Vendor Security Questionnaire (VRAQ) Best Practices
Build, deploy, and optimize TPRM questionnaires that generate financial risk metrics, not compliance checkboxes
By SAFE
Third-party vendors now account for more than 60% of enterprise cyber risk, yet most organizations still assess vendor security through manual spreadsheets, inconsistent questions, and subjective scoring that provides little actionable intelligence. When a vendor’s controls fail, the damage cascades directly into your environment—from ransomware that spreads through managed service providers to data breaches that expose millions of customer records through a single compromised supplier.
This guide covers how to build, deploy, and optimize vendor security questionnaires that generate financial risk metrics rather than compliance checkboxes, from selecting the right assessment framework to automating continuous monitoring with AI-powered validation.
What Is a Vendor Security Questionnaire?
A vendor security questionnaire is a standardized set of questions organizations use to evaluate how third-party vendors handle security, protect data, and manage cyber risk. You might also hear it called a vendor risk assessment questionnaire (VRAQ), third-party security assessment questionnaire, or IT security assessment questionnaire—they all mean roughly the same thing. The questionnaire covers areas like data encryption, access controls, incident response plans, compliance certifications, and business continuity capabilities.
Organizations typically send these questionnaires during vendor onboarding, before signing a contract, or during annual reviews of existing vendor relationships. The responses help security teams spot potential vulnerabilities in a vendor’s environment before those weaknesses can cascade into your own operations. For CISOs and third-party risk management leaders, these questionnaires provide the raw data needed to quantify actual exposure rather than just checking compliance boxes.
Why Vendor Security Assessments Matter for Cyber Risk
Third-party vendors now represent one of the fastest-growing attack surfaces for enterprises. When a vendor’s security controls fail, the damage spreads to every customer in their ecosystem—from breaches exposing millions of customer records to operational disruptions that halt business for days.
Regulatory frameworks like the SEC’s cybersecurity disclosure rules, NYDFS cybersecurity regulation, GDPR, and HIPAA explicitly require organizations to assess and monitor third-party risk. Without structured vendor assessments, organizations face regulatory penalties, failed audits, and board-level questions they can’t answer with data. The financial impact of vendor-related incidents can be substantial, yet many organizations still treat vendor assessments as a compliance exercise rather than a risk management tool.
Here’s what a well-designed vendor security questionnaire program delivers:
- Risk identification: Questionnaires reveal specific control gaps, outdated practices, or missing capabilities that translate to exploitable vulnerabilities in your supply chain
- Compliance fulfillment: Documented vendor assessments satisfy regulatory requirements and provide audit evidence of due diligence
- Due diligence documentation: Questionnaire responses create a defensible record that your organization took reasonable steps to evaluate vendor risk
- Security baseline establishment: Consistent questionnaires set minimum acceptable security standards across your vendor ecosystem
Key Components of a Vendor Security Assessment Questionnaire
An effective vendor security questionnaire covers the critical control areas that directly impact your organization’s risk exposure. While templates vary in length and complexity, comprehensive questionnaires address five core domains that reveal how vendors actually manage security, not just what policies they claim to have on paper.
Data Protection and Compliance
Data protection questions examine how vendors classify, handle, encrypt, store, and dispose of sensitive information throughout its lifecycle. You’ll want to understand whether vendors encrypt data in transit and at rest, how they segregate customer data in multi-tenant environments, and what data retention and destruction practices they follow. Questions about compliance certifications—SOC 2, ISO 27001, GDPR, HIPAA—reveal whether vendors have undergone independent audits and how recently those audits occurred.
Strong vendors can provide specific details about their data classification schemes, encryption standards like AES-256 or TLS 1.3, and compliance report dates rather than vague assurances. The difference often shows up in the specificity of their answers.
Security Controls and Vulnerability Management
This section digs into the technical controls vendors use to prevent, detect, and respond to threats. Questions cover network security architecture, endpoint protection, multi-factor authentication requirements, privileged access management, and security monitoring capabilities. Vulnerability management questions reveal how frequently vendors scan for vulnerabilities, how quickly they patch critical findings, and whether they conduct regular penetration testing.
The difference between a mature vendor and a risky one often shows up in their patch timelines—do they remediate critical vulnerabilities within days or months? That distinction matters when you’re trying to quantify your exposure.
Disaster Recovery and Continuity Plans
Business continuity questions assess whether vendors can maintain or quickly restore services after an incident. You’ll want to know their Recovery Time Objectives (RTO) and Recovery Point Objectives (RPO), how frequently they test backup restoration, and whether they maintain geographically distributed redundancy. Incident response questions reveal whether vendors have documented playbooks, 24/7 security operations capabilities, and clear communication protocols for notifying customers during security events.
Vendors who conduct annual tabletop exercises and can provide specific RTO/RPO metrics demonstrate operational maturity. Vendors who can’t answer these questions with concrete numbers raise red flags.
Vendor Personnel and Insider Threat Controls
People represent both the strongest and weakest link in any security program. Questions about personnel security examine background check requirements, security awareness training frequency and content, access provisioning and deprovisioning processes, and separation of duties. Strong vendors conduct background checks on all employees with access to customer data, provide role-specific security training quarterly, and can demonstrate that access is removed immediately upon termination.
Different industry frameworks emphasize different control areas based on sector-specific risks:
| Framework | Primary Focus | Best For | Question Count |
| SIG (Standardized Information Gathering) | Comprehensive risk domains | Large enterprises, financial services | 1,000+ (Full) / 150+ (Lite) |
| CAIQ (Consensus Assessments) | Cloud security controls | Cloud service providers, SaaS vendors | 280+ |
| VSA (Vendor Security Alliance) | Balanced security fundamentals | Mid-market vendors, general use | 100-150 |
Choosing the Right IT Security Assessment Questionnaire Template
The questionnaire template you select significantly impacts both the quality of risk intelligence you gather and the burden you place on vendors. Established frameworks provide structure and credibility, while custom questionnaires let you focus on your specific risk concerns.
The Standardized Information Gathering (SIG) questionnaire offers the most comprehensive coverage with versions ranging from SIG Lite (around 150 questions) to SIG Full (over 1,000 questions covering 20 risk domains). Financial services organizations and large enterprises favor SIG because it maps to multiple compliance frameworks and provides granular risk insight. However, the length can overwhelm smaller vendors who lack dedicated compliance teams.
The Consensus Assessments Initiative Questionnaire (CAIQ) from the Cloud Security Alliance focuses specifically on cloud service provider controls across 17 domains. If you’re assessing SaaS vendors, cloud infrastructure providers, or platform services, CAIQ provides targeted questions about multi-tenancy, virtualization security, and cloud-specific threats.
The Vendor Security Alliance (VSA) questionnaire strikes a balance between comprehensiveness and practicality with focused questions on data protection, access controls, security policies, and incident response. The VSA framework works well for mid-market organizations or when assessing lower-risk vendors who don’t require the depth of SIG.
Mapping your questionnaire to NIST frameworks—Cybersecurity Framework, SP 800-53, SP 800-171—provides several advantages. First, NIST alignment creates a common language with vendors who already follow these widely-adopted standards. Second, government contractors and organizations in regulated industries often face NIST compliance requirements that extend to their supply chain.
No single template fits every vendor relationship. A cloud infrastructure provider hosting your production environment deserves a comprehensive 500-question assessment, while a marketing vendor with no access to customer data might only need 50 targeted questions. The key is right-sizing the questionnaire based on the vendor’s inherent risk—determined by the type of data they access, the criticality of their service, and their integration with your systems.
Best Practices for Building A Vendor Security Assessment Questionnaire
Creating an effective vendor questionnaire program requires more than selecting the right template. The difference between a questionnaire that generates actionable risk intelligence and one that becomes a compliance checkbox comes down to how you design, deploy, and act on the process.
1. Identify Critical Vendors First
Not all vendors carry equal risk. Start by inventorying your vendor ecosystem and categorizing vendors into risk tiers based on three factors: the sensitivity of data they access, the criticality of their service to your operations, and the level of integration with your systems. A payment processor handling credit card data or a cloud provider hosting your customer database represents critical risk. A vendor providing office supplies does not.
Apply your most comprehensive questionnaires to high-risk vendors, moderate assessments to medium-risk vendors, and lightweight or automated assessments to low-risk vendors. This tiered approach lets you allocate limited security team resources where they’ll have the most impact.
2. Keep Questions Relevant And Updated
Cyber threats evolve rapidly—ransomware tactics, cloud misconfigurations, and supply chain attacks that weren’t concerns five years ago now represent top risks. Your questionnaires need to evolve accordingly. Review and update your templates at least annually, adding questions about emerging threats like AI security, zero-trust architecture adoption, or software supply chain controls.
After major incidents like the SolarWinds compromise or Log4j vulnerability, consider whether new questions would help you identify similar exposures in your vendor base. Remove outdated questions about deprecated technologies or controls that are no longer relevant.
3. Score And Prioritize Responses
Collecting questionnaire responses without a systematic scoring method leaves you with subjective opinions rather than comparable risk data. Develop a scoring rubric that assigns point values or risk ratings to different response options. For example, a vendor with annual penetration testing might score higher than one with no testing, while a vendor with 24/7 security monitoring scores higher than one with business-hours-only coverage.
Weight scores based on control criticality—encryption of sensitive data matters more than the frequency of security awareness training. Aggregate scores into an overall vendor risk rating (high, medium, low) that determines reassessment frequency and monitoring intensity.
4. Include Security Compliance Questionnaire Checks
Rather than sending vendors separate questionnaires for different compliance frameworks, design questions that map to multiple standards simultaneously. A single question about encryption can satisfy GDPR, HIPAA, PCI DSS, and SOC 2 requirements if properly mapped.
Ask vendors to provide evidence for compliance claims—request actual SOC 2 reports, ISO 27001 certificates, or penetration test summaries rather than accepting “yes, we’re compliant” at face value. Compliance reports from reputable auditors provide independent validation and significantly reduce the need for detailed questionnaire responses in control areas already covered by the audit.
5. Plan for Ongoing Reviews
A vendor’s security posture changes over time—new vulnerabilities emerge, controls degrade, or business changes introduce new risks. High-risk vendors typically warrant annual reassessments, while critical vendors (especially those with access to crown jewel data) might require semi-annual reviews. Significant changes like vendor acquisitions, major service updates, or security incidents trigger immediate reassessments regardless of schedule.
Between formal reassessments, continuous monitoring approaches that track vendor security ratings, breach notifications, and external threat intelligence give you early warning when a vendor’s risk profile deteriorates.
Overcoming Common Challenges in Vendor Assessments
Even well-designed vendor security questionnaire programs encounter practical obstacles that can undermine their effectiveness. Understanding the challenges and implementing strategies to address them separates mature TPRM programs from those that exist only on paper.
Questionnaire Fatigue and Coverage Gaps
Large vendors receive dozens or hundreds of security questionnaires annually, many asking nearly identical questions in slightly different formats. This questionnaire fatigueLarge vendors receive dozens or hundreds of security questionnaires annually, many asking nearly identical questions in slightly different formats. This questionnaire fatigue leads to rushed responses, copy-pasted answers from previous questionnaires, or outright refusal to complete yet another assessment. Meanwhile, your security team lacks the capacity to thoroughly review hundreds of vendor responses, creating coverage gaps where high-risk vendors slip through with minimal scrutiny.
Industry initiatives like the Shared Assessments SIG and VSA attempt to standardize questionnaires so vendors can complete one comprehensive assessment and share it with multiple customers. Consider accepting standardized assessments or joining industry consortiums where vendors complete validated assessments that multiple organizations can access. For lower-risk vendors, automated security ratings from third-party services can supplement or replace questionnaires entirely.
Data Accuracy And Validation
Vendors have strong incentives to present their security posture in the most favorable light possible, which can lead to overstated capabilities or technically accurate but misleading responses. A vendor might claim “yes” to having an incident response plan without mentioning it hasn’t been tested in three years or doesn’t cover the specific services you’re using.
For critical vendors, request supporting evidence for key control assertions—ask to see the actual incident response runbook, backup restoration test results, or penetration test executive summaries. Conduct periodic spot checks where you verify a sample of responses through interviews or documentation review.
Managing Fourth Party Risks
Your vendors rely on their own vendors—cloud infrastructure providers, software libraries, managed security services, and more. Fourth-party relationshipsYour vendors rely on their own vendors—cloud infrastructure providers, software libraries, managed security services, and more. Fourth-party relationships create transitive risk that’s difficult to assess through questionnaires alone. A vendor with excellent security controls might still expose you to risk if they depend on a fourth party with weak controls.
Include questionnaire sections that ask vendors to identify their critical subcontractors and describe how they assess and monitor those relationships. For your most critical vendors, request the right to review their assessments of key subcontractors or include flow-down security requirements in contracts that extend your standards through the supply chain.
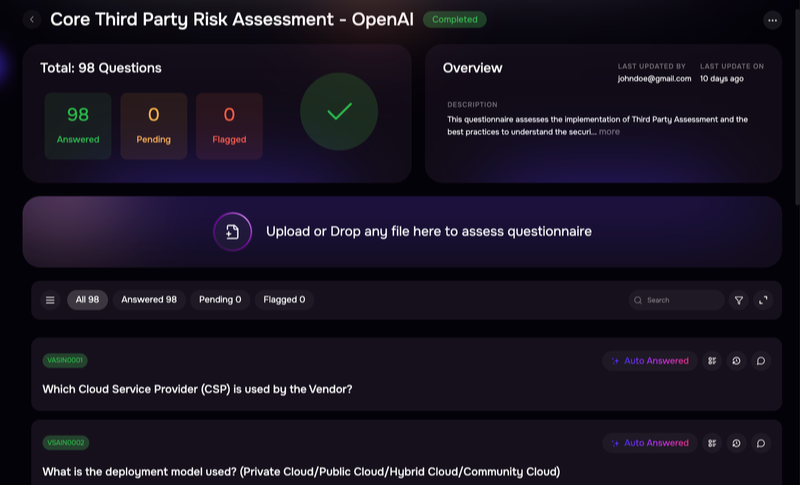
Tools And Automation for Effective Third Party Risk Management
Manual questionnaire processes—distributing spreadsheets via email, chasing vendors for responses, manually reviewing answers in isolation—don’t scale beyond a few dozen vendors. Technology can transform vendor assessments from a resource-intensive compliance burden into an efficient, intelligence-driven risk management program.
Modern TPRM platforms automate questionnaire distribution, track response completion, validate answers against previous submissions, and aggregate results into risk dashboards. The right platform reduces the time security teams spend on administrative tasks and increases the time available for risk analysis and decision-making.
Key capabilities that separate basic spreadsheet templates from enterprise-grade TPRM platforms:
- Automated distribution: Platforms send questionnaires to vendors, track completion status, send reminders, and route responses to appropriate reviewers without manual coordination
- Response validation: Automated checks flag inconsistent answers, missing evidence, or responses that contradict previous submissions or external data sources
- Integration capabilities: Connections to vulnerability scanners, threat intelligence feeds, security ratings services, and GRC platforms provide context beyond questionnaire responses
- Continuous monitoring: Real-time updates on vendor security posture, breach notifications, and external risk indicators supplement periodic questionnaires with always-current intelligence
Driving Continuous Risk Reduction with a VRAQ
The most mature organizations treat vendor questionnaires as one component of a continuous risk management program rather than an annual compliance exercise. Point-in-time assessments provide a snapshot, but a vendor’s security posture changes daily as new vulnerabilities emerge, configurations drift, and threats evolve.
Supplementing questionnaire data with external threat intelligence provides crucial context that vendors might not disclose or even know about their own environment. Security ratings services continuously scan vendor domains for exposed services, leaked credentials, vulnerable software versions, and other observable security signals. Threat intelligence feeds alert you when vendors appear in breach databases, dark web discussions, or vulnerability disclosures.
This external data doesn’t replace questionnaires—it validates and contextualizes them. A vendor might report strong patch management practices in a questionnaire, but external scanning that reveals dozens of internet-facing systems running outdated software tells a different story.
Artificial intelligence can analyze questionnaire responses at scale, identifying patterns, inconsistencies, and risk indicators that human reviewers might miss across hundreds of vendor assessments. AI agents can compare a vendor’s current responses against their previous submissions, flag significant changes, and automatically re-score risk ratings when new information arrives. More advanced AI systems can parse unstructured evidence like security policies, audit reports, and incident response plans to validate questionnaire claims.
Technical risk ratings (high, medium, low) don’t resonate with executives who think in terms of revenue, profit, and shareholder value. Translating vendor questionnaire findings into financial risk metrics creates a common language between security teams and business leadership. Frameworks like Factor Analysis of Information Risk (FAIR) provide structured methods for quantifying the probable frequency and magnitude of losses from vendor-related incidents.
When you can tell executives that a particular vendor relationship represents $2.3 million in expected annual loss exposure based on their control gaps and your data exposure, you enable risk-informed decisions about vendor selection, contract terms, and mitigation investments.
Elevate Your Vendor Security Program with Data Driven Insights
Vendor security questionnaires have evolved from compliance checkboxes into strategic intelligence tools that drive measurable risk reduction. The organizations seeing the most value from their TPRM programs share common characteristics: they tailor assessments to vendor risk levels, validate responses with external data, automate repetitive processes, and translate technical findings into business metrics that executives understand and act on.
The shift from manual, periodic assessments to continuous, automated risk intelligence represents the future of third-party risk management. SAFE Security’s autonomous TPRM solution powered by Agentic AI transforms vendor security questionnaires from static documents into dynamic risk intelligence. The platform automates questionnaire distribution, uses AI to analyze responses and validate claims against external data sources, and quantifies vendor risk in financial terms using FAIR methodology.
Security teams gain continuous visibility into vendor risk across their entire ecosystem without scaling headcount, while executives receive board-ready reports that demonstrate the ROI of third-party risk investments. The platform’s integration with contract lifecycle management, compliance reporting, and cyber insurance workflows creates a seamless vendor risk program.
Request a demo to see how SAFE TPRM can transform your vendor security questionnaire program into a strategic risk management capability.
FAQs about Vendor Security Questionnaires
How often should I send security questionnaires to vendors?
Assessment frequency depends on vendor risk tier and relationship criticality. High-risk vendors handling sensitive data or providing critical services typically warrant annual questionnaires, while your most critical vendors might require semi-annual assessments. Lower-risk vendors can be assessed every two to three years or when significant changes occur in their service delivery, ownership, or your data exposure.
What’s the difference between a vendor security questionnaire and a vendor risk assessment?
A vendor security questionnaire is one tool used within the broader vendor risk assessment process. The questionnaire focuses specifically on evaluating security controls, practices, and compliance through structured questions. The complete vendor risk assessment incorporates questionnaire results along with other factors like financial stability analysis, business continuity capabilities, geographic and geopolitical risks, regulatory compliance, and contractual protections.
How do I validate vendor questionnaire responses?
Request supporting evidence for critical control assertions—ask vendors to provide recent SOC 2 Type II reports, ISO 27001 certificates, penetration test summaries, or incident response plan documentation. For high-risk vendors, consider supplementing questionnaires with virtual or on-site assessments where you can interview security personnel and review controls firsthand. External validation through security ratings services that continuously scan vendor infrastructure provides independent verification of security posture.



