4 Steps to Cybersecurity Due Diligence for M&A
Know before you merge their top cyber risks, IT governance and controls stack
By Pankaj Goyal
Given the frequency of cyber incidents and their increasing cost, cybersecurity due diligence has become a fundamental part of any merger or acquisition process. But given the sensitivity of this topic, it’s not surprising that many potential buyers are afraid to ask about cybersecurity practices during the negotiation phase.

“Can you tell me how secure the company is? We’re closing the deal in 5 minutes.”
This is a typical last-minute M&A conversation between deal and security teams. It’s also a terrible way of assessing a risk that could have detrimental impact on the purchasing company if they’re not careful.
Don’t procrastinate on cybersecurity due diligence during mergers and acquisitions.
Cyber risk needs to be assessed early on to mitigate potential threats before signing off on an acquisition. To do this effectively, companies need to develop and follow a cybersecurity due diligence process that starts with understanding the company’s security posture prior to the deal and ends with continuous monitoring and analysis post deal.
When should you perform M&A cybersecurity due diligence?
As early as possible. Be proactive. Not reactive.
A new company with poor cyber hygiene can significantly increase your company’s cyber risk when integrated. Poor security on one side can give access to the network and assets on the other side.
A cautionary example of this is when Marriott, the multinational hotel company, acquired Starwood, another hotel company that had been unknowingly compromised. The breach went unnoticed for a full 2 years after the acquisition and resulted in a data breach that impacted over 500 million people.
But can’t cybersecurity due diligence be handled post-acquisition?
Not always. Once you have identified a potential acquisition target and have agreed to a deal, it’s too late since there’s almost no opportunity for going back. That’s why cybersecurity due diligence is about acquiring the right know-how before the negotiation phase in a preemptive capacity.
What if there is an attack on the company just after acquisition? What if the company you’ve acquired is already breached? Both situations can result in financial and reputation losses. Moreover, it can negatively impact the business’ targeted returns from the acquisition. A 7-year business case suddenly might become a 10-year journey, and portfolio returns could go south.
What are the essential steps of a merger or acquisition cybersecurity due diligence process?
The cyber due diligence process should follow the financial M&A due diligence process. As you go deeper into the business, you should go deeper into cyber risk.
There are 4 steps to performing cybersecurity due diligence: understand the initial posture, understand financial and cyber risks, a telemetry-based analysis, and continuous real time monitoring.
Step 1: Understand the coverage and effectiveness of the overall governance policies, IT landscape, and cybersecurity stack of the target.
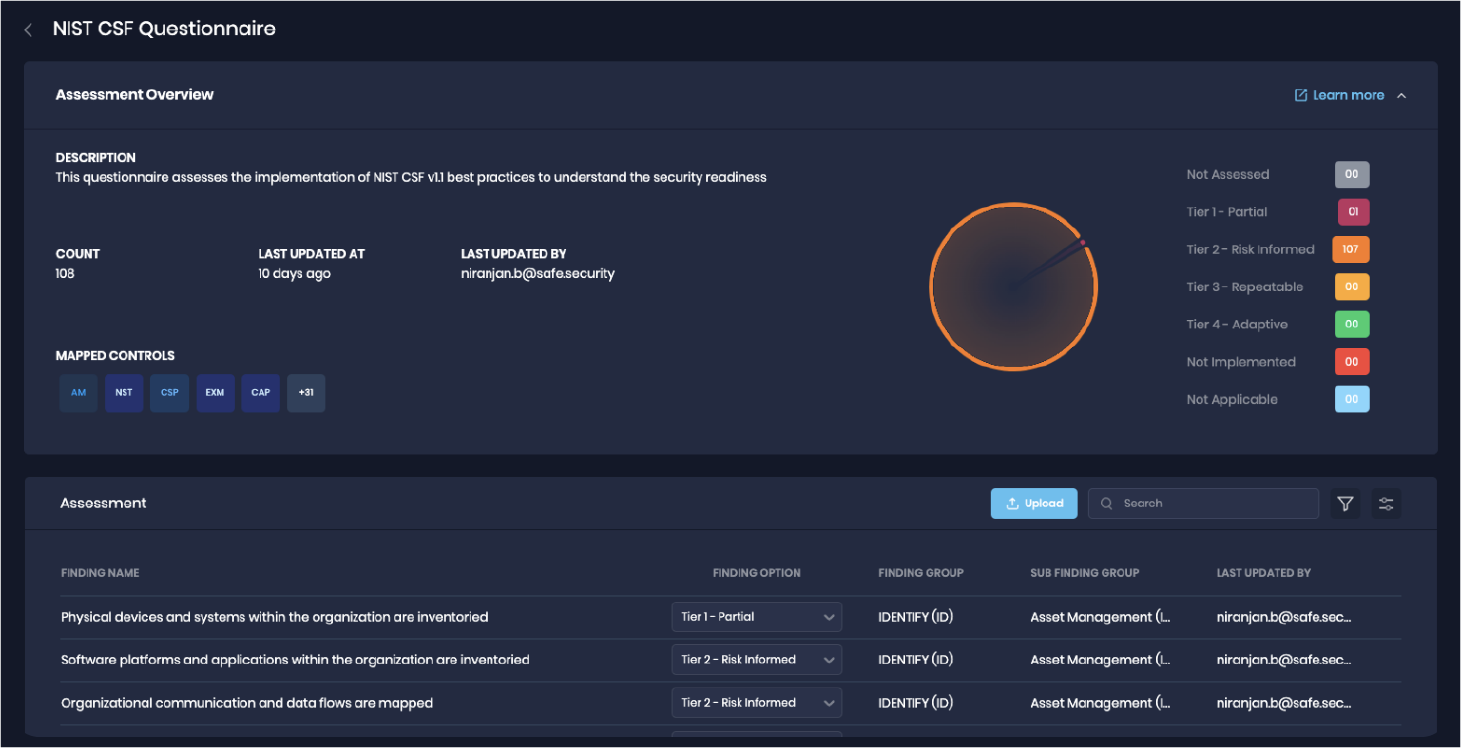
Questions to ask:
- What is the company’s cybersecurity strategy?
- What are the cybersecurity tools you are using?
- What are the cyber insurance policies of the potential acquisition target?
Step 2: Understand the financial risk carried by the target due to cyber risk.
Questions to ask:
- What are the key financial risks compounded by what cyber risks?
- Does the company have any controls in place to address these risks?
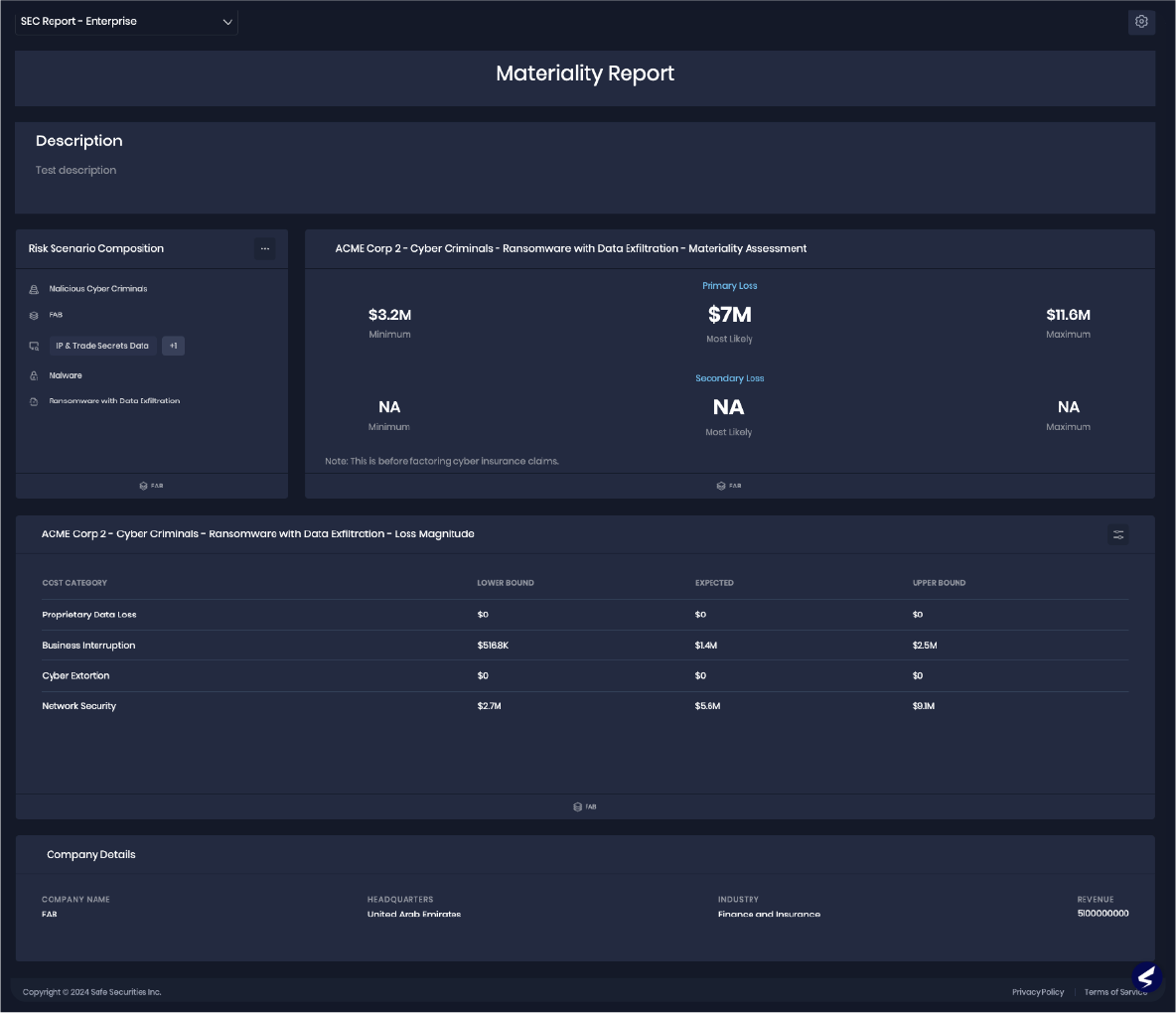
Step 3: An inside-out telemetry-based analysis to go deeper and understand the true security health.
Questions to ask:
- How compliant is the business with established cybersecurity standards?
- How do employees react when they discover a security breach?
- How does cybersecurity impact the future growth of the company?
- How effective are the security controls?
Step 4: (Post-acquisition): Continuous real time analysis during and post integration.
Questions to ask:
- Is the business staying current on cybersecurity trends?
- Are they continually addressing their risks in a timely and effective way?
- Use the SAFE One Platform to perform successful cybersecurity due diligence
The SAFE One platform was designed to help with the cybersecurity due diligence process. The system allows you to perform an efficient and effective investigation of your potential acquisition target. and enables you to assess a company’s cybersecurity strategy, their tool and tech stack, and their compliance with relevant standards.
The primary benefit of using the SAFE One platform during the merger or acquisition process is that it provides a centralized data source. The cybersecurity due diligence process is all about collecting the right data from the right stakeholders. But this can be difficult to do, especially if you have limited internal resources. SAFE One enables you to integrate cybersecurity data from internal and external sources into a centralized system and helps you to perform an efficient investigation and collect the right information.
Conclusion
The M&A cybersecurity due diligence process is all about asking the right questions. You need to understand the cybersecurity strategy of your potential acquisition target. You also need to determine whether the company has the right risk-management strategy and whether they have the right cybersecurity tools. If you manage to integrate cybersecurity into the due diligence process, you will perform an efficient investigation and determine whether your potential acquisition target is a good fit for your company.
The SAFE One platform can be deployed in under 4 weeks and can be implemented and layered over your existing cybersecurity products to give you a quantified view of cyber health, financial exposure, and actions optimized to maximize your business goals.
Want to see how SAFE One takes the guesswork out of cybersecurity? Request a session with one of our CRQ experts who will help you navigate your journey towards effective, real-time cyber risk management.



