity Controls
The FAIR Institute has released an extension of the FAIR model, the FAIR Controls Analytics Model (FAIR-CAM™) that uncovers the relationships among controls, revealing costly duplication in functionality as well gaps in controls coverage. Learn more about measuring the value of controls with FAIR-CAM at the FAIR Institute website.
Technology Risk, Business Continuity Planning and Resilience
Large organizations often create a business impact analysis statement (BIA) to understand the links between processes that drive the business, and the probable outcomes of outages due to man-made or natural events that might significantly interrupt operations. For information technology, that means business continuity plans should prioritize IT resources to minimize the effect of an outage on the business. Typical off-the-shelf BIAs, however, share the fault of other non-quantitative risk assessments – they can’t communicate risk in business terms.
What Is a Material Cyber Risk?
Disclosure rules on cyber risk imposed by the Securities and Exchange Commission (SEC) in late 2023, focused the attention of both regulated and non-regulated companies on the need for a capability to quickly assess when a cyber risk crosses the line into causing a material financial impact to the organization’s bottom line. However, the SEC left it to companies to set their own definition of ‘materiality’. The FAIR Institute responded by releasing a new extension of FAIR, the FAIR Materiality Assessment Model (FAIR-MAM™) that enables organizations to accurately quantify the impact of cyber events in financial terms, on an ongoing basis.
- Learn more about FAIR-MAM.
- Implement FAIR-MAM with the SAFE Materiality Assessment Module
- Stay up to date on material-loss disclosures to the SEC with the Institute’s How Material Is That Hack online reporting service.
- Read a white paper: Your Guide to Material Cyber Risk Rules
Ransomware: Where Cyber Risk, Technology Risk, Operational Risk and Enterprise Risk Converge
The ransomware attack on Colonial Pipeline, the major fuel distributor that is provides critical infrastructure in the Eastern US, quickly jumped the increasingly irrelevant lines among risk disciplines.
Colonial Pipeline management chose to shut down fuel shipment after ransomware hit their business systems. In other words, a cyber risk quickly escalated through technology risk to operational risk and ultimately a risk to the enterprise, potentially in material impact on the bottom line and certainly reputation impact and perhaps legal and regulatory impact.
NIST has released Integrating Cybersecurity and Enterprise Risk Management (NISTIR 8286) to advise organizations on dealing with this new risk reality. The publication called out FAIR as a tool to “better prioritize risks or prepare more accurate risk exposure forecasts” in a risk register. NISTIR 8286 also endorsed many of the standard practices of FAIR analysis, including risk prioritization, risk scenario modeling, Monte Carlo simulations, and, of course, quantification of cyber risk in financial terms.
Is Artificial Intelligence a New Form of Technology Risk?
“Deep fakes,” “hallucinations,” corporate data leaked through a large language model (LLM)…Generative Artificial Intelligence (GenAI) opens novel threat vectors for insider error and external attack. But with the proven principles of FAIR, an organization can scope and quantify an AI risk scenario to generate analyses that enable sound business decision-making. The FAIR Institute has released a FAIR AIR (Artificial Intelligence Risk) approach to quantitative analysis of AI-related risk. One important caveat: Organizations must prioritize security from the outset in reacting to the challenges and opportunities of artificial intelligence. Learn more in this blog post: Maximizing Opportunities: How Risk Quantification Can Drive GenAI Adoption
The SAFE Solution for AI Risk
The SAFE platform offers a comprehensive GenAI Risk Posture Management Platform to equip data-driven decisions around AI risk management. SAFE’s CRQM solution automates GenAI risk identification, quantification, prioritization, and management with its AI-powered approach and prompt professional and risk advisory services. SAFE helps organizations mitigate GenAI risks by implementing the FAIR AIR approach.



