The Uber Breach:Why real-time monitoring of signals across your attack surface is crucial

Uber hit the headlines last week following reports of a successful breach of its internal systems. The latest security intelligence reveals employee credentials were either obtained from dark web forums or through a social engineering attack on an Uber employee.
Verizon’s 2022 Data Breach Investigations Report revealed 82% of breaches involved a human element, such as social attacks, errors, and misuse. It will continue to be a target due to increasing volumes of external assets and the rapid adoption of cloud technologies and storage. Coupled with the recent pandemic and the shift to remote working, organizations should expect more attacks like this and actively measure their own risk.
Attack Analysis: an effective combination for attackers
SAFE’s Threat Research team has analyzed two similar incidents this week. In one case, our security team assisted an organization in its post-breach analysis which revealed that stolen credentials were used to gain access to its internal network.
During adversary simulation exercises carried out for customers, our offensive security team has utilized this method on multiple occasions to gain internal network access. Stolen/leaked credentials and external remote services prove an effective combination for attackers to gain an initial foothold in an organization’s network, enabling them to avoid any active scanning that is often detected and blocked by perimeter security solutions.
Mapping the breach to MITRE ATT&CK
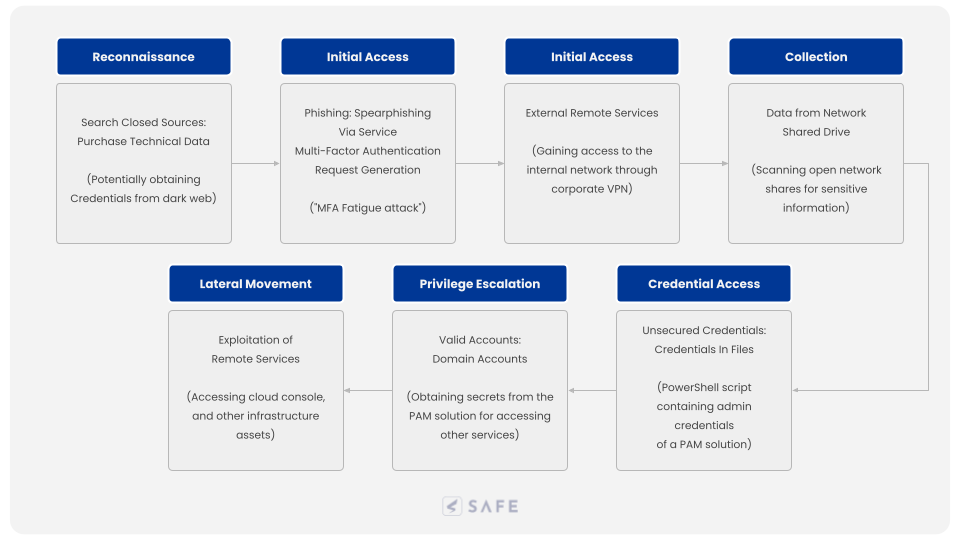
| Tactic | Technique | Details |
| Reconnaissance | Search Closed Sources: Purchase Technical Data | The attackers behind the Uber breach claimed that they secured access to credentials through social engineering. However, a Twitter thread by Group-IB suggests they may have gained access to username and password credentials through dark web exposures. |
| Initial Access | Phishing: Spear Phishing via Service | A conversation between the adversary and security researcher, Corben Leo, revealed that access was gained to Uber’s intranet following a successful social engineering attack on an employee. They did not disclose exactly how they obtained the credentials but did confirm that they attempted to log in as the employee. |
| Credential Access | Multi-Factor Authentication Request Generation | The employee account was protected with multi-factor authentication (MFA). To bypass this, the adversary allegedly used an MFA fatigue attack, then impersonated Uber IT support to persuade the employee to accept the MFA request. |
| Initial Access | External Remote Services | During the conversation with Corben Leo, the attacker disclosed that after obtaining the credentials, they logged into Uber’s internal network via the corporate VPN and began scanning their intranet for sensitive information. |
| Credential Access | Unsecured Credentials: Credentials In Files Credentials from Password Stores: Password Managers | During the scans, the adversary claims that they discovered a PowerShell script containing admin user credentials (in cleartext) for Thycotic, Uber’s privileged access management platform. This was used to access and retrieve further login credentials for Uber’s other internal applications. |
| Collection | Data from Network Shared Drive | |
| Lateral Movement | Exploitation of Remote Services | Company applications accessed by the attacker include its Amazon Web Services Console, VMWare vSphere/ESXi virtual machines, Slack, Hacker One portal, and a Google Workspace admin dashboard for managing Uber email accounts. |
Answered: ‘Could a similar attack happen within my organization?’
In short, yes. No organization is immune, and for this reason, you need to:
- Monitor your expanding attack surface
- Correlate your different security signals in real-time
Prioritizing risk within your organization and monitoring your expanding attack surface is crucial to safeguarding your business. Security tooling will only get you so far. For example, periodic assessment of your internet-facing applications is vital, though monitoring for potential typosquat domains or data leaks in dark web forums is equally important.
This is where automation and AI become your ally: moving from point-in-time assessments to real-time monitoring will enable continuous surveillance of controls across your entire attack surface, including your internal controls, dark web, people security, and beyond. This pivot will empower you with valuable intelligence around gaps, misconfigurations, and weaknesses as they happen so you can mitigate and manage your risk at the earliest opportunity.
Correlating these signals in real-time will improve your security initiatives and your ability to minimize risk. Using phishing as an example, you may already implement FIDO-based two-factor authentication and carry out periodic phishing or security awareness campaigns. Suppose you’re monitoring the dark web for company credential leaks and happen to discover one; this exposure can be mapped and correlated with other signals such as user behavior during the phishing simulation exercise to identify ‘risky users’. You could then enroll these users into more targeted or extensive phishing education programs, such as awareness sessions on how to spot a phishing email or how to identify a malicious URL. One of the many benefits of adopting real-time monitoring and risk quantification is that you also have a tangible opportunity to notify users in real-time when their data is breached so they can change the password of their breached account, plus other accounts where they may have used this password. As a result, the user themselves is empowered and enabled to help you reduce the attack window within which the password can be used by threat actors.
The need for cyber risk quantification and management
Moving organizations away from siloed, point-in-time, manual assessments toward intelligent, automated, real-time measurement of risk is the foundation of our work and research here at SAFE. We believe quantifying risk is essential for leaders to successfully prioritize their initiatives and budgets and see the best return on their security investment.
Discover how you can implement some of the suggestions in this article and how to measure, monitor, and mitigate risk in real-time using our free resources:
- How to prioritize and allocate your cybersecurity resources
- What is cyber risk quantification? Our CRQ 101
- Improve cyber risk communications with your board
- Find out the potential financial impact of a breach on your business
- See real-time cyber risk quantification in action
References
- https://www.bleepingcomputer.com/news/security/uber-hacked-internal-systems-breached-and-vulnerability-reports-stolen/
- https://www.schneier.com/blog/archives/2022/09/massive-data-breach-at-uber.html
- https://www.bleepingcomputer.com/news/security/uber-hacked-internal-systems-breached-and-vulnerability-reports-stolen/


