The Modern Risk Prioritization Framework for 2026
Turn an overwhelming vulnerability management problem into a manageable task list
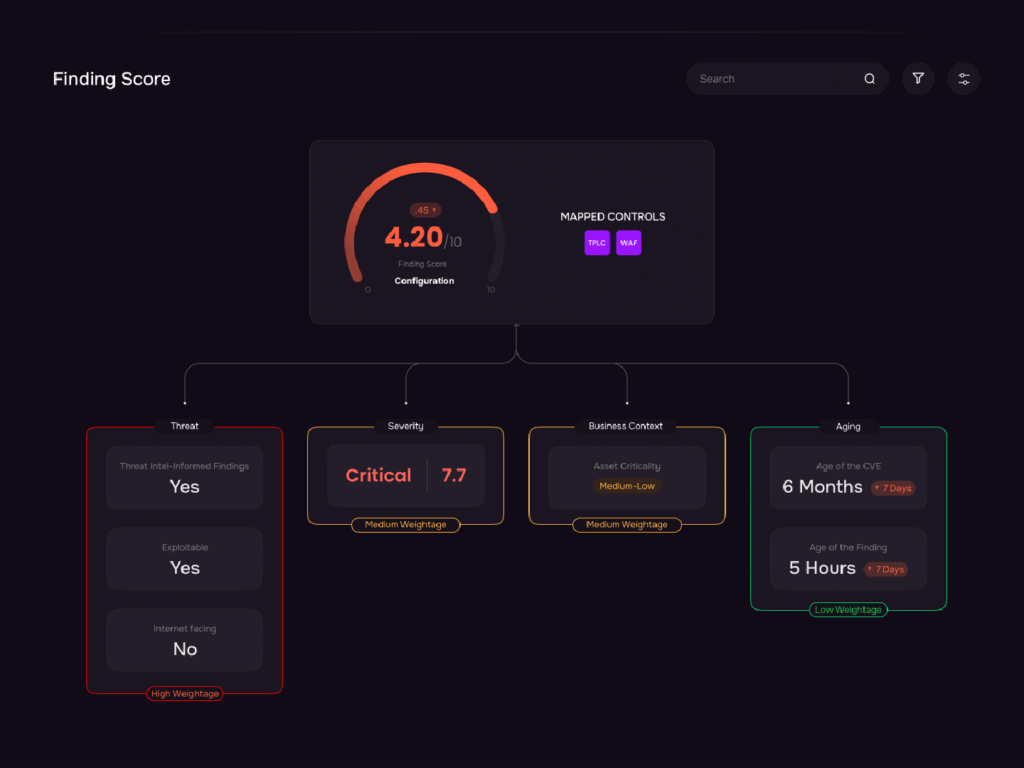
Scoring vulnerabilities – SAFE One risk management platform.
Every security team faces the same impossible math: thousands of vulnerabilities, dozens of critical assets, limited budget, and exactly one question from the board—”which risks matter most?”
Most organizations respond with color-coded spreadsheets and gut instinct, then wonder why they’re patching low-priority issues while critical exposures remain open for months.
Risk prioritization—the systematic process of analyzing and ranking identified risks based on likelihood, impact, and velocity—transforms that overwhelming inventory into an actionable hierarchy that focuses resources where they’ll actually reduce exposure.
This framework walks through the financial quantification methods, multi-dimensional scoring approaches, and continuous monitoring practices that separate effective prioritization from security theater.
What is risk prioritization?
Risk prioritization is the process of analyzing identified risks and ranking them based on their likelihood, probable impact, and other critical factors to determine which risks deserve immediate attention and resources. Instead of treating every risk equally or trying to address hundreds of potential issues at once, organizations use prioritization to create an actionable hierarchy that focuses limited time, budget, and personnel on the most consequential exposures first.
Here’s the distinction that often gets muddled: risk assessment identifies and evaluates probable risks across your environment—it answers “what could go wrong?” Risk prioritization takes that inventory and ranks each item to answer “what do we fix first?” Think of assessment as creating the full picture of your risk landscape, while prioritization decides where to deploy your defenses.
Why does risk prioritization matter in 2026?
The volume and velocity of cyber threats have reached levels that make traditional approaches inadequate. Organizations now face thousands of threats and vulnerabilities across cloud environments, legacy systems, SaaS applications, and third-party vendors—far more than any security team can address with quarterly spreadsheet reviews.
A vulnerability that ranks as low priority on Monday can become a critical exploit by Friday when proof-of-concept attack code surfaces on GitHub. Static assessments create dangerous gaps between when risks emerge and when organizations respond.
Meanwhile, regulators have caught up to this reality—the SEC’s cybersecurity disclosure rules and NYDFS amendments now expect organizations to demonstrate sophisticated, continuous risk management programs rather than checkbox exercises.
The financial stakes tell the story more clearly. Organizations with effective prioritization can focus their limited resources on closing the gaps that actually matter, while those without it waste time patching low-risk vulnerabilities while critical exposures remain unaddressed.
| Traditional Approach | Modern Approach |
| Annual or quarterly reviews | Continuous, real-time monitoring |
| Two-dimensional scoring | Multi-dimensional analysis including velocity and interdependencies |
| Manual calculations in spreadsheets | AI-augmented analysis with automated updates |
| Siloed by department or tool | Unified enterprise view across all risk domains |
Essential components for modern risk prioritization
Effective risk prioritization in 2026 requires moving beyond simple likelihood x impact matrices to incorporate multiple dimensions that reflect how risks actually materialize.
Velocity and time horizon
Risk velocity measures how quickly a threat can materialize and impact your organization once triggered. A ransomware attack can encrypt critical systems within hours, while gradual erosion of customer trust from repeated minor incidents might unfold over months. High-velocity risks often warrant immediate attention even when their probable impact is moderate, simply because you have less time to respond.
Time horizon considerations matter equally. Short-term operational risks like zero-day exploits in internet-facing applications require urgent remediation, while longer-term strategic risks like emerging regulatory requirements might justify a phased response over quarters.
Financial impact and ROI
Quantifying risk in financial terms transforms abstract threat discussions into business language that executives and boards understand. Rather than debating whether a risk is “high” or “medium,” financial quantification lets you state that a particular exposure could result in $2.3 million in expected annual loss, and that implementing a specific control would reduce that to $400,000 at an implementation cost of $150,000.
The FAIR (Factor Analysis of Information Risk) methodology provides the industry standard framework for this quantification. FAIR breaks down cyber risk into loss event frequency and loss magnitude, then further decomposes those into factors like threat capability, control strength, and various forms of loss including productivity, response costs, and fines.
Systemic interdependencies
Risks rarely exist in isolation—they connect, amplify each other, and cascade through organizations in ways that simple scoring systems miss. A vulnerability in your identity management system might have moderate direct impact, but if that system authenticates users for your financial systems, customer database, and cloud infrastructure, the actual blast radius is far larger.
Three types of interdependencies demand attention:
- Cascade effects: One risk event triggers others, like how a phishing compromise can lead to lateral movement, data exfiltration, and ransomware deployment
- Concentration risk: Multiple high-impact systems depend on a single vendor, control, or infrastructure component
- Control dependencies: Multiple risks are mitigated by the same security control, meaning that control’s failure simultaneously elevates numerous threats
How to calculate a risk prioritization number
A Risk Prioritization Number (RPN) provides a quantitative method to compare and rank risks, borrowed from manufacturing’s FMEA (Failure Mode and Effects Analysis) approach but adapted for cybersecurity contexts.
1. Identify likelihood metric
Likelihood represents the probability or frequency that a risk event will occur within a defined timeframe, typically one year. Rather than vague terms like “possible” or “likely,” effective likelihood assessment uses historical data, threat intelligence, and environmental factors to produce defendable estimates.
Start by examining your own incident history—how often have similar events occurred in the past? Then layer in threat intelligence about active threat actors targeting your industry, publicly disclosed vulnerabilities in your technology stack, and observable attack trends. Finally, assess your control environment’s effectiveness at preventing or detecting this particular threat.
| Score | Description | Frequency |
| 1 | Rare | Less than 1% annual probability |
| 2 | Unlikely | 1-10% annual probability |
| 3 | Possible | 10-33% annual probability |
| 4 | Likely | 33-66% annual probability |
| 5 | Almost Certain | Greater than 66% annual probability |
The key is consistency—everyone assessing likelihood uses the same definitions and considers the same factors.
2. Determine impact ranges
Impact quantifies the potential consequences if a risk materializes, ideally in financial terms but sometimes using operational or reputational measures when direct financial translation proves difficult. The most comprehensive impact assessments consider multiple loss categories rather than a single aggregate number.
For a ransomware scenario affecting manufacturing operations, you might calculate three days of lost production at $500,000 per day, $200,000 in incident response costs, and $100,000 in system restoration expenses for a total impact of $1.8 million. That’s cold, hard cash—not abstract severity ratings.
3. Combine for priority score
The basic RPN calculation multiplies likelihood by impact to produce a priority score: RPN = Likelihood × Impact. Using our ransomware example with a likelihood of 4 (likely) and impact of $1.8 million, the RPN would be 7.2 million risk units—a number you can compare against other risks in your environment.
Some organizations add a third dimension for detectability or control effectiveness. If you have strong detection capabilities for a particular threat, you might reduce its effective priority since you’ll catch and respond to it quickly. The enhanced formula becomes: RPN = Likelihood × Impact × Detectability, where detectability is scored inversely (1 = excellent detection, 5 = poor detection).
4. Validate and adjust
Raw RPN calculations provide a starting point, but human judgment remains essential for final prioritization. Convene cross-functional experts to review the top-ranked risks and validate that the scores reflect organizational reality and risk appetite.
Compare your prioritized list against industry benchmarks and peer organizations’ experiences. If your RPN ranks third-party vendor risk as relatively low but industry data shows vendor compromises as a leading attack vector, revisit your likelihood and impact assumptions.
Using a vulnerability prioritization matrix
A vulnerability prioritization matrix specifically addresses the challenge of ranking technical security weaknesses across your infrastructure, applications, and systems. While general risk prioritization considers all threat types, vulnerability prioritization focuses on known software flaws, misconfigurations, and security gaps that attackers could exploit.
The classic vulnerability matrix plots two dimensions: likelihood of exploitation on one axis and business impact on the other. This creates a visual grid typically divided into nine zones, with the top-right quadrant representing high-likelihood, high-impact vulnerabilities requiring immediate remediation.
However, basic severity scores like CVSS (Common Vulnerability Scoring System) often mislead prioritization efforts. A vulnerability might have a CVSS score of 9.8 (critical) but exist on an isolated development system with no internet exposure and no access to sensitive data. Meanwhile, a moderate CVSS 6.5 vulnerability in your internet-facing authentication system with active exploits in the wild deserves far higher priority.
Effective vulnerability prioritization incorporates multiple factors:
- Exploit availability (public exploit code or active exploitation in the wild)
- Asset criticality (sensitive data or critical business functions)
- Compensating controls (other security measures reducing exploitability)
- Exposure (internet-accessible versus internal-only systems)
Organizations managing thousands of vulnerabilities across cloud and on-premise environments can’t manually assess each one. Automation becomes essential—platforms that integrate with vulnerability scanners like Tenable, Qualys, Rapid7, Wiz, and Prisma Cloud can automatically apply business context and threat intelligence to produce actionable priority rankings.
Request a demo to see how SAFE CTEM unifies exposure data from multiple scanning tools and automatically prioritizes vulnerabilities based on exploitability, business criticality, and control coverage.
Step-by-step, risk-based prioritization process
Risk-based prioritization follows a structured methodology that ensures consistency, defensibility, and alignment with business objectives.
1. Define objectives and criteria
Before assessing any risks, establish clear criteria for what makes a risk “high priority” in your organization’s context. Your risk appetite statement defines how much risk the organization is willing to accept in pursuit of its objectives—a fintech startup might accept higher operational risks to achieve rapid growth, while a healthcare provider’s risk appetite for patient data exposure would be near zero.
2. Identify and assess risks
Comprehensive risk identification draws from multiple sources rather than relying on any single method. Facilitated workshops with business and technology leaders surface strategic and operational risks, while technical assessments like penetration testing and vulnerability scanning reveal security weaknesses.
Historical incident analysis reveals patterns in your organization’s actual risk materialization. If you’ve experienced three phishing-enabled business email compromise attempts in the past year, that historical frequency informs your likelihood assessment for similar future events.
3. Score and rank
Apply your prioritization framework consistently across all identified risks. Consistency is crucial—if different teams use different scales or interpret criteria differently, your final prioritized list will be meaningless.
Common biases can skew prioritization if you’re not careful. Availability bias causes teams to overweight recent or memorable incidents while underestimating risks that haven’t materialized recently. Anchoring bias occurs when initial estimates unduly influence subsequent assessments. Combat these by using structured assessment methods, multiple independent reviewers, and historical data rather than intuition alone.
4. Implement mitigation
Once you’ve ranked your risks, develop targeted mitigation strategies matched to each risk’s priority level. Critical risks might warrant immediate remediation regardless of cost, while moderate risks might be addressed through existing change management cycles, and low risks might simply be accepted with periodic monitoring.
Resource allocation follows priority ranking—your top-ranked risks receive proportionally more budget, personnel, and executive attention than lower-ranked items. However, practical constraints sometimes require adjusting the pure priority order.
5. Review and update
Risk prioritization is never “done”—it requires continuous monitoring and periodic reassessment as conditions change. Quarterly formal reviews work well for most organizations, with additional ad-hoc reassessments triggered by significant events like new threat intelligence, major business changes, or actual security incidents.
Track the effectiveness of your mitigation efforts by measuring actual risk reduction. If you implemented multi-factor authentication to address credential compromise risk, monitor authentication logs and incident rates to confirm the expected risk reduction materialized.
Best practices for ongoing risk prioritization
Maintaining an effective risk prioritization program over time requires embedding certain practices into your operational cadence.
1. Use continuous monitoring
Real-time data integration transforms risk prioritization from a periodic exercise into a continuous capability. When your prioritization system automatically ingests data from security tools, threat intelligence feeds, and business systems, it can detect changes that warrant reprioritization without waiting for the next quarterly review.
Automated data collection eliminates the manual effort that makes frequent reassessment impractical. Rather than security analysts spending days gathering information for each review cycle, the system continuously pulls telemetry from firewalls, endpoint protection, cloud security platforms, and vulnerability scanners.
2. Align with regulatory frameworks
Regulatory compliance increasingly demands demonstrable, systematic risk management rather than checkbox exercises. The SEC’s cybersecurity disclosure rules require material cyber incidents to be reported within four days and annual disclosure of cyber risk management and governance processes. NYDFS requires covered entities to maintain comprehensive cybersecurity programs based on regular risk assessments.
Mapping your risk prioritization methodology to established frameworks like NIST CSF, ISO 27001, and FAIR provides multiple benefits. It demonstrates due diligence to regulators and auditors, ensures you’re addressing industry-recognized risk categories, and facilitates communication with external stakeholders who understand these frameworks.
3. Involve cross-functional teams
Effective risk prioritization requires perspectives beyond the security team alone. Business unit leaders understand operational impacts and can articulate which systems are truly critical to revenue and customer service. Finance teams can validate loss magnitude estimates and calculate mitigation ROI. Legal and compliance teams identify regulatory risks and potential liability exposures.
Establish structured governance with clear roles and escalation paths. A risk committee that meets monthly might include representatives from security, IT, business units, finance, and legal, with authority to approve mitigation plans up to a defined spending threshold.
4. Measure ROI regularly
Demonstrating the value of risk prioritization and mitigation investments builds ongoing support and funding for your security program. Track multiple metrics that tell a complete story about risk reduction and program effectiveness.
Financial quantification makes these metrics particularly compelling—being able to state that your efforts reduced enterprise cyber risk by $12 million in expected annual loss resonates with CFOs and boards. Compare incident rates before and after implementing major controls or prioritization changes to validate that your prioritization methodology correctly identified the most impactful risks.
Accelerate security with a unified approach
Fragmented risk data creates blind spots and inefficiencies that undermine even the most sophisticated prioritization methodology. When vulnerability data lives in one system, threat intelligence in another, asset inventory in a third, and business context in spreadsheets and tribal knowledge, assembling a complete risk picture requires enormous manual effort.
A unified platform approach consolidates risk data from across your entire digital ecosystem—enterprise infrastructure, cloud environments, SaaS applications, and third-party vendors—into a single intelligent system.
Consistent scoring methodology across all risk domains ensures you’re comparing apples to apples. Rather than having infrastructure vulnerabilities scored on one scale, application security risks on another, and third-party risks on yet another, a unified platform applies the same financial quantification and business context to every risk type.
SAFE’s platform delivers autonomous cyber risk management powered by Agentic AI, with over twenty-five specialized AI agents that handle data ingestion, control validation, exposure correlation, and vendor monitoring. Organizations using SAFE can quantify cyber risk in financial terms aligned with FAIR standards, prioritize mitigation based on expected risk reduction and ROI, and automate continuous monitoring across their enterprise and supply chain.
Request a demo to see how SAFE transforms fragmented cybersecurity data into clear, financially quantified insight that enables data-driven risk prioritization.
Frequently asked questions about risk prioritization
What makes risk prioritization different from risk assessment?
Risk assessment identifies and evaluates probable risks across your environment, creating a comprehensive inventory of what could go wrong. Risk prioritization takes that inventory and ranks each item to determine which risks deserve immediate attention and resources, transforming an overwhelming list into an actionable hierarchy based on likelihood, impact, and other critical factors.
How often do organizations update their risk prioritization?
Most organizations conduct formal risk prioritization reviews quarterly, with additional ad-hoc reassessments triggered by significant events like major threat intelligence, substantial business changes, or actual security incidents. Organizations with continuous monitoring capabilities can reassess and reprioritize risks in real-time as conditions change.
What tools can automate the risk prioritization process?
Modern cyber risk quantification platforms with AI capabilities can automate data collection from security tools, calculate risk scores using models like FAIR, and continuously update prioritization as new information emerges. Specialized GRC platforms offer templates and workflows for more manual prioritization processes, while vulnerability management tools provide automated prioritization specifically for technical security weaknesses.
How can teams handle risks that score equally in prioritization?
When multiple risks receive identical priority scores, consider additional tiebreaker factors like implementation cost of controls, strategic alignment with business initiatives, dependencies between risks, and organizational capacity to address each risk. The risk that’s cheaper to mitigate, aligns with planned projects, or blocks other risks from being addressed might deserve priority even when the base scores are equal.
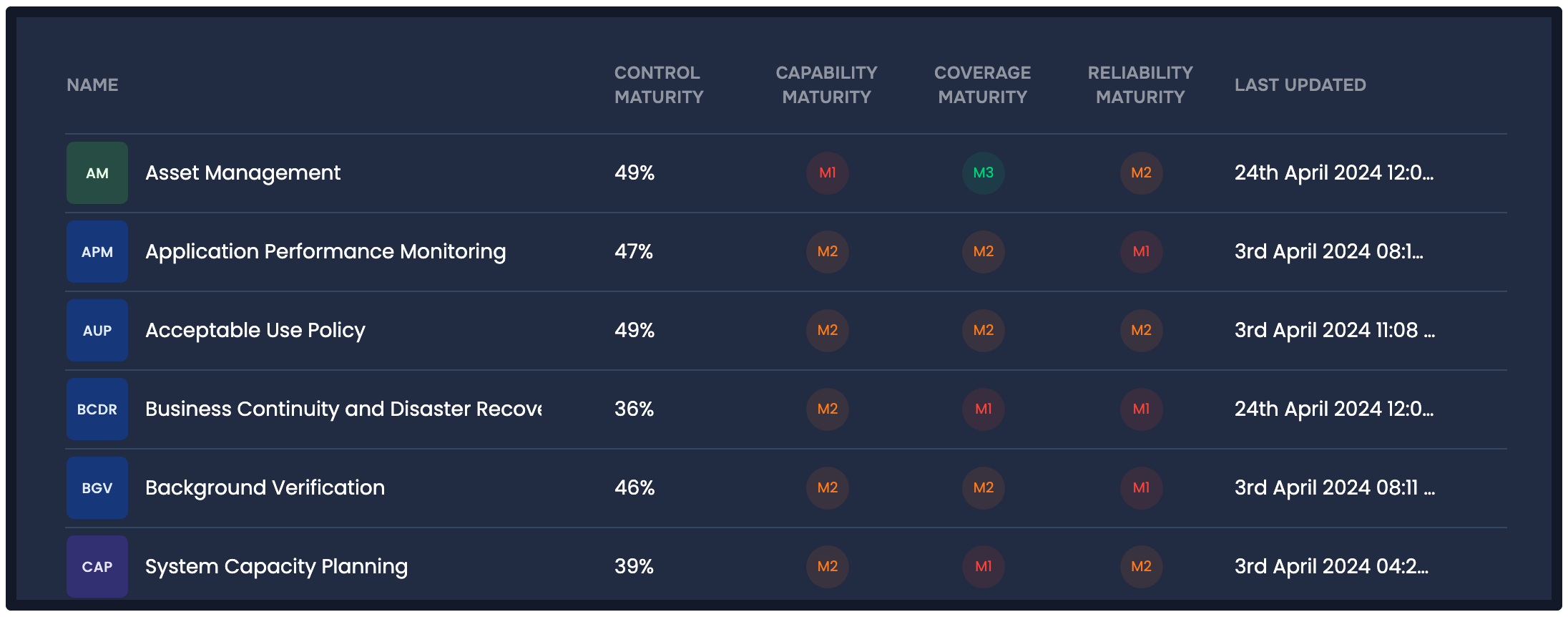
FAIR-CAM analysis of controls, SAFE One platform
How does SAFE handle prioritization of vulnerabilities?
SAFE offers risk-based scoring of vulnerabilities (also known as “findings”) based on the FAIR and FAIR-CAM (controls analytics) standards that allows us to go beyond traditional vulnerability management by linking controls directly to risk. This enables us to not only identify weaknesses but also measure the value of a control’s ability to reduce risk.
This highly accurate process runs on eight categories of data (severity scores, number of assets with open vulnerabilities, internet-facing assets, etc.) and and a six-step priorization methodology:
- Age Index Calculation
- Accounting for the Impact of Aging
- Including the Impact of Exploitable Findings
- Incorporating Business Criticality
- Adusting for Internet-facing Assets
- Adjusting for Threat-Intel-Informed Finding
- Deriving the Final Finding Score
Get the details in this blog post: Understanding the Risk-based Scoring of SAFE’s Findings Prioritization
Let us show you how SAFE can help you build a more robust cybersecurity posture. Schedule a demo.



