Continuous Third-Party Risk Monitoring
Always-On Third-Party Risk Management
Point-in-time assessments go stale and fail to reflect the real-time risk posture of third parties.
Missed SEC filings, ransomware group mentions, downgrades in security ratings, leaked credentials.
Programs operate with zero visibility between touchpoints, questionnaires and contract renewals.
Regulations like DORA, NIS2, and NYDFS demand ongoing oversight—not just onboarding checklists.
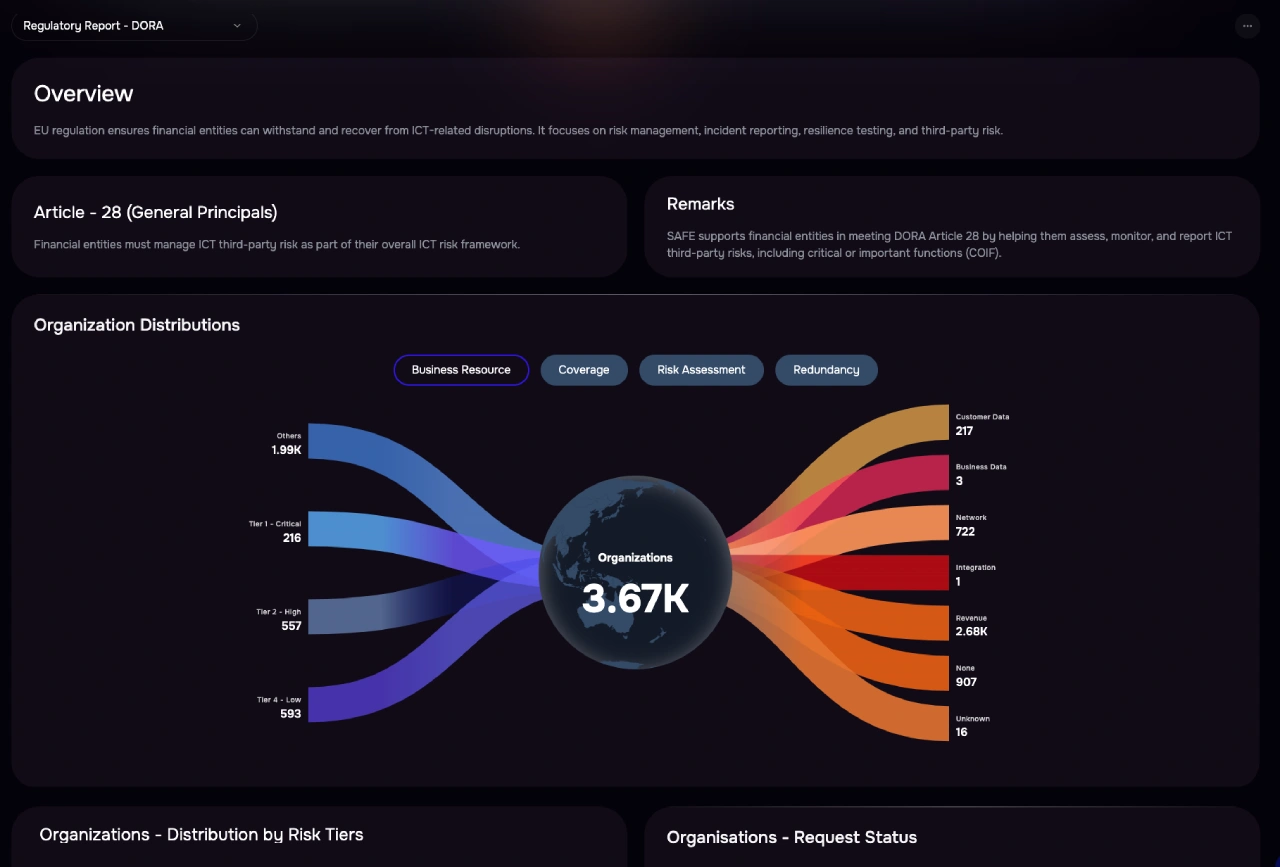




Instantly flag failed
controls, expired certifications, etc
Remain audit-ready with a real-time log of vendor risk changes
Continuously scan third parties' digital footprint, leaked data
Get real-time alerts when fourth parties are discovered
Track real-time to ransomware, system outages exposure, etc

Strengthen overall cyber resilience and align TPRM with broader business and regulatory expectations.

Prioritize actions, demonstrate due diligence to regulators, and align security with business velocity.

Move away from point-in-time monitoring towards real-time risk visibility with actionable insights.
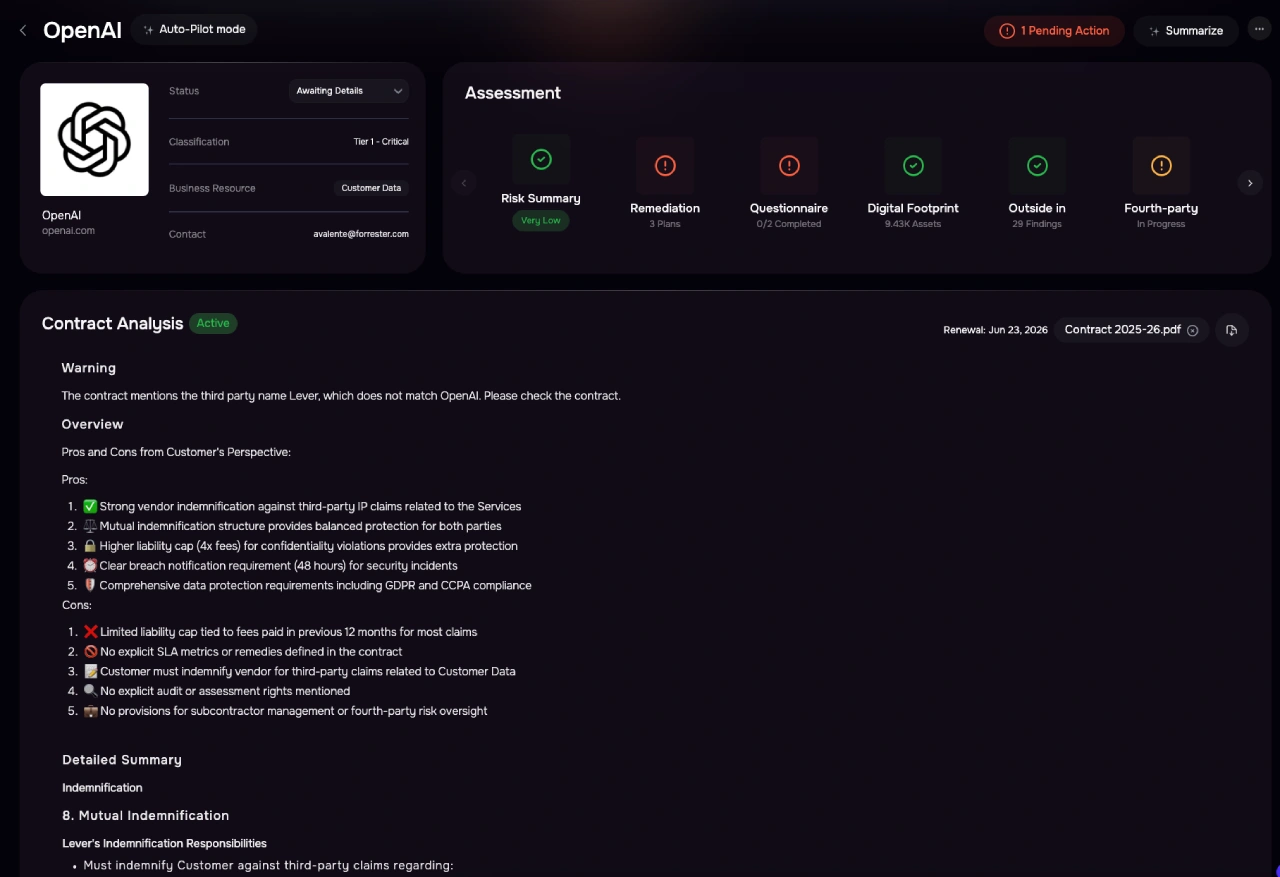
Pre-populates 95% of questionnaires with known data to save time and ensure consistency.
Builds a third party's digital risk profile using their domains, IP addresses, and web presence.
Parses trust centers to auto-extract policies, and security artifacts, and certifications like SOC2.
Continuously checks for intel from past breaches and assets including exposed S3 buckets.
Uncovers hidden fourth parties by mapping downstream vendors like AWS, Slack, Okta, and more.