What Is an Open Standard in Cybersecurity?
Learn what makes cyber risk analysis reliable, defensible – and a seamless, automated experience on SAFE One
At SAFE, we are proud to say that the outputs from our SAFE One platform are “transparent and defensible, purpose built on open standards such as FAIR, MITRE ATT&CK and NIST.”
But wait…what is an “open standard” in cybersecurity and how is a “standard” different from the other common terms of art you’ll hear in the cyber field, such as “model” and “framework.” It doesn’t help that cybersecurity solutions vendors often use these technical terms interchangeably because they sound so impressively technical. Let’s see if we can tease out the useful meaning of these common terms.
What is a model in cybersecurity?
A model describes the relationship among elements that produce an outcome. For instance, Factor Analysis of Information Risk (FAIR) models cyber risk by quantifying and setting in relation to each other the elements that determine the frequency and magnitude of a cyber loss event to generate a view of the probability of risk (or cyber risk quantification). Of course, reality is too complex to model so we are creating an approximation here, with help from Monte Carlo simulations that show us probable outcomes in ranges (as you would see in risk scenario analysis on the SAFE One platform.)
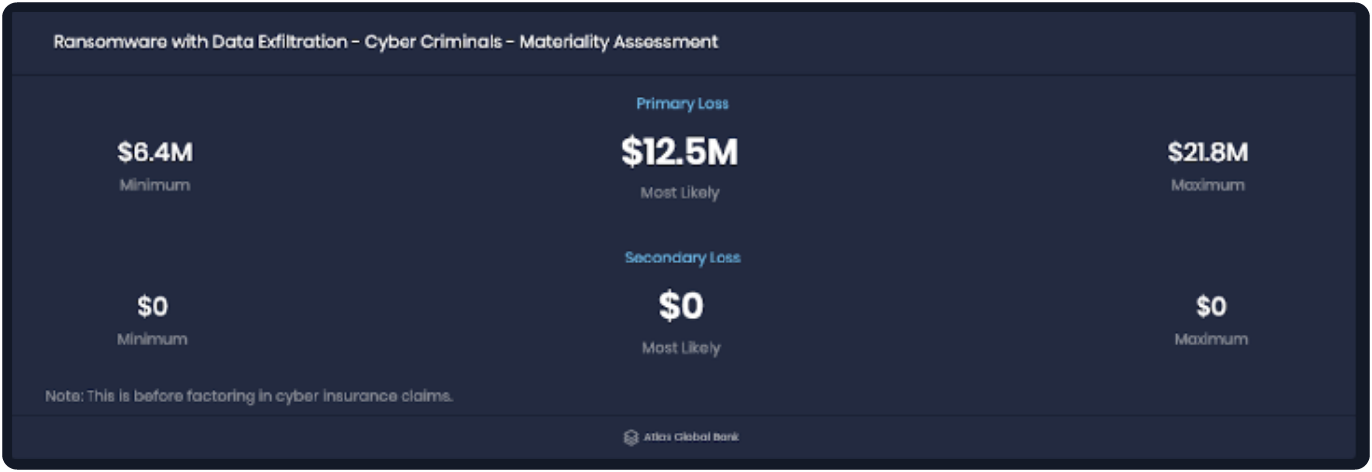
Analysis results in ranges on the SAFE One platform
As FAIR creator Jack Jones wrote in his book Measuring and Managing Information Risk, everyone uses a model to measure risk but too many are using a “mental model”, ranking risk (as “red” or “critical”) based on gut feel, not a rigorous model like FAIR.
What is a framework in cybersecurity?
A framework is an organized list of best practices for processes or controls that reduce cyber risk. The best known is the NIST Cybersecurity Framework (NIST CSF). A framework is not a model, though it’s sometimes treated like one – in other words, assessing whether controls are in place and working as intended is treated as a measurement of risk. Alone, it is not a risk measurement though that sort of status check on controls can provide useful input for FAIR analysis, for instance in gauging the susceptibility of an organization to attack (as it is used on the SAFE One platform).
What is a standard in cybersecurity?
A standard has been tested and approved by a credible group of cybersecurity professionals. The FAIR model is a standard vetted by the Open Group. The NIST CSF and the ISO 27001 are standard cybersecurity frameworks vetted by the National Institute of Standards and Technology and the International Organization for Standardization respectively. (FAIR gets an extra level of approval from NIST – the Institute includes it as an “informative reference” in the CSF.) MITRE ATT&CK is an open knowledge base and framework of attacker techniques from a government-funded research lab.
What is an open standard for cybersecurity?
Yes, “open standard” is a bit repetitious but the key point is that a standard like FAIR is completely open to inspection and challenge and has been developed through vigorous debate among hundreds of professionals before receiving the stamp of approval. Development of FAIR continues through the FAIR Institute, a professional association with more than 15,000 members, including active study groups and an annual FAIR Conference. And there’s more transparency: the FAIR book goes into great detail on the theory and practice of FAIR.
When cyber risk analysis must be defended to skeptical stakeholders in the organization, FAIR is as close as we can get to scientific proof in the world of cybersecurity.
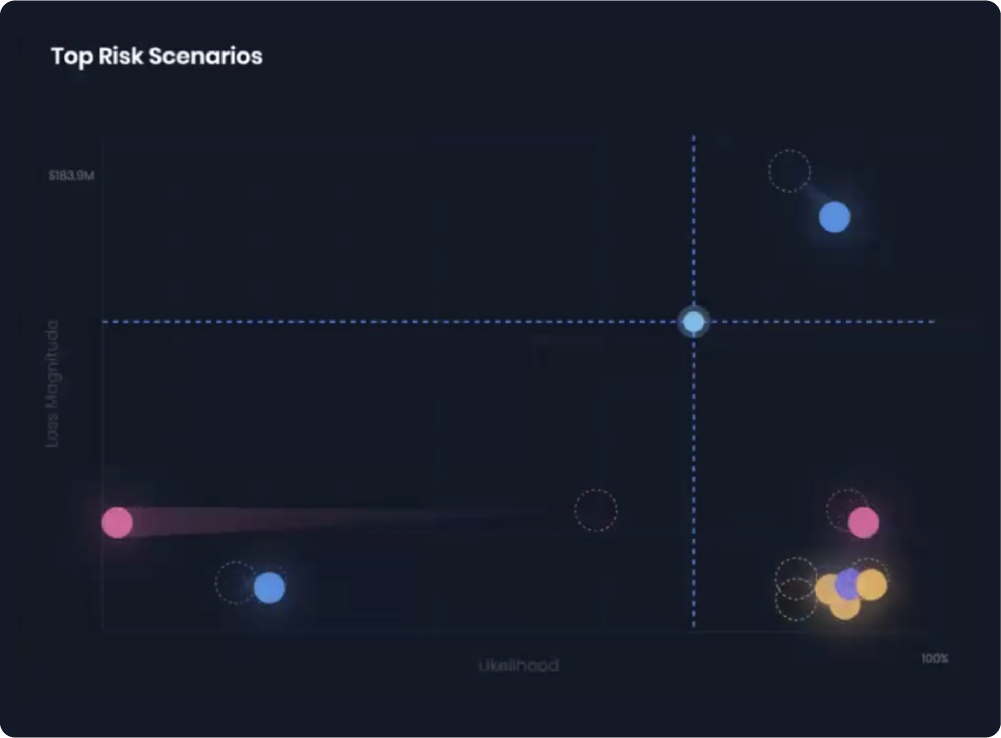
Top risks for frequency and magnitude on the SAFE One platform
So…FAIR analysis must be standard practice in cyber risk solutions
Well, no. Bringing to market an application that truly leverages FAIR is extraordinarily difficult. Look carefully at the documentation for the typical cyber risk analytics product and you’ll eventually hit a wall – a “proprietary model” that runs the machinery that can’t be described and hasn’t been evaluated by an independent third party. It may work fine but how would you know, and how could you defend it?
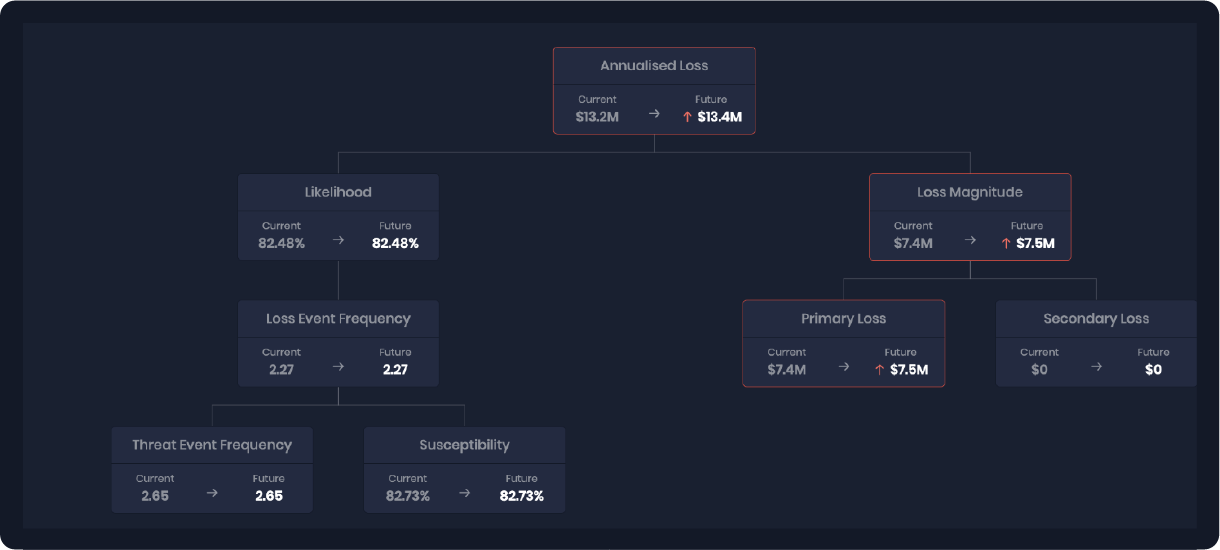
Analysis with the FAIR Model on the SAFE platform
What are the open standards used on SAFE’s SAFE One platform?
- Factor Analysis of Information Risk (FAIR). The platform automates and scales every aspect of FAIR analysis – risk scenario generation, data collection, analysis with Monte Carlo simulations, analysis reporting.
- FAIR Controls Analytics Model (FAIR-CAM). This extension of the FAIR model describes and quantifies the risk reduction effect of controls and controls systems. Using FAIR-CAM and always-on telemetry, the platform gives the most accurate read on controls status to support cyber risk analysis.
- FAIR Materiality Analytics Model (FAIR-MAM). Standardized data collection on the financial impact of cyber events based on industry data or firm-specific loss data used for FAIR-compliant loss magnitude estimation on the platform.
- SAFE TPRM – the defensibility and accuracy of FAIR analysis applied to third party cyber risk management.
- MITRE ATT&CK – Risk analysis leverages this framework’s tactics and techniques in assessing risk scenarios.
- NIST, ISO, CIS and other frameworks. The SAFE platform ingests a client’s roster of controls based on the framework in use and rates the controls environment for coverage, maturity, reliability and other parameters that play into accurate cyber risk analysis.
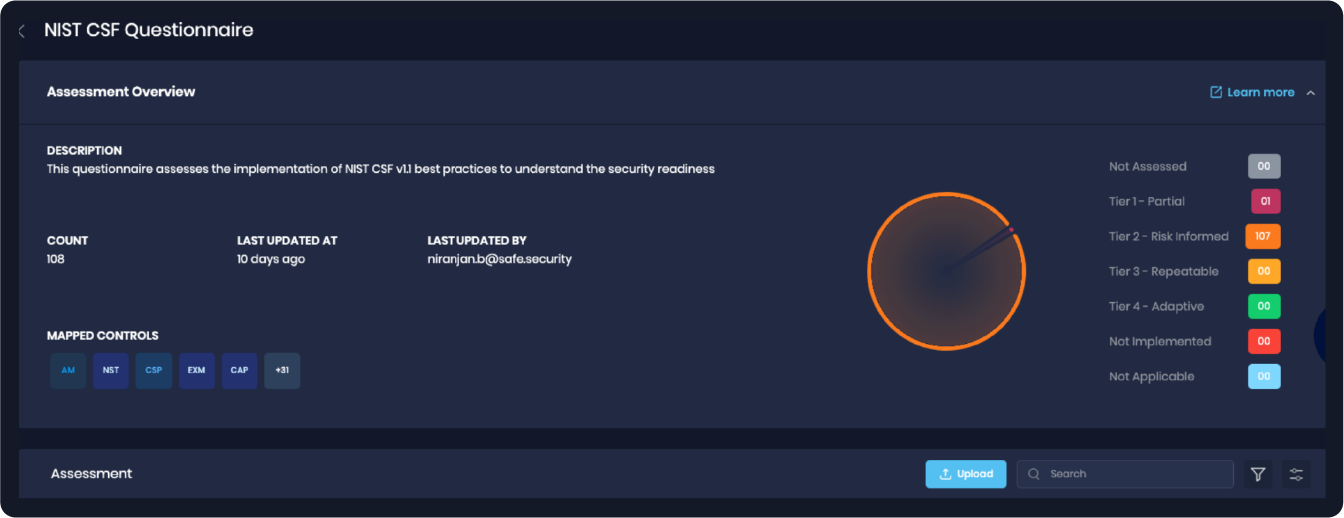
SAFE One: NIST CSF Questionnaire
Learn how SAFE can be your solution for leveraging the leading standards and frameworks in cybersecurity, with reliability and automation – contact us for a demo.


