What Is Vendor Risk Management (VRM) 2024 Guide
A VRM strategy is essential for business continuity, information security and regulatory compliance.
In the interconnected world of business today, more organizations must turn to third-party vendors of goods and services to keep up with the pace of business. The benefits of this approach are many. Just-in-time delivery and niche specialization are more cost and time-efficient than old models of keeping integrated operations in-house.
But there’s also a downside: the organization’s “attack surface”, formerly kept behind cybersecurity firewalls, now spreads for large organizations over hundreds, even thousands of vendors performing critical functions or holding sensitive data as third parties. That’s not even factoring in the fourth parties and down in the networks of those vendors.
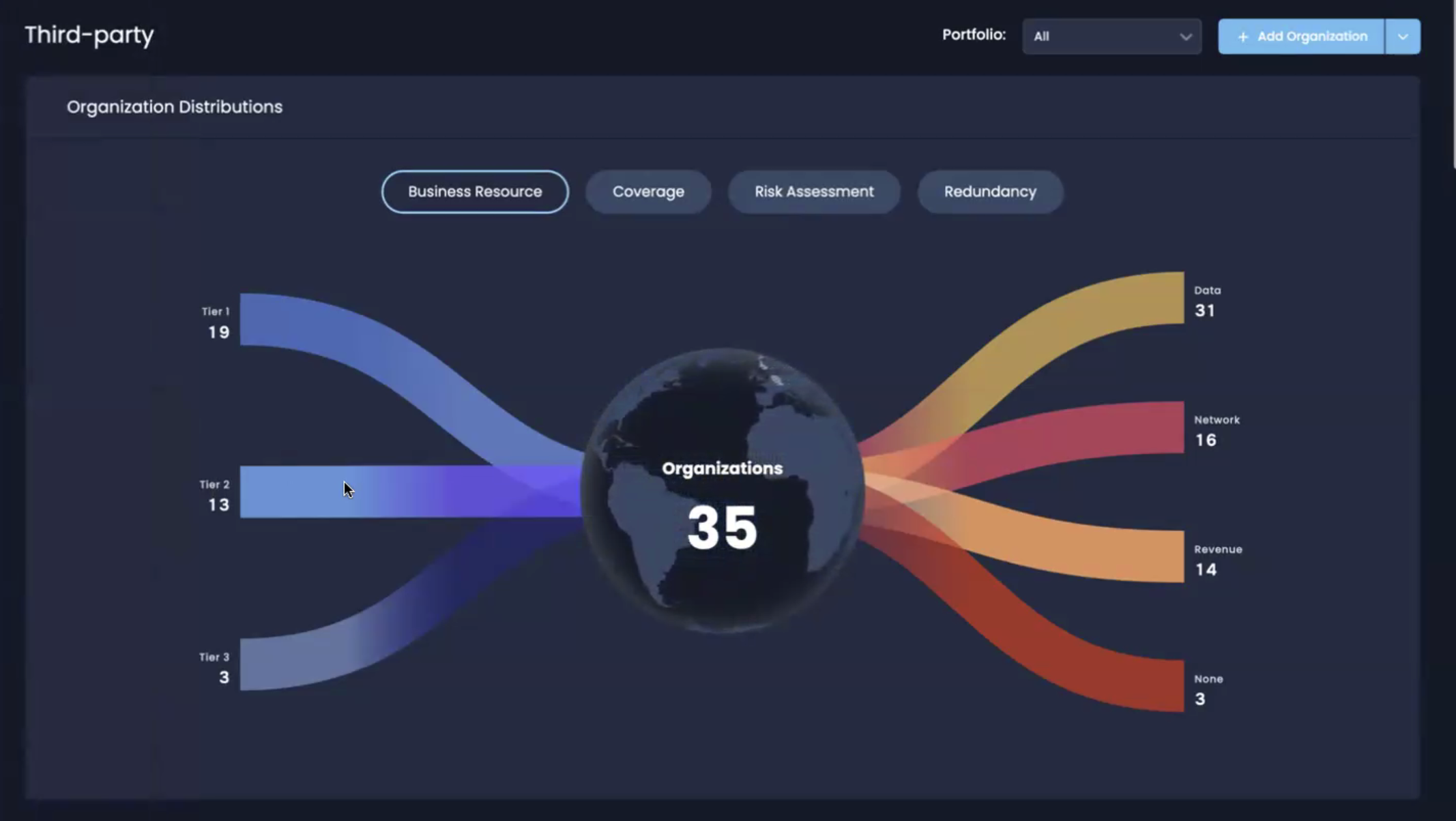
A tiered, risk-based view of vendors on SAFE’s TPRM platform
Of course, cyber attackers, ever looking for vulnerabilities, are now going after third parties as a way to break into systems when larger first parties may be tougher to penetrate. Meanwhile, the power of insiders at third parties who can disrupt operations at first parties through careless mistakes with code or data has increased.
Regulators are taking notice: the US Federal Reserve warned community banks in 2024 that “engaging a third party does not remove a bank’s responsibility” to comply with regulations “just as if the bank were to perform the service or activity itself.”
Organizations are actively searching for proactive vendor risk management (VRM) strategies and programs to shield their interconnected business operations from cyber threat. What they find often is existing methods that are outdated, inaccurate and fail to mitigate business risk. They persist because they have become standard practice and are required for audits and compliance reporting.
Let’s take a deep dive to make sense of managing vendor risk, the state of the art in VRM and where it is heading .
What is Vendor Risk Management?
Definition of VRM
Vendor risk management is a practice that seeks to assess and mitigate risk from two directions:
- Risk posed by a third party vendor to the first party – and the first party’s risk posture facing those risks
- The third party’s risk posture facing its own risks
The vendor risk management lifecycle starts with selecting and onboarding the vendor and should continue on a continuous basis through offboarding.
Implementing a robust VRM strategy is essential for business continuity, information security management, and regulatory compliance. Failure to manage vendor risks can lead to business operations going down, data breach, legal liabilities, financial losses, and more damage.
Definition: What Is Vendor Risk Management Maturity?
A vendor risk management maturity model would provide organizations with a framework to assess their VRM processes. The model could outline several stages of maturity:
- Basic: Organizations have at least created a directory of vendors, often a major task in itself for organizations with hundreds of vendors.
- Compliance focus: First parties can demand in contracts that third parties demonstrate ISO or SOC2 compliance – and typically answer a questionnaire – and might even be able to negotiate some rights of inspection of the vendor’s processes. Questionnaires at best provide a point-in-time look at risk posture and are time-consuming to prepare by the third party and tally by the first party.
- Verification by scanning: Various services offer outside-in scans of third parties to verify security controls in place with a view limited to the controls open to the internet.
- At the highest level, the model combines questionnaires and other compliance verification and, with the cooperation of the third party, inside-out reporting on the presence and status of controls, updated continuously.
Vendor Lifecycle Management
Vendor Lifecycle Management is a broader concept that encompasses the entire relationship with a vendor, from initial selection and onboarding to ongoing performance evaluations, contract management, and eventual off-boarding.
Effective vendor lifecycle management ensures that vendors are consistently meeting expectations and that risks are managed proactively at every stage of the relationship.
Tip: Mind Your Offboarding
When terminating a vendor, cancel access to any accounts or apps or physical entry to premises. Ensure the third party deletes intellectual property or sensitive information data from any servers or devices. Stay in touch: Missing data or other issues may well arise after completing offboarding.
Types of Vendor Risk
Vendor risks can be categorized into several types, each of which requires careful analysis. For the most effective analysis format, express risks in a risk scenario format with a threat actor, an attack vector, controls in place, an asset at risk and an impact to that asset – all elements that can be quantified to arrive at a range of estimates for likelihood of occurrence and impact in financial terms.
Third-Party Financial Risk
Assess the financial stability of the vendor before contracting. Vendors facing financial difficulties may be unable to deliver on contracts or maintain adequate levels of service, which can disrupt your operations.
Third-Party Legal Risks
It’s important to ensure that vendor contracts clearly define responsibilities, including liability for data breaches, intellectual property concerns, and compliance with industry regulations.
Third-Party Cyber Risks
Information security risks are among the most significant posed by third-party vendors. Vendors can inadvertently introduce vulnerabilities into your organization’s network, allowing cybercriminals to gain access to sensitive data – or push out flawed software, crashing your network First parties must in effect manage at arm’s length these potential attack vectors:
- How data flows to vendor organizations and back
- How vendors manage access
- Their behavior – do employees click on phishing emails, etc.
Therefore, it’s essential to assess a vendor’s cybersecurity measures, including their encryption protocols, access controls, and adherence to industry-specific regulations like the Health Insurance Portability and Accountability Act (HIPAA).
Top 10 Cybersecurity Controls in Vendor Risk Management
Extensive research into third-party cyber risk has identified this minimum (but mighty) list of controls for third party cyber risk management (TPRM). Any first party should determine the presence and ideally monitor the performance of these controls at the third party.
1. Email Security Protections
2. Endpoint Detection and Response (EDR)
3. Multi-Factor Authentication (MFA)
4. Secured Software
5. Secure Web Gateway (SWG)
6. Security Conscious Personnel
7. User Access Control
8. Incident Response
9. Data at Rest Encryption
10. Data Loss Prevention (DLP)
Key Differences between a Vendor, Third-Party, Supplier, and Service Provider
The terms “vendor,” “third-party,” “supplier,” and “service provider” are often used interchangeably but they have distinct meanings that can influence how risks are managed on both the contracting organization and the vendor.
Why Is Vendor Risk Management More Important than Ever?
The digital transformation of industries has resulted in more complex vendor ecosystems. With organizations relying on multiple third-party providers for essential services, even one weak link in the supply chain can result in disastrous consequences.
What Are the Benefits of Vendor Risk Management?
- Business Continuity: By assessing vendor risks – especially identifying key vendors that could be single points of failure –companies can prevent potential disruptions due to vendors
- Enhanced Cybersecurity: A proactive approach to VRM helps organizations minimize the cybersecurity risks posed by third parties but also enables a 360-degree view of the organization’s aggregated risk.
- Regulatory Compliance: VRM ensures that vendors comply with industry regulations, such as GDPR, HIPAA, and others, reducing the risk of non-compliance penalties to the first party contractor organization.
- Financial Protection: Avoiding financially unstable vendors minimizes the risk of disruptions and losses due to vendor insolvency.
Key Components of a Vendor Risk Management Strategy
- Clear Guidelines in Vendor Contracts: Define expectations, roles, and responsibilities in vendor contracts and penalties for non-compliance or breach of contract, including liability for data breaches.
- Assessment of Vendor Security Posture: Ideally, first parties should foster a cooperative relationship with vendors to voluntarily achieve visibility into the systems, controls and security practices.
- Continuous Monitoring: Continuous monitoring is essential to ensure ongoing compliance and performance. Advanced Vendor Risk Management (VRM) systems offer always-on visibility into controls status via API feeds.
- Assessment of First-Party Security Posture vs Vendors: Using zero trust, least privilege or other strategies, limit the access by and potential damage from vendors.
How to Implement Your Vendor Risk Management Program
1. Choose the Right Software
Caution: Many VRM solutions today fall short on delivering a comprehensive, actionable VRM. Common practices include:
Self-assessment questionnaires
Problems: “Checklist approach” – assumes that the presence of controls reduces risk, though with no indication of how well the controls perform. Questionnaire submission process is typically lengthy.
Cybersecurity ratings services
Problems: Conduct a scan of the third party’s network as visible from the outside plus a check on publicly available information to produce a loosely defined numeric rating. Result is just a partial view of the third party’s risk
Compliance with frameworks
Problems: A self-attestation that the third party has in place controls recommended by framework such as SOC 2 but rarely conducted by an outside auditor; typically limited in scope.
An advanced VRM solution enables effective third party cyber risk management (TPRM) with features such as
- Automated ingestion and cataloging of questionnaires, certifications and other security documentation.
- Real-time monitoring of controls status
- Prioritization among vendors based on risk exposure, defined as breach likelihood and probable financial impact
2. Educate Your Team
Provide training to ensure your team understands how to effectively use the software and the key underlying concepts of risk management
3. Create a Comprehensive Vendor List
Compile or import a detailed inventory of vendors, specifying the risk-exposure attributes you wish to track, such as redundancy of services.
4. Categorize Your Vendors
Organize vendors into tiers based on their risk levels in financial terms and importance to your operations (and not based on size of contract). Watch out for potential single points of failure.
5. Select an Assessment Framework
Identify the most suitable assessment standards or frameworks for your organization and industry. There are various assessment frameworks you can use to evaluate vendor potential risks, including ISO 27001, NIST, and FAIR, ideally verified by an outside auditor. Remember the goal is assessment in business terms, not just meeting technical standards.
6. Establish Your Risk Assessment Process
Develop a structured approach for conducting vendor assessments, including key questions to guide the vendor risk management process. This should include sending out questionnaires, performing audits, and evaluating the vendor’s financial, legal, cybersecurity, and other risks.
7. Define Your Risk Calculation Methodology
Create a method for evaluating risks, utilizing tools that perform quantitative cyber risk assessment in financial terms, based on a standard model such as FAIR. Use software that performs “what-if” analysis to assess whether new controls should be implemented to handle new risk scenarios, taking into account return on investment.
8. Implement Automation Workflows
To manage the very large vendor ecosystem that major enterprises support, automated systems are a must-do for instance, to send and evaluate assessment questionnaires, generate risk reports, and monitor vendor compliance. Advanced VRM systems today leverage artificial intelligence (AI) to speed the process.
9. Develop Reporting Tools and Dashboards
Create reports and dashboards to visualize key metrics related to vendor risk management, particularly for the highest value/highest risk vendors. Dashboards should be continuously updated.
10. Continuously Improve Your VRM Program
Regularly review and refine your VRM processes to adapt to new audit or compliance requirements and new threat intelligence.
Vendor Risk Assessment Process
To effectively assess vendor risks, follow these steps:
- Initial Evaluation: Begin by sending vendors questionnaires that assess their security practices, financial stability, and legal compliance.
- Tiered Risk Scoring: Establish a scoring system that ranks vendors based on the likelihood and probable impact of the risks they pose, expressed in financial terms. This will help prioritize high-risk vendors for deeper evaluations.
- Continuous Monitoring: Once the initial evaluation is complete, continue monitoring vendors through regular audits, security reviews, and performance assessments. With the vendor’s cooperation, perform inside-out scans of their controls for a continuous read on their risk posture.
Best Practices for Effective Vendor Risk Management
- Cross-Functional Collaboration: Engage multiple departments such as HR, IT, and legal to ensure a holistic approach to vendor risk management.
- Training and Awareness: Implement ongoing training for both employees and vendors to enhance security awareness and reduce human error.
- Utilize VRM Software: Leverage technology to automate processes, manage risks more effectively, and ensure compliance.
- Collaborate with vendors: Vendors and the contracting first parties share a mutual interest in a successful vendor relationship – real-time information sharing through APIs is easier than ever.
- Treat third parties as potential threats: Implement zero trust, least privilege and other techniques to limit the capability of vendors even unintentionally to do harm to your systems.
What Are the Benefits of Using Vendor Management Software?
Vendor management software streamlines the VRM process by automating vendor risk assessments, vendor performance tracking, and compliance management. These tools provide valuable insights into vendor risk profiles and help organizations identify and address vulnerabilities at the first and third parties before they cause problems.
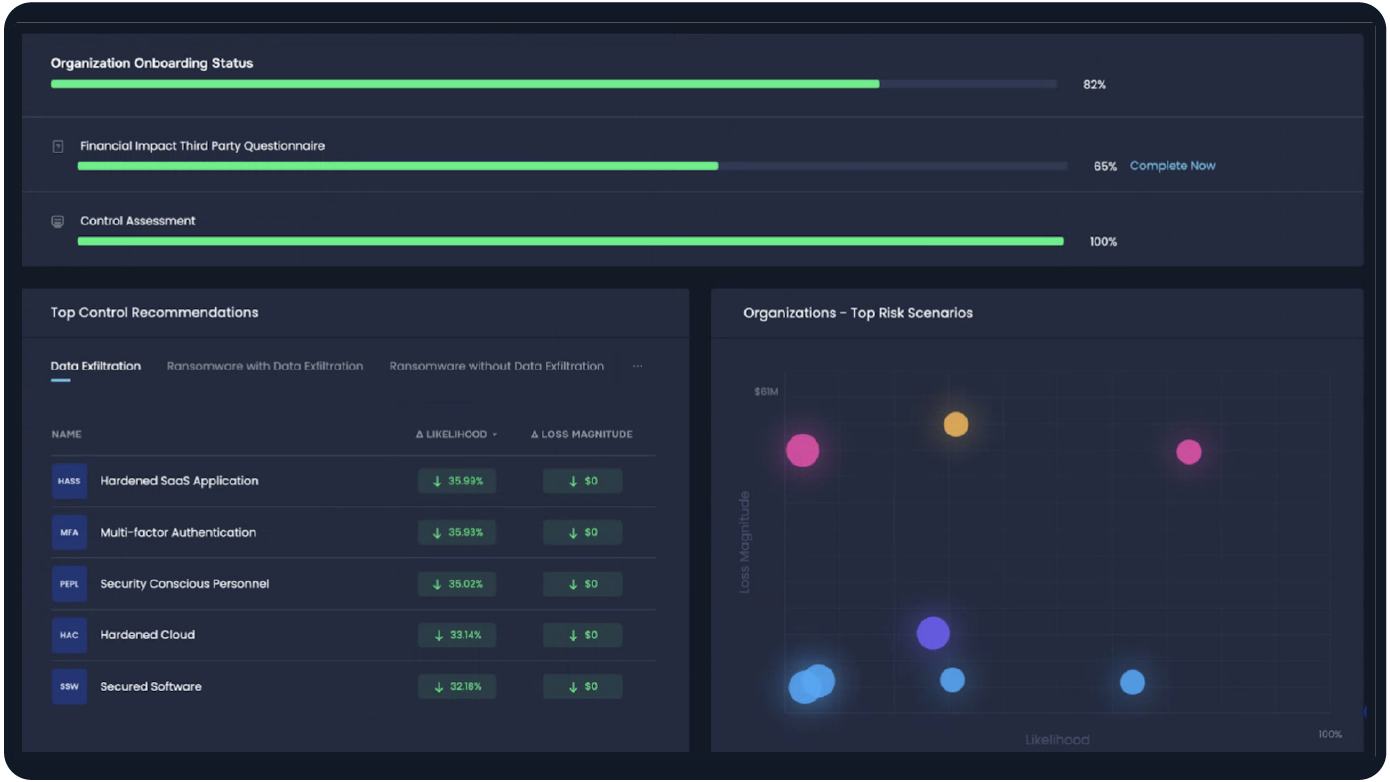
Third-party risk assessment on the SAFE One TPRM platform
SAFE’s Approach to Cyber Assessments
SAFE’s approach to cyber assessments provides organizations with the tools they need to assess, monitor, and mitigate vendor risks effectively, helping them build a more resilient and secure vendor ecosystem.
Key features of SAFE’s SAFE TPRM/VRM Solution:
- Risk-based third-party tiering based on the probable loss exposure vendors could generate.
- Guidance on zero-trust controls to safeguard against threat vectors originating in third parties.
- GenAI-powered automation for data collection and security analysis of vendors.
- Based on trusted open standards: FAIR, MITRE ATT&CK, NIST CSF.
- Comprehensive integration of feeds on threat intel and third party risk posture – plus management of first-party and third-party risk on one platform – for a unified view of risk exposure.
Let us show you the power of SAFE TPRM to solve third party and vendor risk management for your organization. Schedule a 1:1 demo today to start your re-imagined VRM journey.



